WiKI-Eve – Eavesdropping on Keystrokes to Steal Wi-Fi Passwords

Mobile devices and apps are becoming increasingly important in user identification, yet password theft, like identity theft, encourages a wide range of eavesdropping assaults, including covert indirect ones via side channels.
Indirect attacks, such as those that use side channels (acoustic, electromagnetic, and so on), pose more dangers by predicting passwords without observing the target panel.
Mentioned cybersecurity researchers have found out a new way to exploit and steal Wi-Fi passwords via eavesdropping on keywords, known as “WiKl-Eve”:
- Jingyang Hu (Hunan University, China)
- Hongbo Wang (Nanyang Technological University, Singapore)
- Tianyue Zheng (Nanyang Technological University, Singapore)
- Jingzhi Hu (Nanyang Technological University, Singapore)
- Zhe Chen (Fudan University, China)
- Hongbo Jiang (Hunan University, China)
- Jun Luo (Nanyang Technological University, Singapore)
Wi-Fi Passwords by Eavesdropping
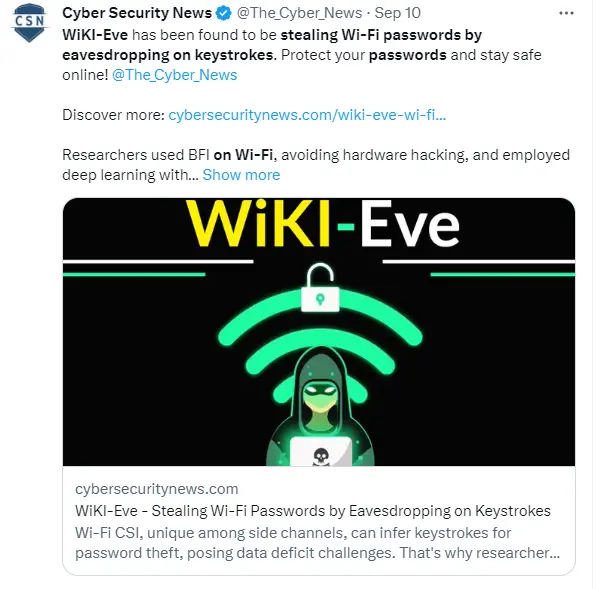
Wi-Fi CSI provides data shortage issues because it is the only side channel that may infer keystrokes for password theft. In order to circumvent BFI variations and steal numerical passwords, researchers devised WiKI-Eve.
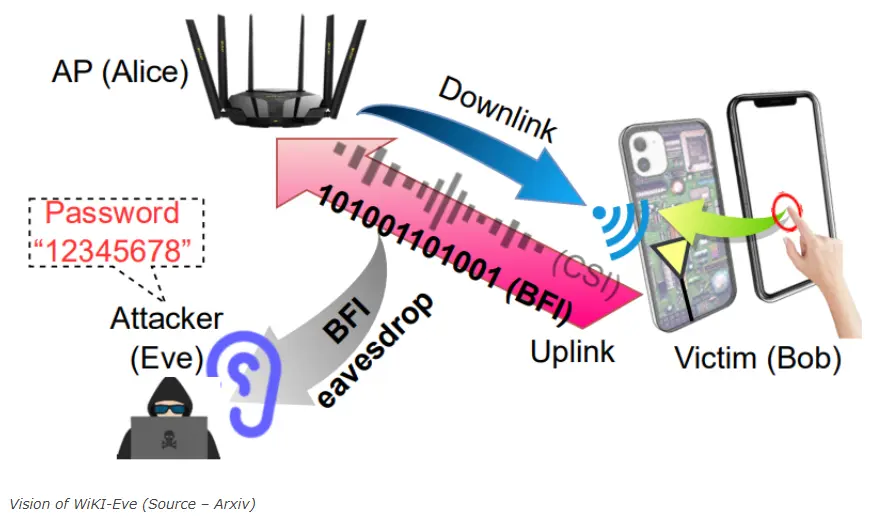
To prevent hardware hacking, cybersecurity experts deployed BFI on Wi-Fi. For keystroke inference in WiKI-Eve, they used deep learning with adversarial training to ensure viability with minimal data and overcome data deficiency.
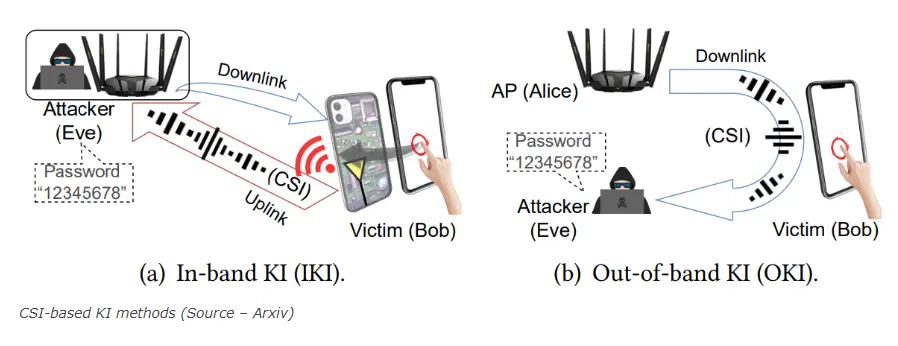
Following are the 2 CSI-based Kl methods that one can use:
- In-band KI (IKI)
- Out-of-band KI (OKI)
Due to Android’s constraints, security experts conducted tests using a laptop (Acer TravelMate with Intel AX210 Wi-Fi NIC). They used Wireshark in monitor mode to record BFIs, ran analyses in Matlab and Python with PyTorch, and then posted their data and preprocessing code online for everyone to see.
Keystroke classification accuracy and top-N password inference accuracy are two metrics used by security analysts to assess. Correct keystrokes are measured by keystroke accuracy, whereas a candidate password’s top-N probability match with the real password is determined by top-N accuracy.

Micro-benchmarks are used by experts to first illustrate WiKI-Eve’s building blocks, after which they assess overall performance and usability. Actual tests reveal that WiKI-Eve is capable of capturing WeChat Pay passwords and applying them to QWERTY keyboards.
In a real-world experiment, they use Bob (the victim) to conduct a transaction using an iPhone 13 in a 5 m x 8 m conference room, with Eve listening in from a distance of 3 m, to show the viability of WiKI-Eve.
Although WiKI-Eve can be directly defended against by encrypting data transmission, this can complicate systems with high user dynamics. The complexity is shifted to users through keyboard randomization and indirect protection, but it may cause problems for people who rely on muscle memory to enter passwords.
With its broad application and lack of hacking or specialist hardware requirements, WiKI-Eve is a flexible Wi-Fi KI assault. Its adversarial learning is transferable to unexplored domains.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Read More Article Here:
U.K. and U.S. Sanction 11 Members of the Russian Cybercrime Organization TrickBot