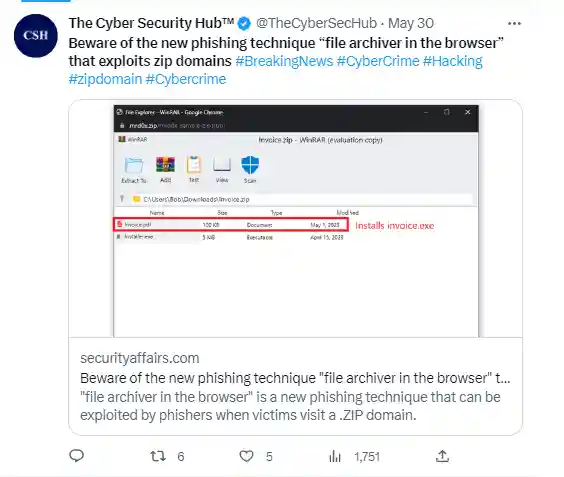
A new phishing method called “file archiver in the browser” that makes use of zip domains should be avoided.

When users visit a .ZIP domain, scammers can take advantage of the “file archiver in the browser” phishing method.
When the target hits a .ZIP domain, scammers can employ a novel phishing tactic termed “file archiver in the browser” to “emulate” a file archiver program in the web browser. The fresh assault method was described by security researcher mr.d0x.
Google introduced 8 fresh top-level domains (TLDs), including .zip and .mov, in May 2023. Several security specialists have issued a warning about fraudulent apps on these addresses.
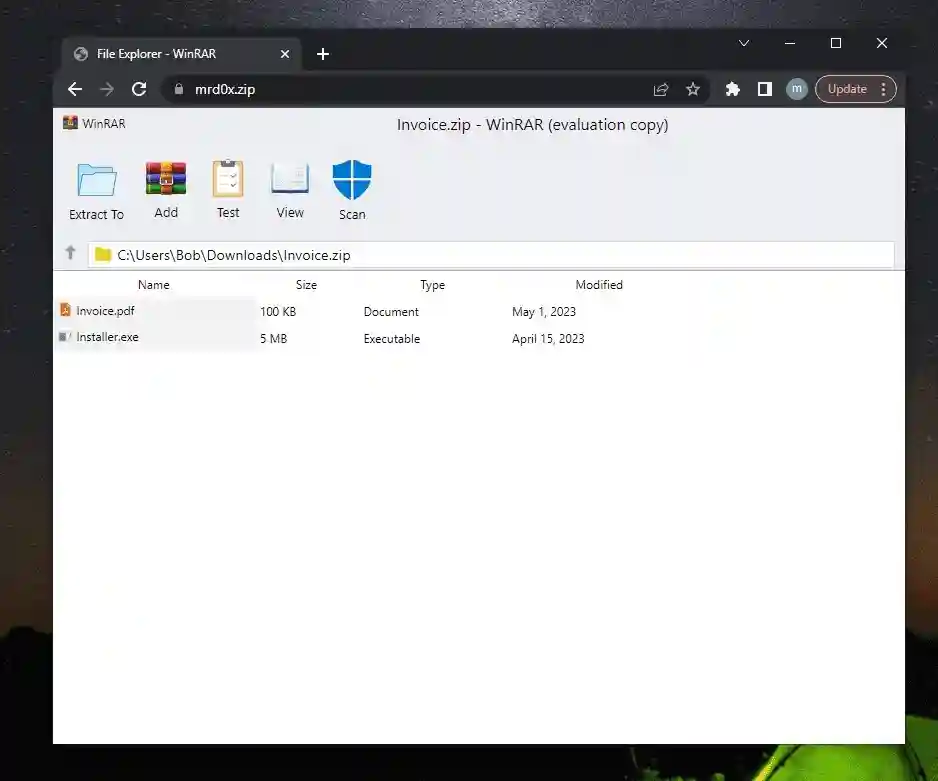
Using HTML/CSS, the assailant must simulate a file archive software in order to execute an attack utilizing this method. Two samples were provided by the researchers; one imitates the WinRAR file archiver, and the other the Windows 11 File Explorer interface.
