What is phishing? and How to Create a Phishing Page?

What is phishing? and How to Create a Phishing Page?
Phishing is a kind of social engineering where an attacker sends a deceitful message intended to fool a human victim into uncovering touchy data to the attacker or to convey malicious software on the victim’s framework like ransomware.
Type of Phishing:
- Email phishing
- HTTPS phishing
- Spear phishing
- Vishing
- Smishing
Email phishing:
Email misrepresentation is purposeful trickiness for either close to a home addition or to harm another person through email. Nearly when email turned out to be broadly utilized, it started to be utilized as a way to cheat individuals. Email extortion can appear as a “con game”, or trick
HTTPS phishing:
The hypertext transfer protocol secure (HTTPS) is regularly thought to be a “protected” connection to click since it utilizes encryption to build security. Most real associations presently use HTTPS rather than HTTP since it sets up authenticity. Nonetheless, cybercriminals are presently utilizing HTTPS in the connections that they put into phishing emails.
Spear phishing:
Spear-phishing attacks, phishing attacks are not personalized to their victims. They are usually sent to masses of people at the same time. Spear-phishing attacks target a specific victim, and messages are modified to specifically address that victim, purportedly coming from an entity that they are familiar with and containing personal information. Spear-phishing requires more thought and time to achieve than phishing. Spear-phishing attackers try to obtain as much personal information about their victims as possible to make the emails that they send look legitimate and to increase their chance of fooling recipients.
Vishing:
Vishing is only one type of phishing, which is any kind of message — like an email, text, call, or direct-talk message — that gives off an impression of being from a confided in source, yet isn’t. The objective is to take somebody’s personality or cash. It’s getting simpler to contact more individuals, as well.
Smishing:
Smishing is a type of phishing in which an attacker utilizes a convincing instant message to fool designated beneficiaries into clicking a connection and sending the attacker private data or downloading malicious projects to a cell phone. … fewer individuals know about the risks of clicking joins in instant messages.
The Social-Engineer Toolkit (SET):
The Social-Engineer Toolkit is an open-source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly. SET is a product of TrustedSec, LLC – an information security consulting firm located in Cleveland, Ohio.
How to install Social-Engineer Toolkit?
Step 1: Clone the repository
git clone https://github.com/trustedsec/social-engineer-toolkit/ setoolkit/
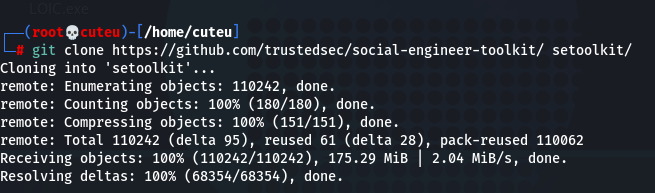
Step 2: Change the directory
cd setoolkit
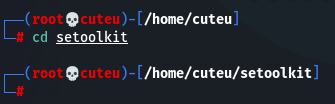
Step 3: Install the requirements
pip3 install -r requirements.txt
![]()
Step 4: Run the setup file with python
python setup.py
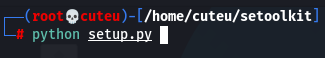
Step 5: Run Social-Engineer Toolkit with type “setoolkit”
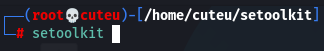
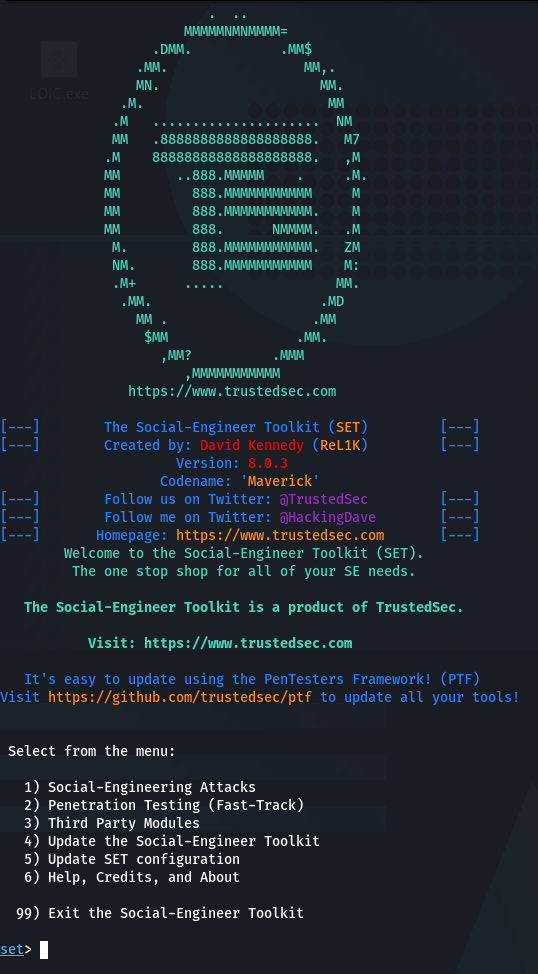
How to create a phishing page with Social-Engineer Toolkit?
