New Malware Confused Android Device Users in Using Google Play Store

You may have heard of malware’s various behaviors. But have you ever heard of its impersonating other apps on the official platforms where you visit to download a legitimate app for your personal choice? If not, then this is the time you should get accustomed to it, because recently it has been happening over Google Play Store.
This malware is known as “Autolycus”. Usually, every user on Google PlayStore thinks that on PlayStore they are safe and they have nothing to lose. However, nothing is promising and unchangeable in this materialistic world.
Everything has a lifetime period, so be it. Well, if we talk about this malware, we would say that this malware made several people download it even though it passed the trackers of Google Robust Security System.
Don’t know how, but that was terrific. Let’s see the whole story, what it was, and how it happened to people.
Autolycus
To make a big breakthrough this malware impersonated several apps to get people to download as much as possible.
A Security Researcher from Evina Security known as Maxime Ingrao shared a report that says a new malware campaign targeting Android Users, globally. He was the one who named this malware “Autolycus”. This malware ran customized infectious campaigns to impersonate several apps.
It was shocking but as malware, it does a great job impersonating several apps to get ignored by Google Play Store. The appearance of this malware made Google PlayStore make a mistake which unfortunately proved to be disastrous for the global audience.
Luring Users was just a simple trick for this malware, that even the Robust Google Security wouldn’t be able to detect its existence. That means it succeeded in its mission to target the Audience Operating Android Devices.
| Note: We got a suggestion for the users that they must look for the genuineness of the App Developer of the Apps before installing it on their devices, which can be harmful to Confidential Data. |
According to Ingrao….
This malware has had an existence since June 2021 via 8 various Apps. All of them made a grand number of downloads that reached over 3 Million Installs. It reacts as much to show nothing to the user that seems to be suspicious.
The only way it could help the attacker to make money is by subscribing to the premium version of the app to get access to the victim’s bank account. It made its way to withdraw the money from the victim, and the radar wouldn’t be able to catch the attacker’s actions in time.
Then, it is as simple as it seems to be that the victim didn’t make it in time and the attacker got what he’s meant to take with him.
The Process
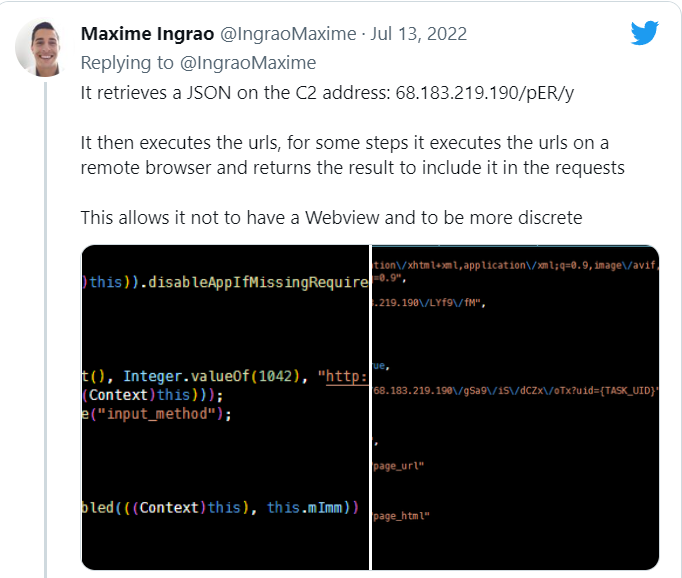
- It gets JSON on C2 address that is: 183.219.190/pER/y
- After that, it executes the URL.
- For some steps, the execution of the URL is done on the remote browser.
- Then it returns the results to be included in the requests.
- This allows it to be more discrete and not a webview.
