What is WAF? and How do bypass WAF with Nmap?

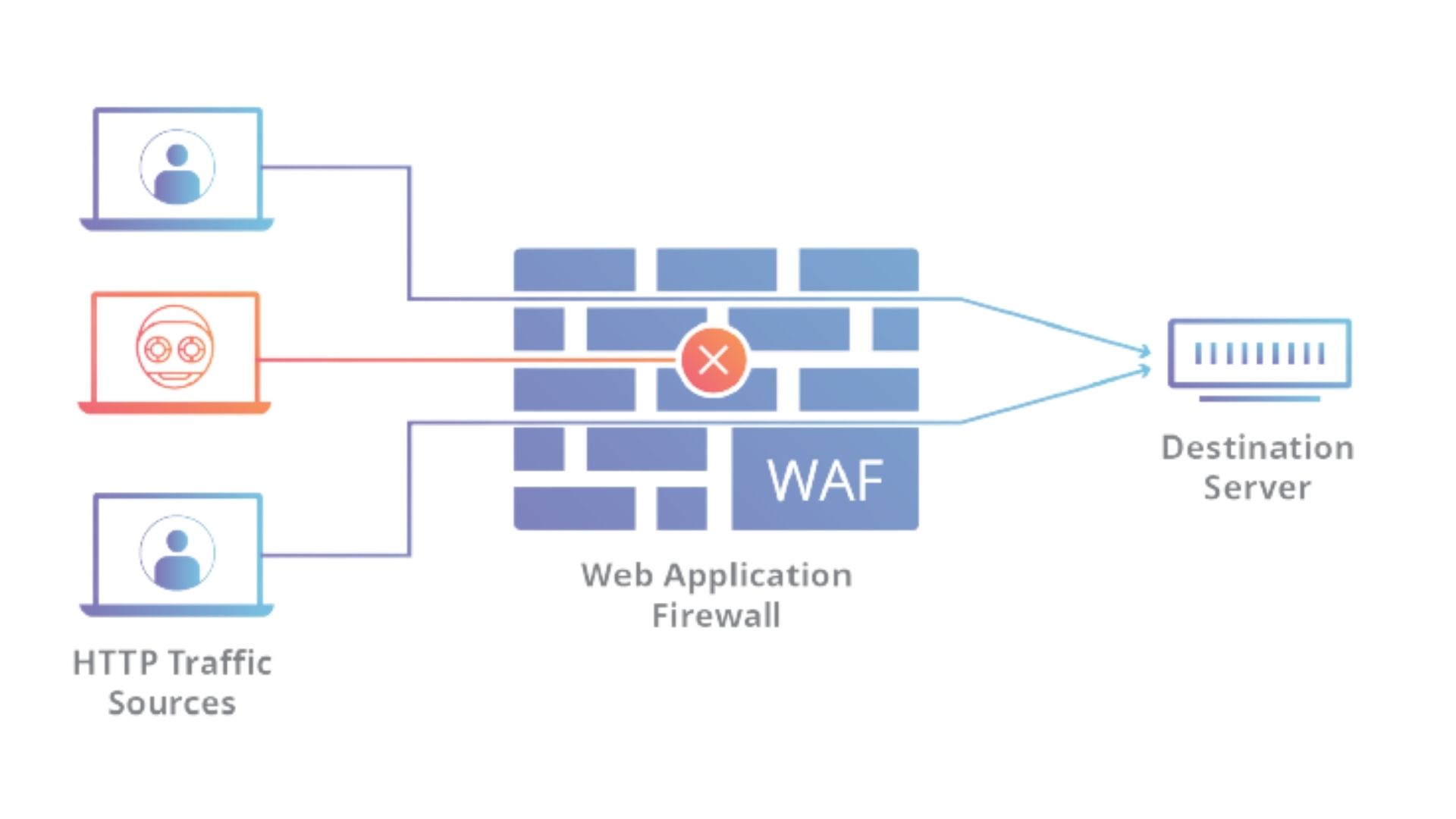
WAF represents a “Web application firewall”. A web application firewall is a particular type of application firewall that filters, monitors, and blocks HTTP traffic to and from a web service. A WAF can be either network-based, host-based, or cloud-based and is frequently conveyed through a converse intermediary and set before at least one site or application.
Type of WAF?
- Network-based web application firewall:
An application firewall is a type of firewall that controls the input/output or system calls of an application or service. - Host-based web application firewall:
Host-based web application firewalls (HWAF) exist as modules for a web server. It is an essentially less expensive arrangement contrasted with equipment-based WAFs, which are intended for little web applications. The greater part of the software WAFs are made to be handily incorporated with mainstream web servers - Cloud-based web application firewall:
One advantage of an unadulterated, cloud-based WAF is that it blocks vindictive traffic sometime before it arrives at your organization. At the end of the day, the WAF fills in as a security edge outside of the interior or cloud framework, assisting with keeping pernicious traffic a protected separation from your application and data servers.
