Everything about Nmap | The Network Mapper
Everything about Nmap | The Network Mapper
Nmap is a free, open-source network scanner. It is created by Gordon Lyon. Nmap provides various features like scanning hosts, probing networks, host discovery, OS detection, and services running on the system. Nmap is also available in a graphical interface named Zenmap. Nmap detects the host and the services in the network by sending packets and analyzing the responses. Nmap is a Network mapper tool. Nmap scans the ports on the machine to detect the running service on the port. Nmap was written using C, C++, Lua, and python. Nmap can be more aggressive by using scripts to extends its power and capabilities that provide more advanced service detection, vulnerability detection, and other features. Nmap was initially started on Linux but nowadays it can be also used on other platforms like Windows and macOS.
Features of Nmap:-
- Host discovery
- Port scanning
- Service version detection
- OS detection
- Advanced Scripts
- TCP/IP stack fingerprinting
Host Discovery ——————-à
Nmap is a network tool that aids in host finding. Nmap mentions the hosts that respond to TCP/ICMP requests.
Port Scanning ——————-à
Nmap enumerates the open ports on the target.
Service version detection
——————————–à
It can detect the service name and its version.
OS detection
—————–à
Nmap can detect the OS running on the target machine.
Advance Scripts ——————–à
The addition of advanced scripts to Nmap makes it more capable and powerful for advanced vulnerability identification and other types of scanning.
TCP/IP stack fingerprinting
———————————-à
By observing network activities, Nmap detects the target’s operating system and hardware specifications. User interface
Nmap is available in both a command-line interface (CLI) and a graphical user interface (GUI) (GUI). The graphical version is known as Zenmap.
Uses of Nmap:–
