Top 10 Filters of Wireshark Packet Analysis Program
Top 10 Filters of Wireshark
Wireshark is a network packet analyzer tool, and it is a free and open-source packet analyzer software. It is used for network troubleshooting, analysis, software and communications protocol development, and some projects. A network packet analyzer presents captured packet data in as much detail as possible.
You could think of a network packet analyzer as a measuring device for examining what’s happening inside a network cable, just
However, with the advent of Wireshark, that has changed. Wireshark is available for free is open source and is one of the best packet analyzers available in today’s world.
Features of Wireshark
· Available for UNIX, LINUX, and also for Windows.
· Capture live packet data from a network interface.
· Open files containing packet data captured with tcpdump / WinDump, Wireshark, and many other packet capture programs.
· Import packets from text files containing hex dumps of a packet data.
· Display packets with very detailed protocol information.
· Save packet data captured.
· Export some or all packets in a number of the capture file formats.
· Filter packets on many criteria.
· Search for packets on many criteria.
· Colorize packet display based on filters.
· Create various statistics, and much more.
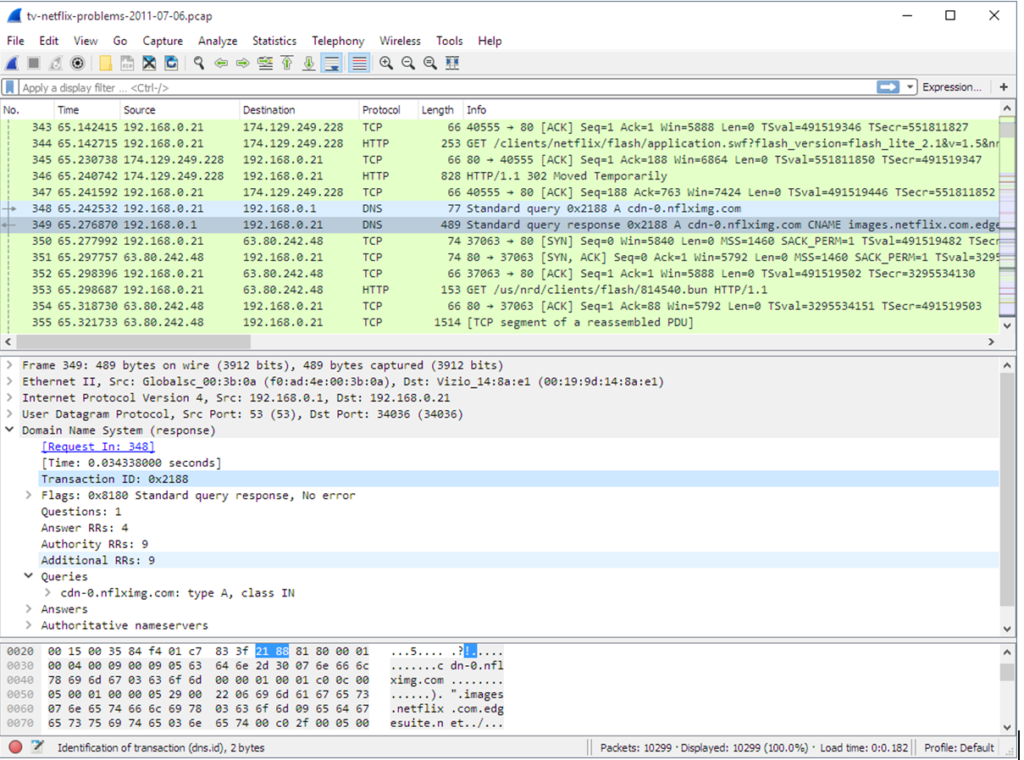
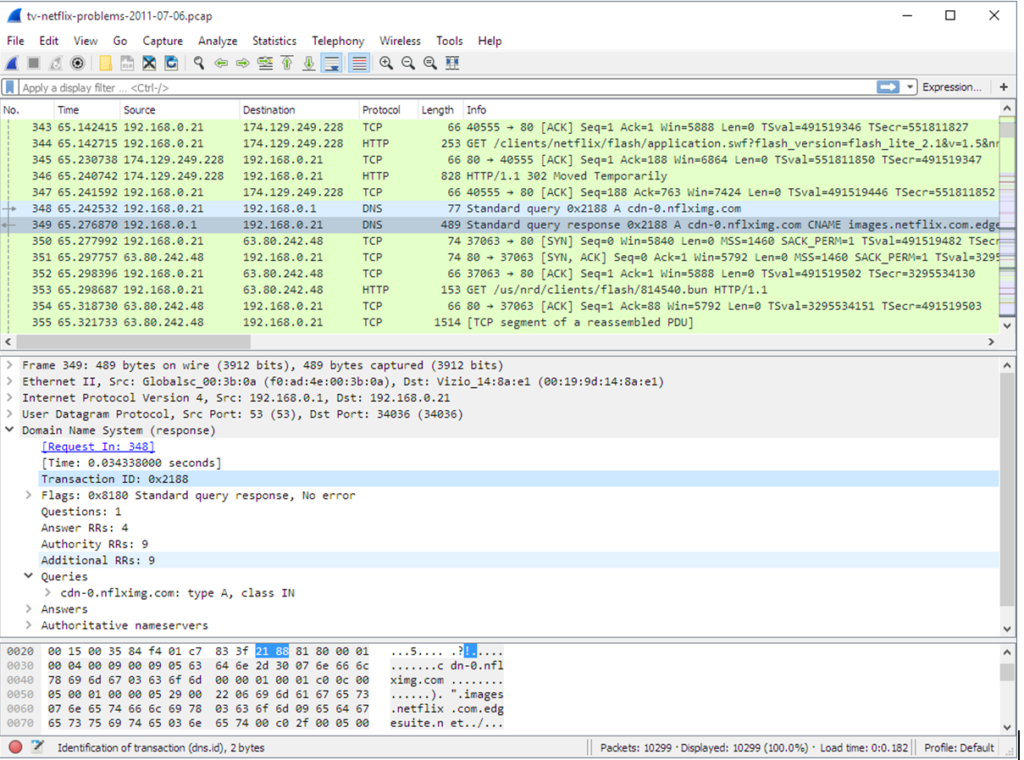
Top 10 Filters of Wireshark