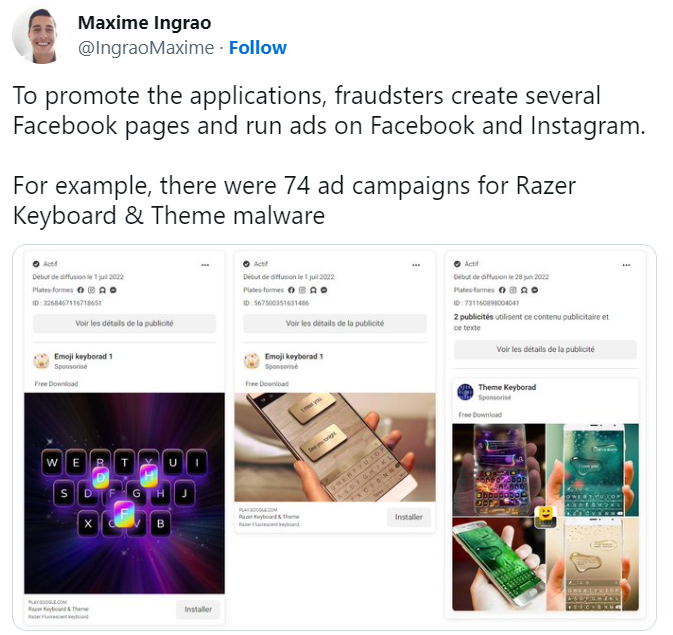
The Cybercriminals behind this whole scenario to make this crime more legitimate created several promotional pages on social media to attract visitors. This made the malicious apps that were distributing the malware look like legitimate apps.
You’ll get more detailed information about the malware in a technical form in the report made by Evina.
The existence of Some Apps is still disturbing.
After the whole mess up, researchers tweeted the list of fabricated apps on Twitter. They also sent a report to Google to take quick action on a serious note.
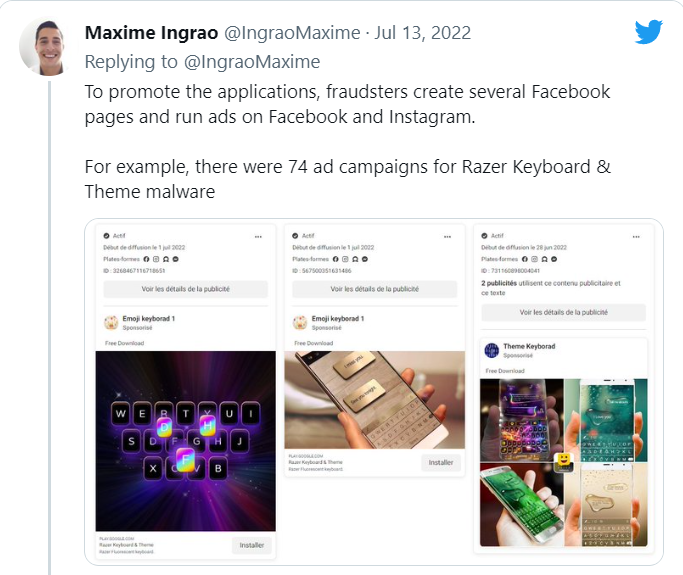
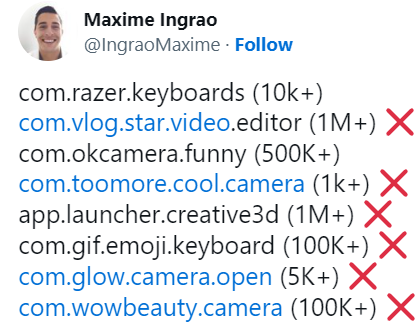
Well, it took a long time to remove the apps from Google Playstore. But still, an app known as “Funny Camera” (com.okcamera.funny) exists on Playstore without any issue.
Well, that’s an annoying thing. Even now, Google Playstore Users have to be careful while using this platform to download apps. Search for a trusted and reliable developer, then you don’t need to be afraid of getting hacked.
Now that you understand the risk of social media and social platforms you should get used to being alert for everything. Well, you do have alternatives apart from being alert, and that is to join a Mobile Application Security Course.
One of the best institutes you can join for this course will be Craw Security. Once you join this institute, you’ll be able to get the best trainers to train you to become a professional like them. Don’t waste your time and get enrolled now!
Kindly read more articles :
OpenSSL Update is in Severe Conditions due to Implications in its Service