1.Network mapping
2.Firewall detection
3.Network auditing by detecting servers on the network
4.To generate traffic to the host
5.To find and explore vulnerabilities
6.DNS query and subdomain search
Nmap gives you four different output formats to choose from. Nmap is a popular tool used by network admin to map their networks.
Nmap has two modes of operation: basic and advanced. In the ordinary, we utilize simple commands, but in the advanced, we must use scripts to increase its capabilities. Nmap can scan both large and small networks with ease.
Types of scans
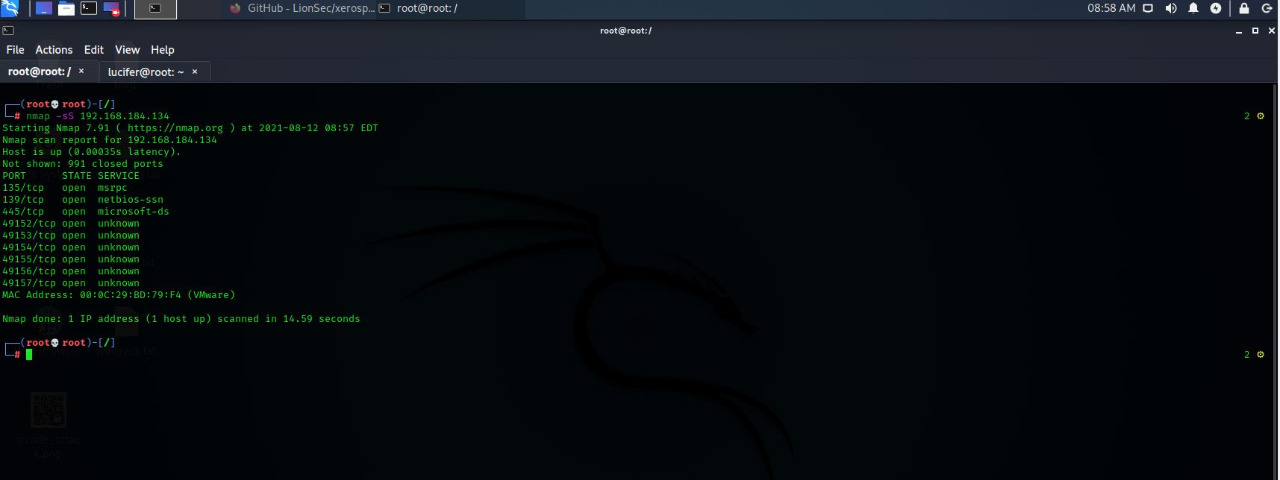
- Network Specific Scan
#nmap 192.168.0.1-255
#nmap 192.168.0.1/24
**From a text file
#nmap -iL <IP Address list path>
STATE –> 1. OPEN
- CLOSED
- FILTERED
FILTERED|OPEN
FILTERED|CLOSED
- Target Specific scan
#nmap <IP Address Of The Target>
#nmap <IP Address range> –exclude <IP Not To Scan>
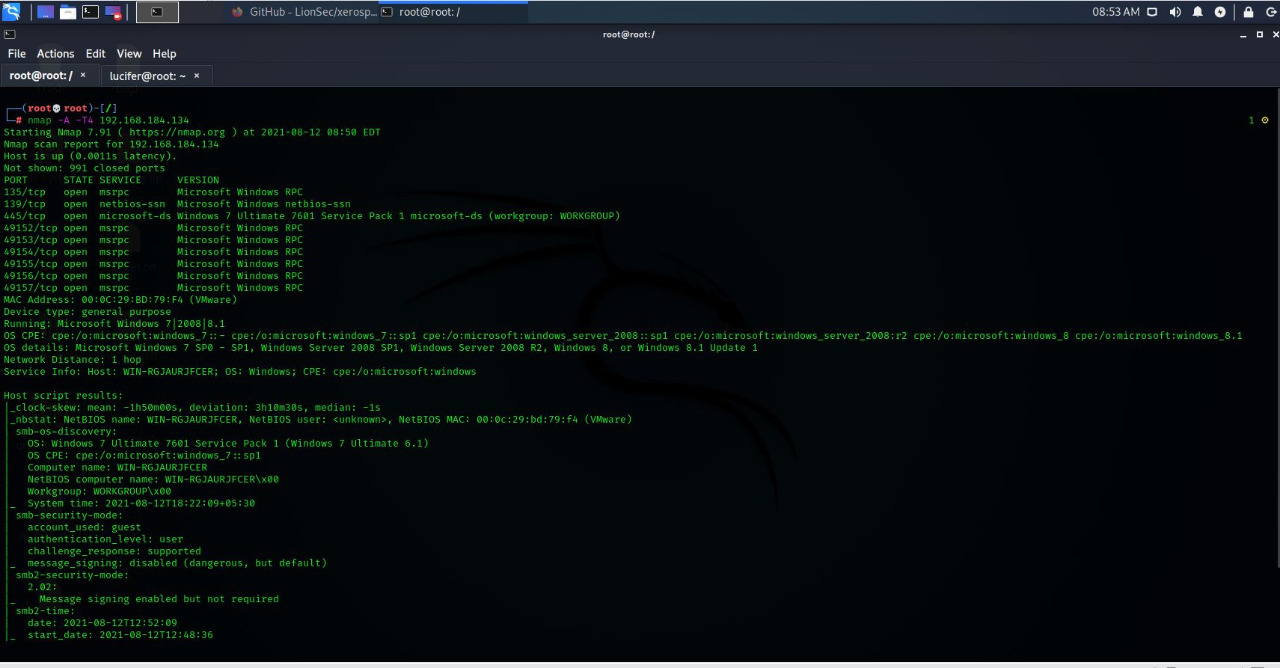
