Top 10 Firewalls in India (2025 Updated)

Top 10 Firewalls in India
Introduction:
Amidst an age where safeguarding digital information is of utmost importance, firewalls act as the initial barrier to protection against online dangers. India has experienced a significant increase in the adoption of firewall technology due to its fast-expanding digital infrastructure.
This article presents a list of the top 10 firewalls available in India, taking into account their security features, performance, ease of use, and customer service.
What is a Firewall?
A firewall is a network security apparatus that scrutinizes and regulates incoming and outgoing network traffic according to an organization’s pre-established security protocols. Essentially, a firewall serves as a barrier between a private internal network from the public Internet. A firewall’s primary objective is to thwart malevolent network traffic, such as viruses and hackers, in order to safeguard the network and mitigate any damage.
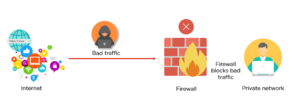
Firewalls can exist as either hardware, software, or a hybrid of the two. They are essential instruments for preserving network security and ensuring its integrity.
How Does A Firewall Work?
A Firewall software works in the following manner:
- Traffic Filtering
| Packet Filtering | The firewall scrutinizes every data packet that enters or exits the network and either approves or denies it according to user-defined regulations. This is comparable to a mailroom in an office that meticulously inspects every parcel entering or leaving. |
| Stateful Inspection | In this context, the firewall not only scrutinizes the data packets but also monitors the status of ongoing connections. It is akin to having a security guard who not only verifies identification at the entrance but also guarantees that persons are in the appropriate places according to their credentials. |
- Proxy Service
Firewalls can function as proxy servers, enabling them to fetch data from the Internet and transmit it to the requesting system, and vice versa. This procedure obfuscates the actual network addresses.
- Content Filtering
Certain firewalls have the capability to selectively restrict access to particular websites or materials by means of content filtering. This is especially advantageous in corporate settings for implementing and ensuring compliance with internet usage regulations.
- NAT (Network Address Translation)
Network Address Translation (NAT) is employed to obfuscate the IP addresses of devices within a local network by utilizing a single IP address. This enhances security by preventing the Internet from being aware of the IP addresses of specific devices.
- Monitoring and Logging
Firewalls record network traffic, which is essential for detecting patterns of attempted breaches or other potential dangers. It is akin to possessing a surveillance system that meticulously documents the entry and exit of individuals, so as to furnish a comprehensive log for potential inquiries in the future.
- Application-Level Gateway and Circuit-Level Gateway
These are enhanced filtering techniques that analyze network traffic at the application or protocol level. They can be configured to enforce intricate regulations on permitted or restricted network traffic.
- Next-Generation Firewalls
These include enhanced functionalities like as deep packet inspection, intrusion prevention systems, and real-time identification and blocking of malicious traffic.
Top 10 Firewalls in India
With the utmost need for Firewalls in our systems in today’s hacking environment, we have jotted down some of the prominent as well as Top 10 Firewalls in India for the coming year 2024. You may seek references from them and choose a firewall software for you or your organization:
-
Cisco ASA Firewall

Key Characteristics:
| Features | Provides sophisticated security features such as intrusion prevention and support for virtual private networks (VPNs). |
| Performance | Renowned for its dependability and resilient performance in busy settings. |
| User Interface | Intuitive interface accompanied by a comprehensive control panel. |
| Support | Superb customer assistance accompanied by an extensive array of service centers. |
-
Fortinet FortiGate

Key Characteristics:
| Features | Combines firewall, antivirus, and intrusion prevention systems into one unified solution. |
| Performance | Optimal efficiency enhanced by cloud functionality. |
| User Interface | The UI is user-friendly and ideal for both novices and experts. |
| Support | Excellent client service with valuable web tools. |
-
Palo Alto Networks Firewall

Key Characteristics:
| Features | Utilize machine learning capabilities to enhance advanced threat defense. |
| Performance | Exceptionally high-efficiency scores, particularly in managing substantial amounts of data. |
| User Interface | Efficient and user-friendly. |
| Support | Robust support system accompanied by comprehensive documentation. |
-
Check Point Firewall

Key Characteristics:
| Features | This software offers comprehensive security management capabilities, specifically emphasizing the implementation of many layers of protection. |
| Performance | Reliable and uninterrupted performance with minimum periods of inactivity. |
| User Interface | Interface that may be customized to suit individual preferences, equipped with comprehensive monitoring features. |
| Support | Our team provides prompt and adaptable support, and we also have a community forum where members can seek assistance from their peers. |
-
Sophos XG Firewall

Key Characteristics:
| Features | Provides a harmonious combination of robustness, efficiency, and observability. |
| Performance | Ideal for small to mid-sized businesses. |
| User Interface | Streamlined administration and documentation. |
| Support | Customer education is prioritized through proactive support. |
-
SonicWall Firewall

Key Characteristics:
| Features | Robust security measures combined with fast VPN capabilities for comprehensive threat protection. |
| Performance | Perfect for enterprises with demanding data transmission needs. |
| User Interface | Contemporary, prioritizing user experience. |
| Support | Excellent technical assistance accompanied by a vibrant online community. |
-
Juniper Networks Firewall

