3 Top Crypto Firms Experience Data Breach Due to Kroll SIM-Swapping Attack

Data breach victims were contacted by cryptocurrency companies, including FTX, BlockFi, and Genesis, after a sim-swapping attack on Kroll, a company that offers services and digital products for valuation, governance, risk, and transparency.
Following a SIM-swapping attack on the renowned risk and financial advising firm Kroll, three significant cryptocurrency companies, FTX, BlockFi, and Genesis, are dealing with the fallout from a sophisticated data breach. These companies are BlockFi, Genesis, and FTX.
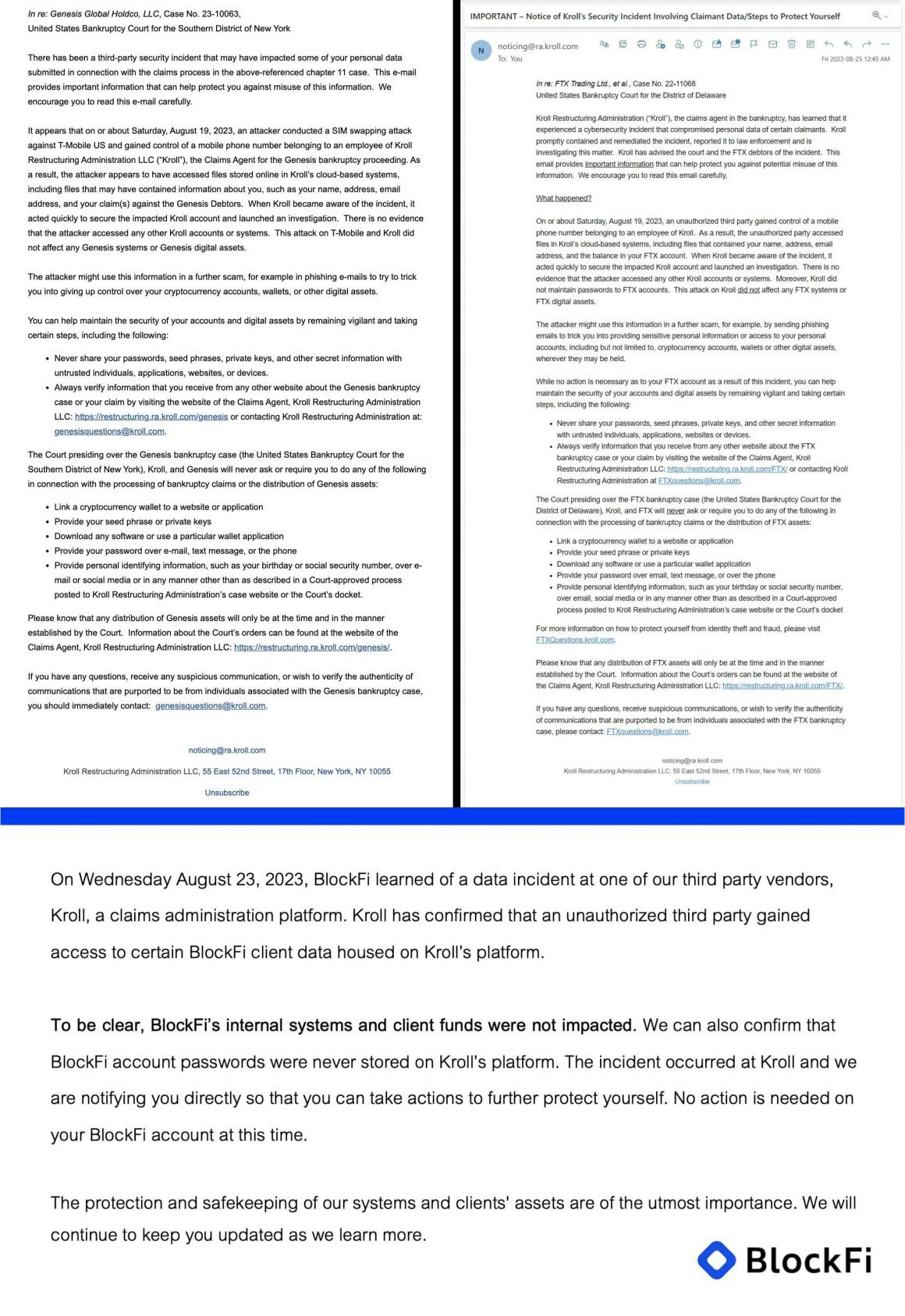
On August 19, 2023, Kroll received word that a threat actor had used a well-planned SIM-swapping assault to take advantage of a T-Mobile account owned by one of the company’s workers.
In this kind of attack, adversaries trick cell providers into porting a victim’s phone number to a new SIM card under their command. In this instance, the attacker successfully accessed private data held on Kroll’s computers, notably files containing information about individuals who had filed for bankruptcy in instances involving FTX, BlockFi, and Genesis.
This breach has had a huge effect. Both FTX and BlockFi notified their consumers of the incident right away. Users should rest assured that account passwords and digital assets were untouched by the disclosure made by FTX, which indicated that the exposed information contained customer names, addresses, email addresses, and account balances. BlockFi mirrored the sentiment and warned its users about a probable rise in spam phone calls and phishing attempts due to the hack.
Kroll quickly secured the hacked accounts and, working with the FBI, launched an inquiry into the event. There are worries that the stolen data may be used in phishing attempts, even though the impacted organizations have stressed that the security of their systems and digital assets remains intact.
Phishing emails urging users to withdraw money from their accounts have been reported by users of these platforms, showing that fraudsters are already seeking to take advantage of the situation.
Although not new, SIM-swapping assaults continue to be a formidable weapon in the armory of hackers. Attackers can successfully avoid multi-factor authentication and take over numerous accounts linked to a victim’s phone number by taking control of it.
The potential of SIM-swapping attacks rises as more organizations and people use mobile phone numbers for account recovery and verification.
Reduce reliance on SMS-based authentication, look into alternatives to providing phone numbers for account registration, and regularly review and update account recovery methods to include security keys or mobile authentication apps, according to cybersecurity experts.
Kroll, a provider of services and digital products for valuation, governance, risk, and transparency, apologized for any inconvenience and reaffirmed its commitment to information security and protection in a statement. Kroll also stressed its commitment to protecting customers, partners, and the larger community.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.





