Crypto Wallets targeted by access to FB Business A/cs via NodeStealer 2.0

A new Python variant of NodeStealer is found out, which can easily take illicit access over FB Business A/cs & Crypto Wallets.
A recent unreported phishing event was found out by Palo Alto Network Unit 42, which shared the Python Variant of the NodeStealer.
The specially customized malicious code was designed to illegitimately access Facebook Business Accounts & steal funds via cryptocurrency wallets.
From Dec, 2022, it has been observed by professionals that adversaries have targeted FB business A/cs with phishing techniques via offering tools such as business spreadsheet templates.
Nodestealer ( Data Stealing Malware) was shared on Meta, allowing breaching browser cookies to access A/cs on various platforms, including.
- Facebook,
- Gmail, and
- Outlook.
In late Jan, 2023, this malware was seen while attacking the browsers of Windows systems. Moreover, it can attack several web browsers, including.
- Google Chrome,
- Microsoft Edge,
- Brave, and
- Opera.
In May, Meta found this variant which is a Javascript malware, to bundle the Node.js environment.
Developer used Node.js to run malware execution on various OS, including
- Windows,
- Linux, and
- macOS.
This Info Stealer has a Vietnamese Origin & was continuously shared by adversaries from Vietnam. In May, FB took action to stop the malware event & help victims in recovering their A/cs. But, the new event includes 2 variants coded in Python enhanced with more features to facilitate adversaries.

Palo Alto Networks, Analysis
The adversary used these variants with crypto-stealing facilities, downloading facilities, and FB business A/cs accessing capabilities.
The NodeStealer seems to be more fatal for people & the firm. It can breach sensitive data from browsers that can be utilized for future attacks.
In the phishing message, a link was attached that highlighted a .zip archive uploaded on a known cloud file storage provider like – Google Drive. The .zip file was loaded with the malicious infostealer executable.
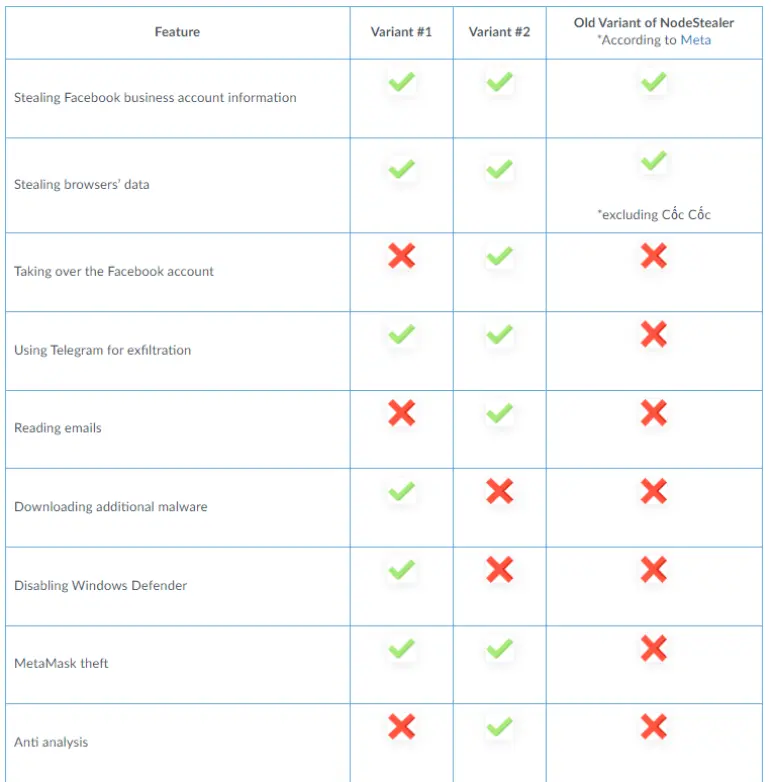
Palo Alto Networks observed a variant that supports various features, such as
- Breaching FB Business A/c data,
- Download more Malware,
- Disable Windows Defender through GUI & steal money from the MetaMask Cryptocurrency Wallet utilizing stolen data from the following browsers.
- Google Chrome,
- Edge,
- Cốc Cốc,
- Brave, and
- Firefox Web Browsers.
After running the malware, it assesses the FB Business A/c logged in to the default browser on the targeted device by connecting to https://business.facebook.com/ads/ad_limits/ and assessing the header.
If it is logged in, the malware connects to the Graph API graph.facebook.com via the User ID & the access token is breached from the header.
If the account is prepaid & ads data, NodeStealer will breach the following data about the victim.
- Followers Count,
- User Verification Status, and
- Account Credit Balance.
Unit 42 found out that NodeStealer’s 2nd variant has more facilities, such as
- Parsing Emails via Microsoft Outlook,
- Data Exfiltration via Telegram,
- Taking over the Facebook Account, and
- Anti-Analysis Capabilities.
Differences between the 2 Variants:
Report
The two variations’ analysis revealed some interesting malware behavior, including doing much more than its original intentions, which is likely to increase the potential profit for the threat actor.
Adversaries, supposed to be Vietnamese, offer the new variations access to downloaders, the capacity to steal cryptocurrency, & full control over FB business A/cs.
The potential damage for both persons and firms can be shown not just in money loss but also in reputation damage for a target.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Read More Article Here:
A superstar was called a Womanizer by Kangana Ranaut and has been accused of hacking her A/c
Sonu Nigam Calls Attention to Online Fraud and Discloses Fraudsters Using His Name!