WoofLocker Toolkit Runs Tech Support Frauds by Hiding Malicious Codes in Images

An upgraded version of WoofLocker, a powerful fingerprinting and redirection toolset designed for tech support frauds, has been described by cybersecurity researchers.
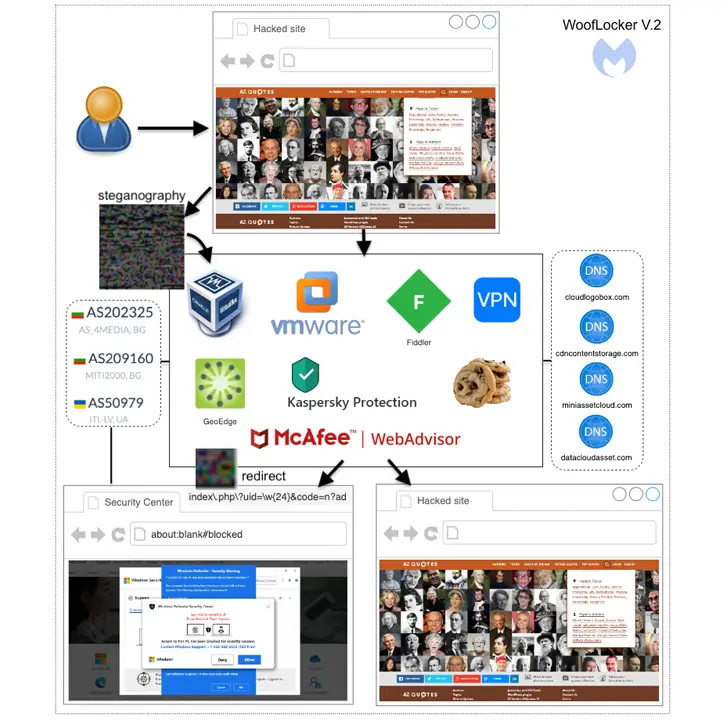
In order to deliver advanced JavaScript that drives users to a browser locker (also known as a browlock), the complex traffic redirection strategy first became known by Malwarebytes in January 2020. It takes advantage of JavaScript hidden in hacked websites to carry out anti-bot and web traffic monitoring checks.
In turn, this redirection mechanism employs steganographic techniques to cloak the JavaScript code inside a PNG image that is only delivered after the validation process has been completed. A fake PNG file without the dangerous code is employed if a user is identified as a bot or has uninteresting traffic.
WoofLocker is also known as 404Browlock since a 404 error page appears when the browlock URL is accessed immediately without the proper redirection or one-time session token.
According to the most recent study by the cybersecurity company, the campaign is still active.
According to Jérôme Segura, director of threat intelligence at Malwarebytes, “the strategies and methods are remarkably comparable, but the system in place is now stronger than before to prevent potential takedown attempts.”
“It is similarly hard to replicate and analyze the rerouting process now as it was then, particularly in view of fresh fingerprinting checks” to identify computer systems, certain extensions for browsers, and security tools.
Most of the websites running WoofLocker are adult-oriented, and the network is powered by hosting companies in Ukraine and Bulgaria that provide threat actors with more robust takedown defenses.
Browser lockers’ main objective is to induce their intended victims to call for help with (fake) computer issues. Once in remote control of the computer, they can then create an invoice advising the victims that they must pay for an antivirus program to fix the issue.
In 2020, Segura stated, “This is handled by third parties via bogus call centers.” The threat actor is responsible for the traffic redirection, and the browlock will be compensated for each lead that is successful.”
Although the threat actor’s precise identity is still unknown, there are indications that the campaign’s planning began as early as 2017.
WoofLocker is a very solid and low upkeep business, in contrast to other efforts that rely on buying ads and performing whack-a-mole with hosting companies and registrars, Segura added. In contrast to the fingerprinting and browser locking infrastructure, which appears to be utilizing reliable registrant and hosting companies, the websites hosting the malicious malware have been infiltrated for years.
The revelation coincides with the company’s description of a new malvertising infection chain that involves the use of false search engine advertisements to drive customers looking for remote access tools and scanners to websites that have been duped into deploying stealth malware.
The campaign in question is unique in that it can identify visitors by their browser fingerprints using the WEBGL_debug_renderer_info API to collect the graphics driver properties of the victim and separate real browsers from crawlers and virtual machines before exfiltrating the information to a remote server to decide the next step.
Threat actors can make sure their dangerous ads and infrastructure are available online for a longer period of time by employing better filtering before sending people vulnerable to malware, according to Segura. “It likely affects takedown actions, as well as making it harder for defenders to recognize and report such events.”
The incident also comes in the wake of a recent study that revealed that over the previous five years, websites belonging to American government agencies, prestigious institutions, and professional groups had been taken over and exploited to spread phony deals and incentives via “poison PDF” files submitted to the portals.
Many of these con games target kids and try to get them to download malware and apps or give out personal information in exchange for fake incentives on websites like Fortnite and Roblox.
About The Author:
Yogesh Naager is a content marketer that specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article Here:
Karnataka Congress Website got hacked by 4 Hackers: Hosting Spoof Site
Citrix ShareFile flaw added by CISA to KEV Catalog as a result of In-the-Wild Attacks.









