CISA added 7 new flaws to its Known Exploited Vulnerabilities Catalog

The Cybersecurity and Infrastructure Security Agency (CISA) from the U.S. added 7 latest issues to its unleashed Exploited Vulnerabilities Catalog.
Researchers are always in the search for options to evade issues erupting from the loopholes in the networks and systems that we use. So, what’s now? Did we get something new? Or is it just some daily news Pop-Ups? No, today, this news will amaze you because CISA has identified several flaws, in a catalog that records exploited vulnerabilities.
This week, CISA introduced seven new flaws and recorded them in the records along with other Exploited Vulnerabilities of their Catalog. That included a critical SAP Security Vulnerability observed as CVE-2022-22536.
On Thursday, CISA added a critical SAP security flaw to its Catalog containing Exploited Vulnerabilities. Moreover, that is based on the evidence of active exploitation.
One of those risks got the highest rating score of severity which is 10.0 on the CVSS Vulnerability Scoring System. That is CVE-2022-22536. On Tuesday this vulnerability was identified by SAP as part of its Patch updates for February 2022.
The catalog has some additional flaws included:
| S.No. | Code | Issues |
| 1. | CVE-2022-32893 | Apple iOS and macOS contain an out-of-bounds write vulnerability that can get access to adversaries to remotely execute code execution when running maliciously crafted web content. |
| 2. | CVE-2022-32894 | Apple iOS and macOS contain an out-of-bounds write vulnerability that could allow an app to run code with kernel privileges. |
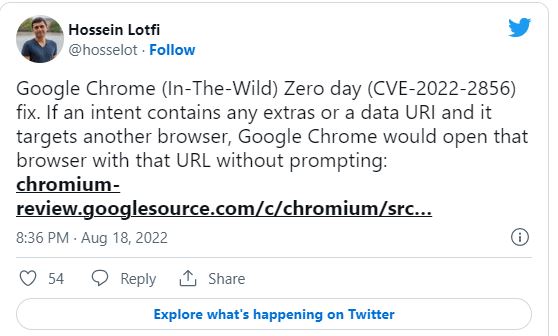
| 3. | CVE-2022-2856 | Google Chrome Intents allow for insufficient validation of untrusted input, causing unknown results. CISA will update this explanation if more data becomes available. |
| 4. | CVE-2022-21971 | Microsoft Windows Runtime contains an unspecified vulnerability that allows remote code execution. |
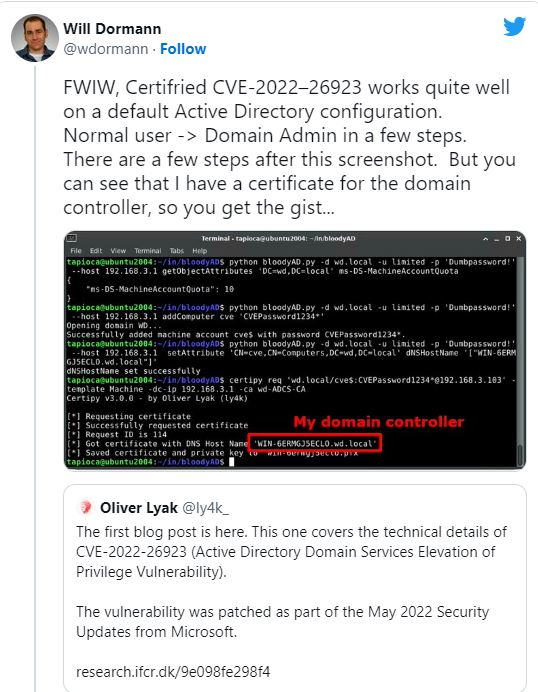
| 5. | CVE-2022-26923 | A valid user could change attributes on PC A/Cs they own/ manage and keep a certificate from Active Directory Certificate Services that would allow for privilege escalation to the system. |
| 6. | CVE-2017-15944 | Palo Alto Networks PAN-OS contains multiple, unspecified vulnerabilities which can allow for remote code execution when chained. |
Binding Operational Directive (BOD) 22-01:
Reducing the Significant Risk of already unleashed Exploited Vulnerabilities, FCEB organizations need to identify the identified loopholes by the due date to secure their networks against attacks that exploit the flaws in the mentioned catalog.
Advice from Experts
Private Organizations must review the Catalog and consider the loopholes in their infrastructure, and management. CISA orders federal agencies to patch these vulnerabilities by September 8, 2022. As a professional in the industry, you should be careful of the things that may worry you for a long time if avoided. Always look for the latest updates in Cyber Security Tech News. Learn, Research, and Grow!
Watch more News here :