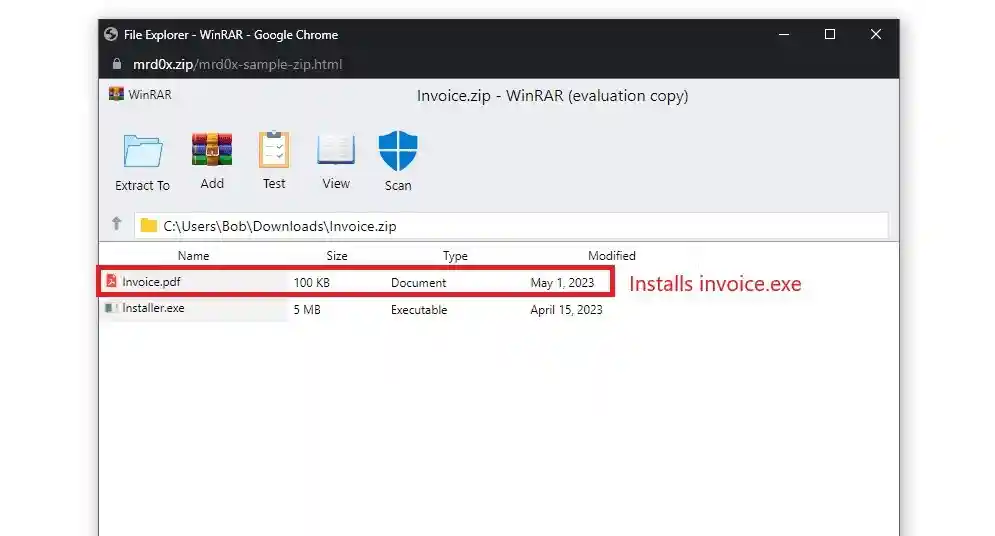
The researchers inserted a “Scan” indicator into the WinRAR sample using a clever method, as shown in the figure below. Users are assured that the data are secure when they tap on the icon, removing any room for skepticism.
The sample was then set up on a .zip domain, which can be leveraged in a variety of exploitation situations, including the following:
- Send viewers to a landing page designed to capture the victim’s login information whenever an attachment is clicked.
- Present a file that can be executed with a bogus extension to trick the visitors. Visitors who click on what looks to be a .pdf document — for instance, “invoice.pdf”—download an executable file instead.
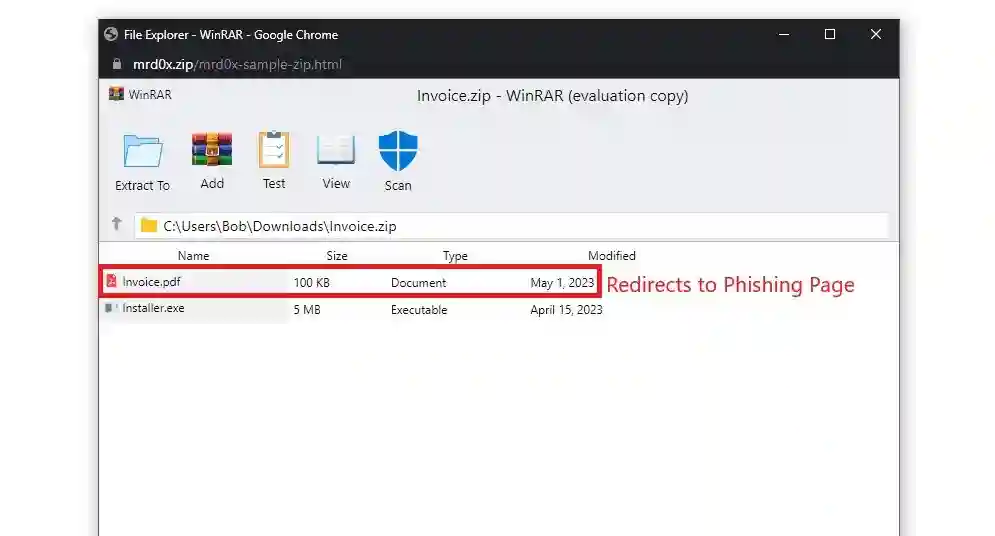
The researcher observed that a large number of Twitter users highlighted the Windows File Explorer search function as a convincing distribution mechanism.
“The Windows File Explorer search bar is an excellent distribution vector, as several users noted on Twitter. The web browser will instantly open whenever an individual searches for mrd0x .zip, and it doesn’t exist on the system. Given the fact that the user would be anticipating observing a ZIP file, this is ideal for the situation,” reads the report that Mr. D0x released.
The latest TLD launches give hackers greater chances to conduct phishing campaigns. To prevent being a victim of these attacks, it is imperative to be aware of this assault tactic.
Businesses are being urged to put restricting procedures in place for the .zip and .mov domains since phishers are already using them maliciously and are likely to continue doing so.
The expert continues, “It’s strongly advised for organizations to block .zip and .mov addresses as they have already been utilized for phishing and will probably just keep continuing to be utilized more frequently.”
About The Author:
Yogesh Naager is a content marketer specializing in cybersecurity and B2B. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Kindly read another article:
Tambaram police warn smartphone users to prevent falling victim to a Telegram fraud.
Data Theft Reported When Sysco Hit By Cyberattack
RSAC 2023 Revealed 10 Innovative and Amazing Cybersecurity Tools