Microsoft Discover Severe ‘One-Click’ Exploit for TikTok Android App

Several Apps are now being targeted to be the bearer of malicious content every day. Attackers find several ways to take advantage of App loopholes that can be exploited with some simple techniques that the Attackers know.
Similarly, TikTok… Aah! Right! TikTok which has been banned in India is in the spotlight due to a malicious vulnerability, recently.
On Wednesday, Microsoft announced that there was a high severity vulnerability in a certain version of the TikTok App (Android). Attackers could get access to the accounts of victims just after the victims click on the malicious link created by the attackers.
Fortunately, the vulnerability has been patched since the bug was found and reported early.
Dimitrios Valsamaras, Microsoft 365 Defender, Research Team
“Attackers could have leveraged the vulnerability to hijack an account without users’ awareness if a targeted user simply clicked a specially crafted link,”
Well, if we look at the reactions of the sources then we would say, even though the loophole was discovered a bit late, it was still drastic for those whose IDs were hacked.
The most the attacker could harm was by modifying the posts and content on the victim’s profile and DM others blatantly. But let us see what was the process and how the attacker managed to play that malicious trick on victims.
Consequences of the Malicious Link
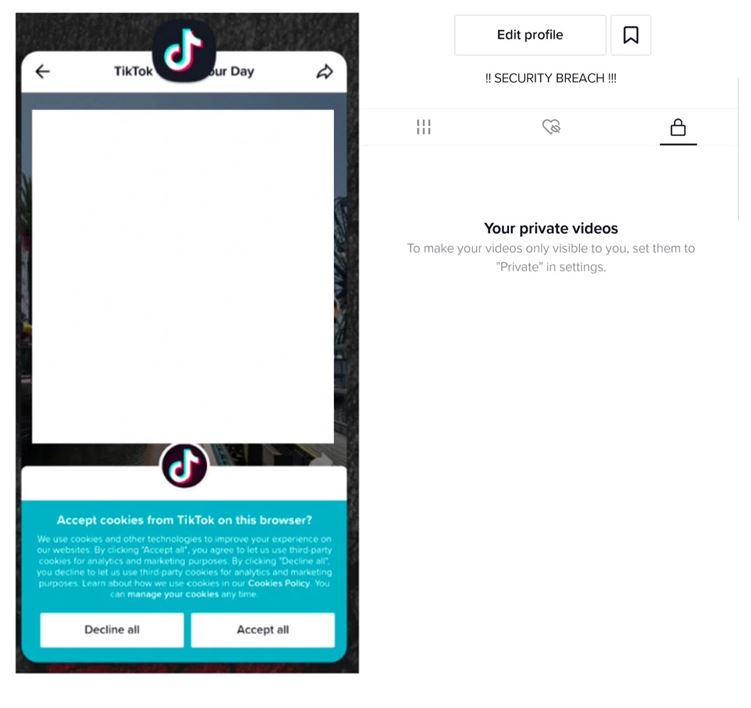
After the exploitation, malicious actors could access and modify users’ TikTok profiles and sensitive data. That led to the unauthorized upload of private videos. Attackers could abuse the bug to send msgs and upload videos in place of users.
Versions affected by this Attack
TikTok’s version 23.7.3 was the one affected by this attack. Moreover, the impact was put on two variants of the App that were
- ss.android.ugc.trill (for East & Southeast Asian users)
- zhiliaoapp.musically (for users except for India).
The total number of downloads from both apps was 1.5 Billion + installations. That’s not a small count to be avoided. If you look at it carefully then you can guess how many accounts could get compromised. Researchers addressed that vulnerability as CVE-2022-28799 and got a CVSS score of 8.8.
Process of Attack
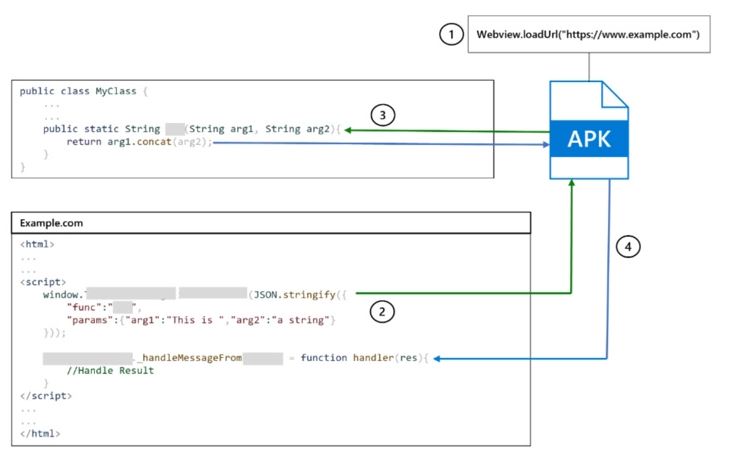
- The app mainly used a deeplink (customized link) to take advantage of the app’s vulnerability.
- It allows apps to open a specific resource within another app that is installed on the victimized device.
- Rather than taking users to a website it uses the link to move the victim from one place to another.
- The crafted URL is an unvalidated deeplink especially customized to force the zhiliaoapp.musically WebView to load an arbitrary website.
- It allows attackers to get access to JavaScript Interface to fully control the features of the victim’s account within a single click.
- Due to the flaw in the app the app’s restriction doesn’t allow any untrusted host and loading any website which seems to be fishy won’t work as usual.
- Moreover, the attacker will be able to cross the app’s restriction and could load any website of his/ her choice via Android System WebView. WebView is a system to display web content on other apps which are simply going to react as it is designed.
- The reason behind the customization of this is to target WebView into loading rogue websites.
- That could permit the attackers to invoke 70+ exposed TikTok Endpoints.
Valsamaras, Static Analysis
“The filtering takes place on the server-side and the decision to load or reject a URL is based on the reply received from a particular HTTP GET request,”
| Note
● “It is possible to bypass the server-side check by adding two additional parameters to the deeplink.” ● “Microsoft– From a programming perspective, using JavaScript interfaces poses significant risks.” ● “A compromised JavaScript interface can potentially allow attackers to execute code using the application’s ID and privileges.” |
The attack could effectively compromise a user’s profile integrity which is very dangerous in every sense because it could lead to so many things that can put the victim’s data or user’s reputation in danger. Moreover, evidence that could prove the wild use of the bug has not been found.
You should be aware of any suspicious links that you might get on social media platforms when surfing the web. Don’t just swiftly move your fingers on that link. First, you must be clear about the motive of that sender that premeditatedly sent you that link to accomplish some indecent goal. Learn, Research, Grow.
Watch more latest news :
Latest Open Source Bug Bounty Projects Launched by Google to Control Supply Chain Attacks
Akasa data hacked, airline asks customers to be ‘vigilant against possible phishing attempts’