Step 1: select 1(Social-Engineering Attacks) from the menu
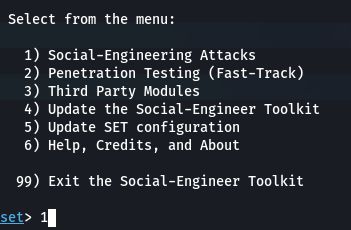
Step 2: Select 2(Website Attack Vectors) from the menu
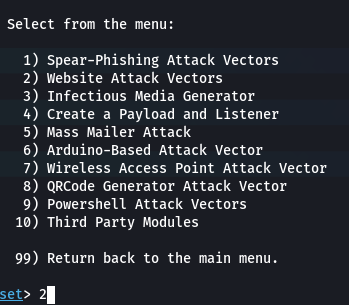
Step 3: Select 3(Credential Harvester Attack Method) from the list
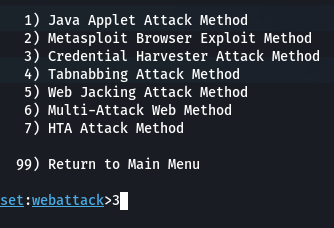
Step 4: Enter your IP address
![]()
Step 5: Select 1(Web Templates) from the list
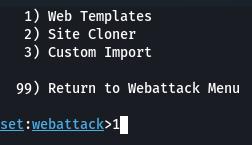
Step 6: Select 2 (Google) from list
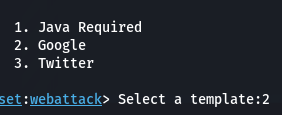
Step 7: Search your IP address on the browser
![]()
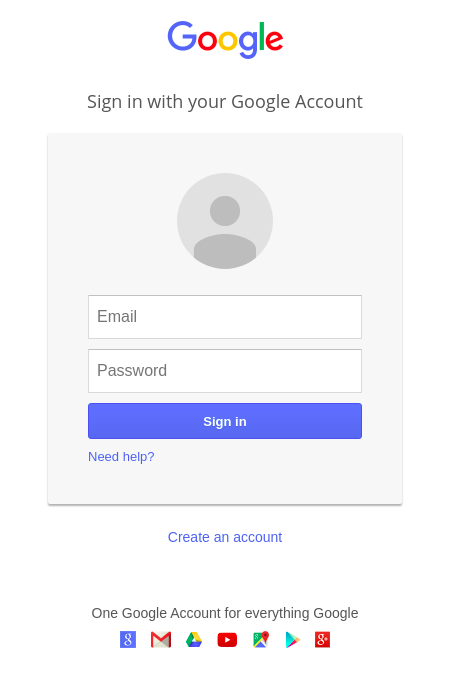
Step 8: enter the username and password
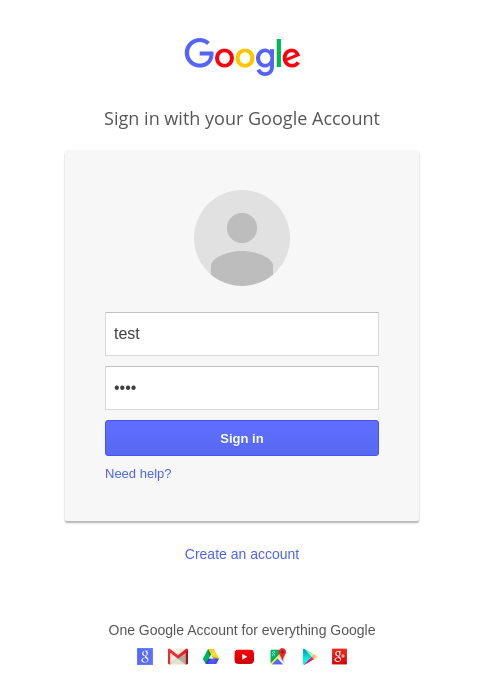
Step 9: you get the username and password
![]()