1. ip.addr == 10.0.0.1 [Sets a filter for any packet with 10.0.0.1, as either the source or destination], You can also choose to use ip.dst == x.x.x.x to filter only by destination
or ip.src == x.x.x.x to filter by source.
2. ip.addr ==10.0.0.1 &&ip.addr==10.0.0.2 [sets a conversation filter between the two defined IP addresses]
3. TCP.time_delta> .250 [sets a filter to display all TCP packets that have a delta time of greater than 250mSec in the context of their stream. Note, this filter requires TCP Conversation Timestamps to be calculated. To learn to do that, click here.]
4. TCP.port ==4000 [sets a filter for any TCP packet with 4000 as a source or dest port]
5. tcp.flags == 0x012 [displays all TCP SYN/ACK packets – shows the connections that had a positive response. Related to this is tcp.flags.syn==1]
6. ip.addr == 10.0.0.0/24 [Shows packets to and from any address in the 10.0.0.0/24 space]
7. a frame contains traffic [displays all packets that contain the word ‘traffic’. Excellent when searching on a specific string or user ID]
8. !(arp or ICMP or stp) [masks out arp, ICMP, stp, or whatever other protocols may be background noise. Allowing you to focus on the traffic of interest]
9. eth[0x47:2] == 01:80 [This is an example of an offset filter. It sets a filter for the HEX values of 0x01 and 0x80 specifically at the offset location of 0x47]
10. tcp.analysis.flags&& !tcp.analysis.window_update [displays all retransmissions,