Use of WAF?
- Injection attacks:
Attackers now and then supplement pernicious SQL code into web demands with an end goal to separate information from your database. To permit or impede web demands that seem to contain malevolent SQL code, make at least one SQL injection match condition. A SQL injection match condition recognizes the piece of web demands, for example, the URI or the question string, that you need WAF to assess. Later all the while, when you make a web ACL, you determine whether to permit or hinder demands that seem to contain malevolent SQL code. - Broken Authentication:
For web applications can prompt the openness of undesirable information, taken qualifications or meetings, and pantomime of genuine clients. These defects are hard to moderate utilizing a WAF. - Sensitive data exposure:
application defects are regularly harder to relieve utilizing web application firewalls. These defects ordinarily include encryption measures that have been insufficiently executed. A few models are the absence of encryption on shipped or put away touchy information or utilizing weak heritage encryption figures, where noxious gatherings can block and decode your information. - XML External Entities (XXE):
It permits an aggressor to read delicate data on the webserver. Play out the disavowal of administration assault, etc. Consequently, shield the machine from XXE attacks. Web Application Firewall can shield the apparatus from XXE attacks as long as the substance type is recognized as XML. - Broken Access control:
Application blemishes in this category permit inside web application object to be controlled without the requestor’s entrance consents being appropriately approved. Contingent upon the particular responsibility, this can prompt openness of unapproved data, control of interior web application state, way crossing, and record consideration. - Security misconfigurations:
particularly ones that have a security sway, can occur at any level of your application stack. This can apply to the operating system, middleware, stage administrations, web server software, application code, or database layers of your application. Default arrangements that boat with these parts may not generally follow security proposals or be good for each responsibility. - Cross-Site Scripting (XSS):
Attackers at times embed scripts into web demands with an end goal to abuse weaknesses in web applications. You can make at least one cross-website prearranging match condition to recognize the piece of web demands, for example, the URI or the inquiry string, that you need WAF to review for conceivable malignant contents. - Insecure Deserialization:
Unreliable Deserialization weakness, otherwise called Untrusted Deserialization, is a genuine category of Application Security gives conceivably influencing most present-day systems. … Identified with Struts treatment of XML deserialization, prompts distant execution.
Limitations of WAF:
- They can create false positives and false negatives
- Can easily be break
- 0-Day Exploits
- Costly
Nmap:
Nmap is a free and open-source network scanner created by Gordon Lyon. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service and operating system detection.
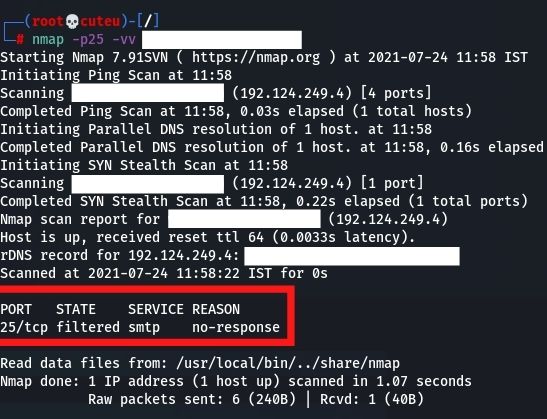
nmap -p25 -vv Hostname
How to bypass WAF with Nmap?
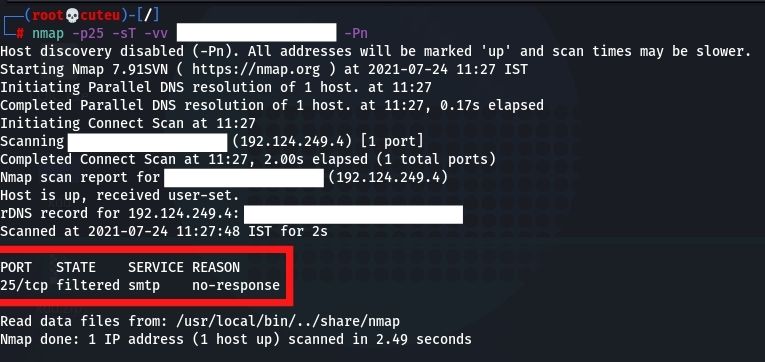
- TCP Connect Scan (-sT)
TCP connect scan is the default TCP scan type when SYN scan isn’t an option. This is the situation when a client doesn’t have crude parcel advantages or is scanning IPv6 organizations.nmap -p25 -sT -vv Hostname
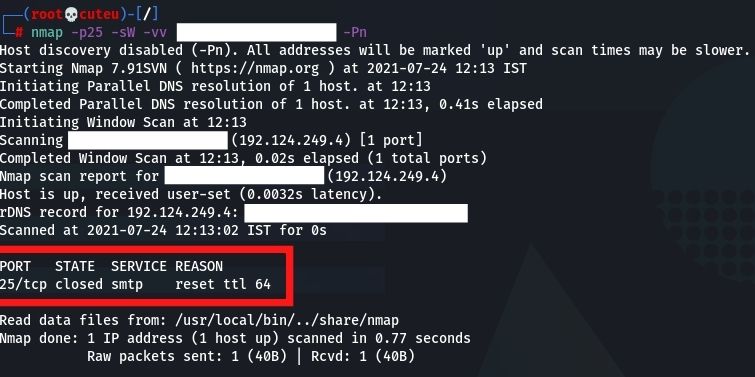
- TCP Window Scan (-sW)
Window scan is actually equivalent to ACK scan with the exception that it misuses an execution detail of specific frameworks to separate open ports from shut ones, instead of continually printing unfiltered when a RST is returned.