- Agressive Scan
#nmap -A -T4 <IP Address Of The Target>
A –> Agressive Scan
T –> Time Duration between sending 2 consecutive packet
4 –> 4 unit of time(sec)
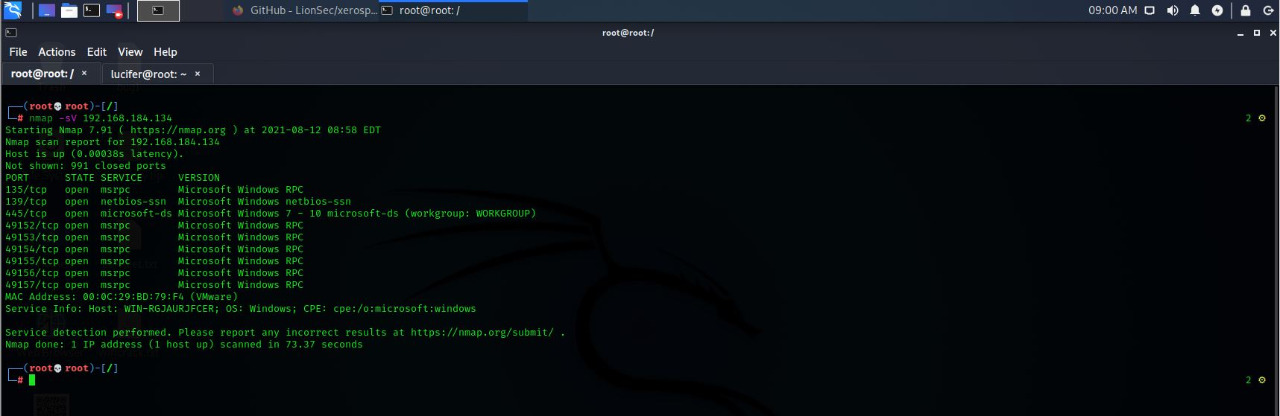
- Service Detection Scan
#nmap -sS 192.168.0.189 s –> Script
S –> Service Detection

- Version Detection Scan
#nmap -sV <IP Address>

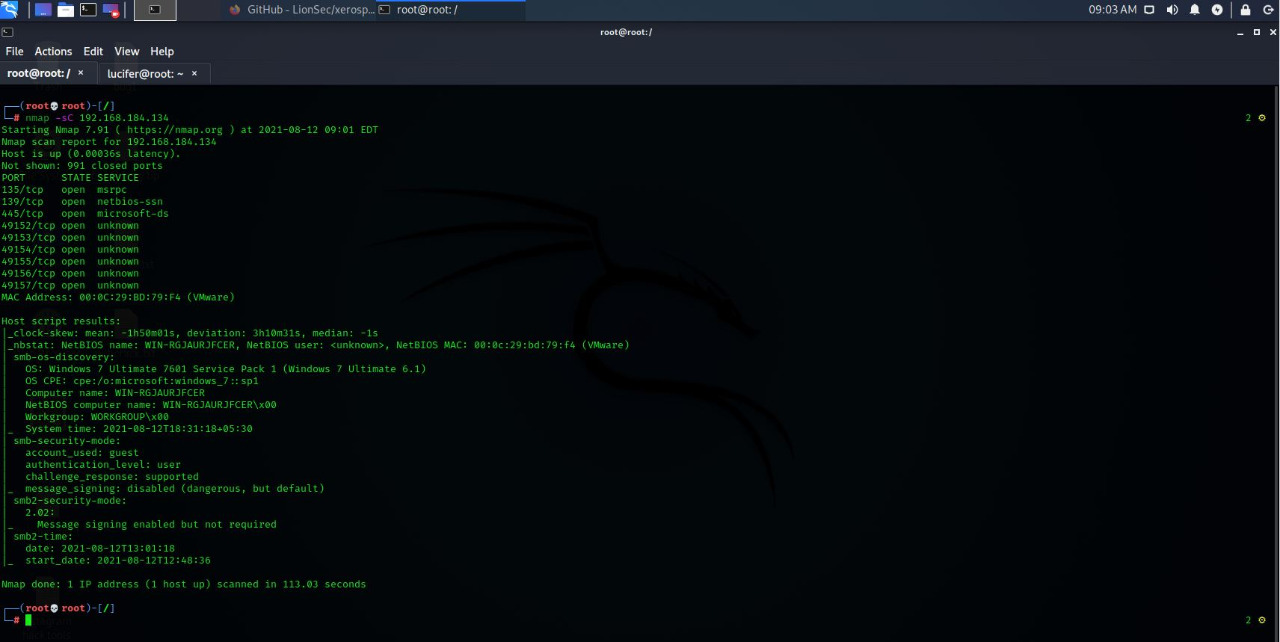
- Minute Details
#nmap -sC <IP Address>
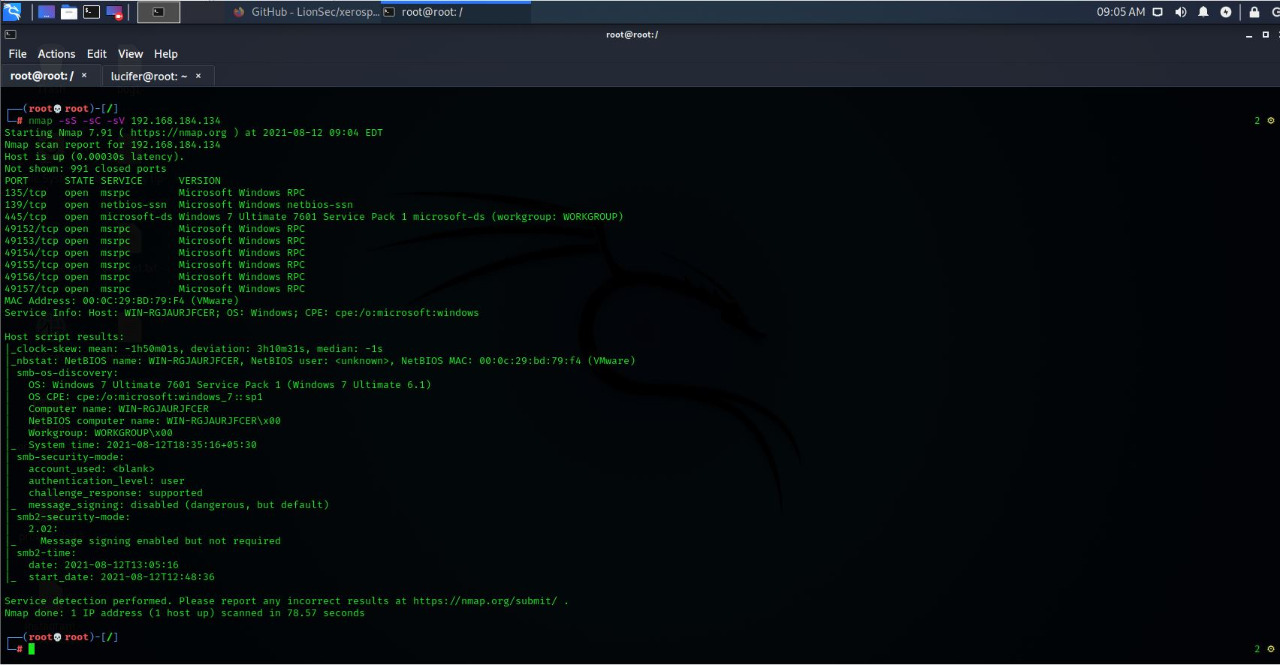
- Combined Scan
#nmap -sS -sC -sV <IP Address>
- Port Specific Scan
#nmap 192.168.0.181 -p80,3306
#nmap 192.168.0.181 -p80-3306
- Firewall Scan
#nmap -f <IP Address>
#nmap <IP Address> -Pn
#nmap <IP Address> -Pn -p80,3306
#nmap –script firewall-bypass <target>
#nmap –script firewall-bypass -Pn -p80,3306 -sS -sC -sV <target>
- Vulnerability Scan
#nmap –script vuln 192.168.0.103 –WINDOWS 7 ,XP
- Operating System Detection Scan
#nmap 192.168.0.105 -O -sC
- To scan a website
#nmap <website domain name>