Data on Twitter of millions of people was stolen in a drift

How is it possible that someone could easily draw information from a secured application or website? Do they have no strong secured databases, or do they let their guard down when dealing with their user’s ID? Nothing like that. Then what happened? Let’s continue…
Attacker draws the data related to millions of people.
According to a Report, Jan 2022
Hacker was admitted to have found a vulnerability. That vulnerability could be exploited to get a Twitter Account via the details related to the users such as:
- Phone No.
- Email address
Moreover, this could be done even if the user uses the prevention option in the privacy settings of his/ her account. This loophole allows anyone to get a Twitter ID without any authentication process. In exchange, it only demands the contact no., or email ID of the original users.
The existence of this bug happened to be possible due to the authentication process in the Android Client of Twitter. This could happen if anyone tries to check the duplicity of a Twitter Account. You can read the whole process via the report submitted by Zhirinovsky on a bug bounty platform “HackerOne”.
| Serious Note
On a serious note, this is not an easy bug to identify in the first place. But the most irritating part of this case is that not only the attacker could find the user who restricted searching them via their phone number/ email ID, but also could cite a big load of data related to Twitter User Base with a little bit of scripting/ coding. This kind of collection can be put on sale for cybercriminals for promotion motives, or for attacking any famous celebrity for a specific purpose. |
After Zhirinovsky found this bug and reported it to the Twitter Security Management Team confirmed the vulnerability with a security check, he got the bounty money worth $5,040. This load of data was first observed by Restore Privacy on Breached Forums.
Twitter Account Data on Auction worth 5.4 Millions
Data on auction was containing data related to several Celebrities & Companies that have a reputation in the industry, worth millions. Moreover, the data was including Emails and Phone numbers of the personal. During this sale the attacker also shared a csv file (Comma-separated values) containing the sample of the data.
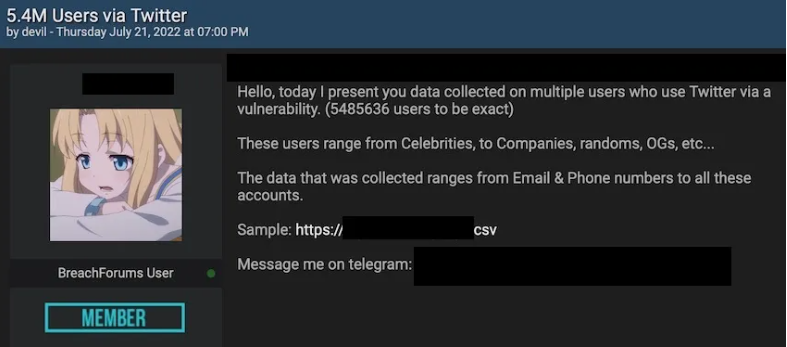
Some hours later, the post reached the owner of Breach Forums. First, the owner decided to verify the legitimacy of the leak. After that, it was proved to be true that the data was leaked due to the vulnerability in the security management of Twitter. It was in the report of HackerOne.
This attack has to be one of the biggest data breaches in the history of data breach. The data involved nothing less than everything. Attacker also demanded $30,000 for the whole Database.
On 24 July, 2022 the hacker revoked the ad from the breach forum.
Conclusion
Well, whatever the case was, this was a big mistake of Twitter that it let this loophole open for the attackers. However, if you want to secure yourselves from such incidents you can learn how to manage your security over online apps that collect data.
For that, you can join a Mobile Application Course that will introduce you to several techniques and tools. If you want to get the guidance of best trainers to train you through and through you can contact Bytecode India.
Bytecode has been in the market of Cyber Security for a long time. Therefore, you’ll get the best training and the chance to ask for online sessions. What are you waiting for? Enroll, Now!
Kindly read more news :
Will the cloud be able to help India’s conditions in employment by the end of 2022?
Maui Ransomware has made several targets since March 2021





