1,900 Phone Numbers of Signal Users Accessed in Phishing Attack

You may know about Signal, one of the most secure messaging platforms that’s famous for its end-to-end encryption policy said-
Earlier this month, 1,900 Users’ phone numbers might have got exposed in a phishing attack on Twilio Inc,. Twilio is Signal’s SMS Verification Services Provider.
Tweet, Monday
Signal claimed this Monday, “Data in attackers’ possession could allow them to try out to register a Signal user’s phone number on a new device. That’s possible only, if that user had not enabled the registration lock,”. Might look safe, but what guarantees that the users might not face any drastic consequences?
“Via Twilio, attackers may have accessed phone numbers & SMS registration codes for 1,900 Signal users,”
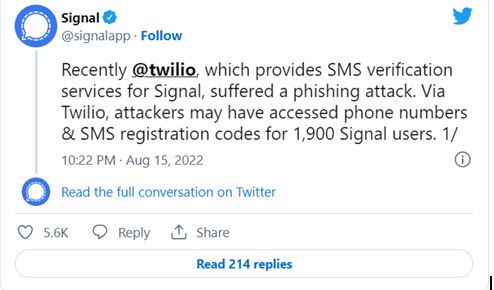
However, according to Signal, an attacker isn’t capable of accessing messaging history, profile information, contact lists, and other data, yet in any condition and won’t be. That’s just a superstition. This is one of the major phishing attacks tried on online platforms. But for those who don’t know what a phishing attack is, can understand via the below content.
What is a Phishing Attack?
It’s a common type of cyber attack that involves sending fraudulent messages which appears to be a genuine message dropped by a reputable source via emails. These emails are customized differently on the basis of the victims and their systems.
Sometimes attackers do a lot of research to analyze victim’s actions and choices over the internet to interpret what they are in search of. That helps the attackers to customize the emails according to the search of victims’ needs. The one “n” only goal of attackers is to steal confidential data such as credit card & login info/ to install malware on the victim’s device.
Watch Related news here : Click here Now!
Twilio Suffered
04, Aug, is the day, when Twilio disclose the matter of phishing attack via a blog post that gives full information that how the attacks was proceeded, and how it got into the observation of Twilio.
SMS verification partner wrote
“Twilio became aware of unauthorized access to information of its customer accounts through a sophisticated social engineering attack designed to steal employee credentials. This broad- based attack against our employees succeeded in fooling some employees into providing their credentials,”.
Twilio said…
- Attackers used the breached data to gain control of Twilio’s internal systems to get certain clients’ data.
- It also notified the aggrieved customers
- Twilio was working with customers as part of an ongoing investigation.
Twilio, Cybercriminals of Modus Operandi
“Our current and former employees recently reported receiving text messages purporting to be from our IT Department. The text bodies suggested the employee’s passwords had expired, or their schedule had changed, and they needed to log into a URL the attacker controls.”
To trick victims into clicking on a link impersonating Twilio’s sign-in page, attackers made the URLs with the use of words such as:
- “Twilio,”
- “Okta,”
- “SSO”
Signal, Twitter
“We are prompting them [the affected users] to re-register their Signal numbers and encouraging them to enable registration lock. We are also working with Twilio to ensure they upgrade their security practices,”
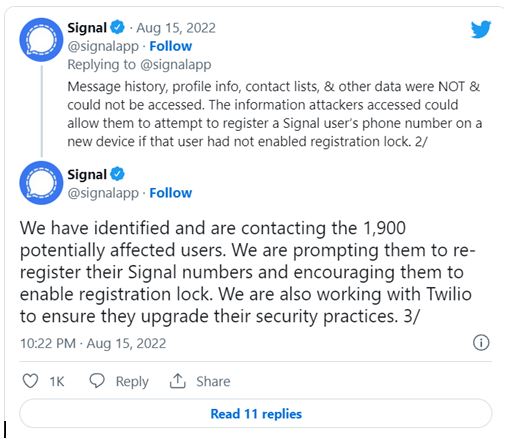
Twilio Claims
It claimed in its posted blog that the messages originated from US carrier networks, which were eventually shut down. Well, if we took some steps on how to click on unofficial links, we can avoid getting in trouble because of such apps and websites.
However, as a social media user you should learn about the cybersecurity, and the effects of clicking such unusual and unauthenticated apps/ website’ link. Therefore, you’d be able to make yourself more secure and safe.
Watch more news here:
Zoom rolls out key Security updates on Mac to prevent hackers from gaining device control