Key Characteristics:
| Features | Excellent scalability and seamless connection with cloud settings. |
| Performance | Intended for expansive networks with high-volume traffic. |
| User Interface | Challenging yet potent for proficient users. |
| Support | Comprehensive support system with worldwide coverage. |
-
Barracuda CloudGen Firewall

Key Characteristics:
| Features | Architecture designed for cloud environments, incorporating enhanced measures to protect against potential threats. |
| Performance | Designed to be very efficient and effective in both cloud and hybrid environments. |
| User Interface | Designed to be easily usable by individuals, with a particular focus on efficient management of data and applications through cloud technology. |
| Support | Extensive assistance with an emphasis on safeguarding cloud systems. |
-
Huawei Firewall

Key Characteristics:
| Features | Advanced security solutions incorporating artificial intelligence to boost threat detection. |
| Performance | Excellent performance in both tangible and digital settings. |
| User Interface | Simple and user-friendly. |
| Support | Expanding the support infrastructure with a specific emphasis on fostering innovation. |
-
WatchGuard Firewall

Key Characteristics:
| Features | Specializes in the implementation of multi-factor authentication and state-of-the-art encryption techniques. |
| Performance | Designed specifically for organizations of modest to moderate size. |
| User Interface | Effortlessly navigable with user-friendly controls. |
| Support | Dependable customer assistance accompanied by a diverse range of internet resources. |
Process of Installing A Firewall
The process of installing a firewall is not rocket science to memorize thoroughly. You can simply do this without any special training. However, knowing all the other specifications of a firewall is of utmost importance.
In the same context, you can follow the below-mentioned pursuit to install a firewall on your system:
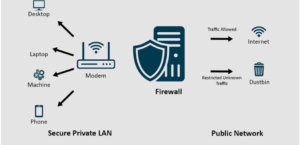
Planning and Requirements Analysis
| Identify Needs | Evaluate the configuration and security needs of the network. Assess the requirement for either a hardware, software, or hybrid firewall solution. |
| Choose the Right Firewall | Choose a firewall that aligns with the organization’s dimensions, security requirements, and financial constraints. |
Preparation
| Backup Data | Prior to installation, make sure you back up all critical data. |
| Update Systems | Ensure that all systems are modified to be compatible with the new firewall. |
Installation
| Physical Setup | To set up hardware firewalls, establish a physical connection between the device and your network. To implement software firewalls, install the software on the specified server or device. |
| Configuration | Adjust the firewall configurations in accordance with your established security protocols. This encompasses the establishment of regulations, the configuration of port forwarding, and the allocation of IP addresses. |
Testing
Test the Firewall: Evaluate the firewall’s functionality to verify its ability to prevent illegal entry while permitting approved network traffic. This may involve conducting penetration testing or performing trial runs.
Monitoring and Maintenance
| Monitor the Firewall | Consistently oversee the firewall’s functioning and logs for any abnormal actions. |
| Update and Maintenance | Ensure that the firewall software and hardware are consistently updated to address emerging threats and vulnerabilities. |
Benefits of A Firewall

The crucial benefits of a firewall are mentioned in the following table:
| Enhanced Security | Firewalls safeguard networks by preventing unauthorized access and mitigating cyber risks such as viruses, worms, and hackers. |
| Controlled Access | They facilitate the administration of network access by regulating the authorization of devices to connect to the network. |
| Monitoring Network Traffic | Firewalls oversee the movement of data, aiding in the identification and prevention of atypical behavior. |
| Preventing Data Leaks | They aid in the prevention of unwanted access or leakage of sensitive data. |
| Regulatory Compliance | Firewalls aid enterprises in adhering to diverse data protection and privacy standards. |
Challenges in Using a Firewall

The primary challenges that an individual faces while utilizing a firewall are as follows:
- Complex Configuration: Configuring and managing firewalls can be difficult, particularly for extensive networks with sophisticated security needs.
- Performance Impact: Firewalls may impede network performance in certain instances, as they necessitate additional processing to scrutinize and regulate traffic.
- False Positives/Negatives: Improperly set firewalls might impede genuine network activity (false positives) or permit harmful network activity (false negatives).
- Costs: Acquiring and upkeeping high-caliber firewalls, particularly for extensive enterprises, might incur substantial costs.
- Evolution of Threats: Staying abreast of the swiftly changing cyber risks and adjusting firewall rules and configurations can pose a challenge.
- Insider Threats: Firewalls primarily prioritize safeguarding against external attacks and may have limited effectiveness in countering threats originating from within the company.
- Need for Expertise: Proficient utilization of firewalls necessitates adept workers possessing expertise in network security.
How News4Hackers Can Help?
If you wish to learn more about other things related to firewalls or other cybersecurity activities, you may seek guidance from the highly skilled and well-qualified training professionals of Craw Security, the leading cybersecurity training provider in India and the sister vertical of News4Hackers, the Best Cybersecurity Info, and News Portal. In order to get more info on Craw Security’s in-house training programs or partner-oriented training certifications, you may give them a call at their round-the-clock mobile number +91-9513805401 or log on to their Official Website.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE





