1,00,000 ChatGPT A/cs stolen, caused breaches on Dark Web

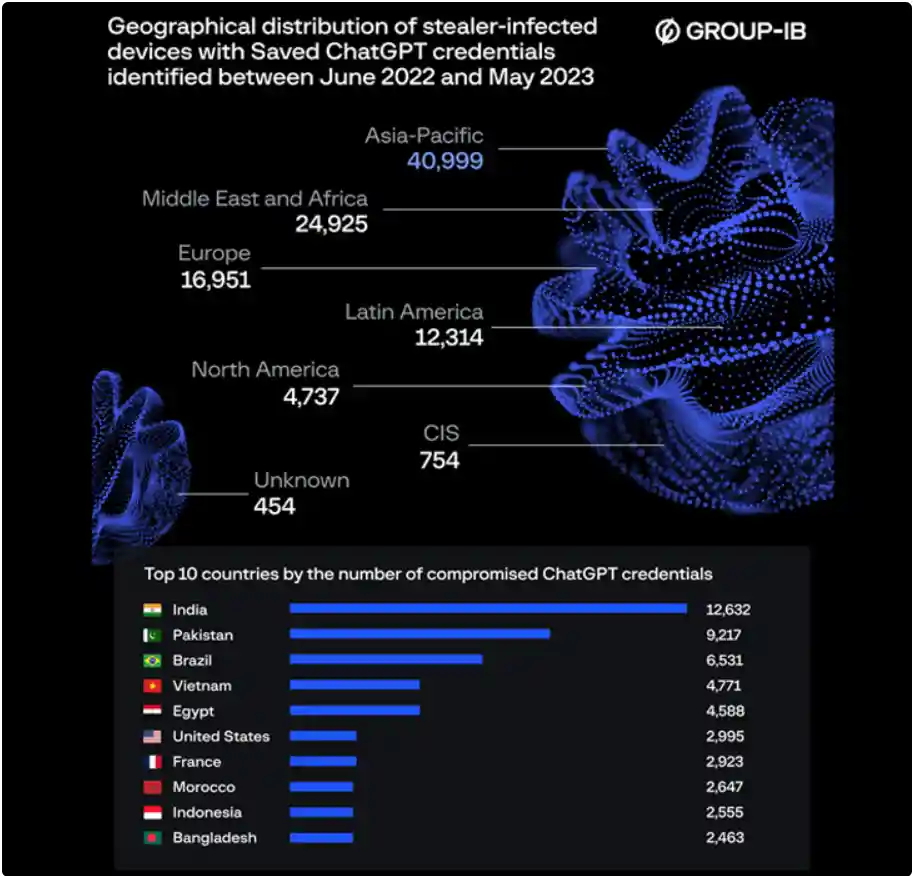
Between June 2022 and May 2023, over 101,100 victimized OpenAI ChatGPT accounts’ data were sold on Dark Web, with 12,632 of those credentials coming from India.
Group-IB
Sensitive data were breached within data stealer logs made available for sale on the cybercrime platform. “Logs containing compromised information harvested by info stealers are actively traded on dark web marketplaces.”
Dmitry Shestakov, (head) Threat Intelligence, Group-IB
“Many enterprises are integrating ChatGPT into their operational flow.”
The corporation’s headquarters in Singapore reported that “the contacts of available logs containing victimized ChatGPT A/cs reached a peak of 26,802 in May 2023.” The biggest number of ChatGPT credentials sold over the past year has been in Asia-Pacific.
Pakistan, Brazil, Vietnam, Egypt, the United States, France, Morocco, Indonesia, and Bangladesh are other nations where the most compromised ChatGPT credentials have been found.
Further investigation has shown that the notorious Raccoon adversaries (78,348), followed by Vidar (12,984) and RedLine (6,773), have compromised the majority of logs holding ChatGPT accounts.
Due to their skills to steal passwords, cookies, credit card numbers, and other data from browsers & cryptocurrency wallet extensions, adversaries have become popular among cybercriminals.
The lists of websites detected in the log and the information on the infected host’s IP address are further details about logs offered on such markets.
Not only they lowered the bar attack, but they also acted as a conduit for launching follow-on attacks utilizing the siphoned credentials. They are often offered based on a subscription-based pricing model.
Employees can utilize the bot to optimize their proprietary code or enter confidential correspondence. Given that ChatGPT’s default setting saves all discussions, threat actors could unintentionally gain access to a wealth of important information if they manage to get account credentials.
Users should adhere to good password hygiene practices and secure their accounts with two-factor authentication (2FA) to reduce these risks and guard against account takeover threats.
The development takes place during an ongoing malware campaign using pornographic content lures and phony OnlyFans pages to spread the DCRat (or DarkCrystal RAT), a modified variant of AsyncRAT, a remote access trojan, and an information stealer.
eSentire Analysts
The activity has been ongoing since January 2023. “In observed cases, victims were trapped into downloading ZIP files containing a VBScript loader which ran manually,” they stated.
The victims may have been drawn in by explicit images or OnlyFans content for different adult film stars, according to the file naming convention.
It also comes in the wake of the discovery of a brand-new VBScript variant of the malware GuLoader (also known as CloudEyE), which uses decoys themed around taxes to start PowerShell scripts that can retrieve and inject the Remcos RAT into a genuine Windows process.
Canadian Cybersecurity Company
“GuLoader is a highly evasive malware loader commonly used to deliver info-stealers and Remote Administration Tools (RATs).”
GuLoader uses shortcut files or user-initiated scripts to run highly obscured commands and encrypted shellcodes. As a result, a legal Windows process is hosting a memory-resident malware payload.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Kindly read other news articles:
A Cyberattack caused a data breach at new BreachForums in which 4,000 members were victimized.
Russian Ransomware Group Launched A Series of Cyberattacks on Federal Agencies of the US