nmap -p25 -sW -vv Hostname
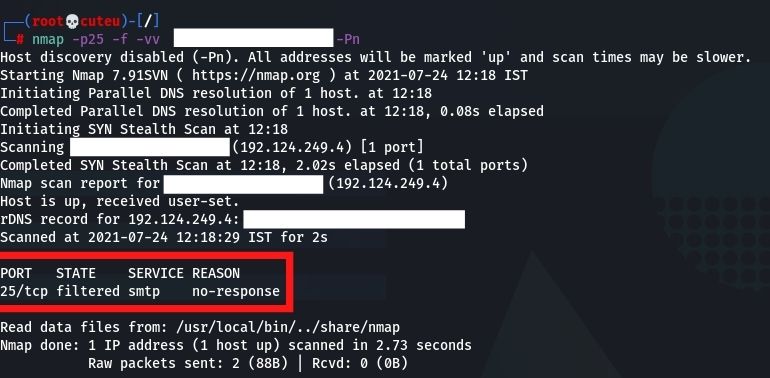
- Fragmentation Scan(-f)
A Nmap scan will utilize little IP fragments if the – f is indicated. Naturally, Nmap will incorporate up to eight bytes of information in each part, so a commonplace 20 or 24 byte (contingent upon options) TCP parcel is sent in three little fragments.nmap -p25 -f -vv Hostname
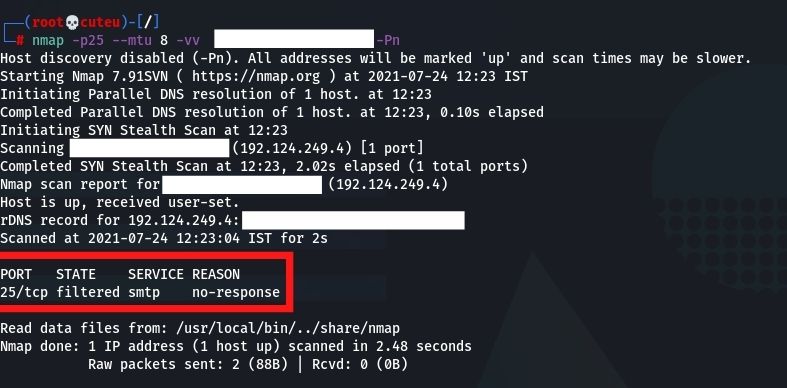
- Maximum Transmission Unit(–mtu)
Nmap is giving the option to the client to set a particular MTU (Maximum Transmission Unit) to the bundle. This is like the parcel discontinuity method. During the scan, Nmap will make parcels with a size-dependent on the number that we will give. In this model, we gave the number 24, so the Nmap will make 24-byte parcels, creating turmoil in the firewall.nmap -p25 –mtu 8 -vv Hostname
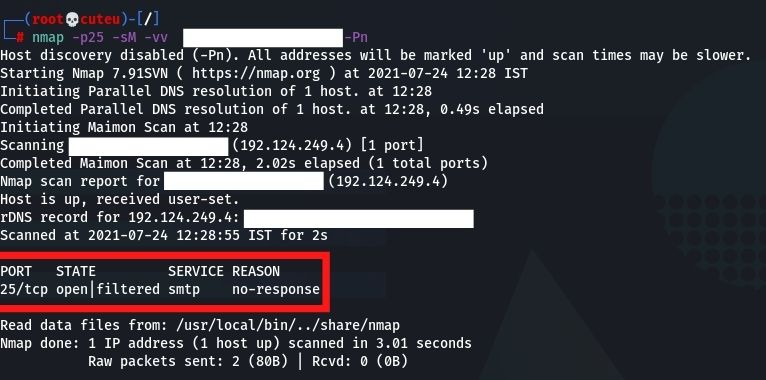
- TCP Maimon Scan (-sM)
The Maimon scan is named after its discoverer, Uriel Maimon. This technique is exactly the same as NULL, FIN, and Xmas scan, except that the probe is FIN/ACK.nmap -p25 -sM -vv Hostname