The First Million Stolen Records in the Ticketmaster Breach were Released for Free

The First Million Stolen Records in the Ticketmaster Breach were Released for Free
The first one million records that are included in the data collection that the cybercriminal who was acting under the moniker “Sp1d3r” claimed to have stolen from Ticketmaster/Live Nation were made available to the public. Free and without charge, the files were made available to the public.

At the time when Malwarebytes Labs first became aware of this data breach, it was the first big incident that was discussed on the revived BreachForums. At that time, an individual using the nickname “ShinyHunters” offered to sell the complete information (name, address, email, and phone number) of 560 million consumers.
A user using the handle “SpidermanData” posted a post on another forum that was remarkably identical to the one in which they offered the same data set for sale a few days before. It is possible that this is the same individual or that it is a member of the ShinyHunters organization.

In the aftermath of this event, Malwarebytes Labs provided readers with guidance on how to react and maintain their safety. Importantly, even in situations where a breach is not considered a “breach” — in that instant when the details have not yet been confirmed and a breach victim is getting ready to make public pronouncements — the very news of the suspected breach can be utilized by hackers who are looking to gain an advantage as a phishing lure.
Ticketmaster later confirmed that there had been a breach of data.
ShinyHunters informed Bleeping Computer that they already had buyers who were interested in purchasing their products. Currently, Sp1d3r, who was spotted blogging before regarding customer data from Truist Bank and Advance Auto Parts, has made available for free one million data records relating to Ticketmaster.
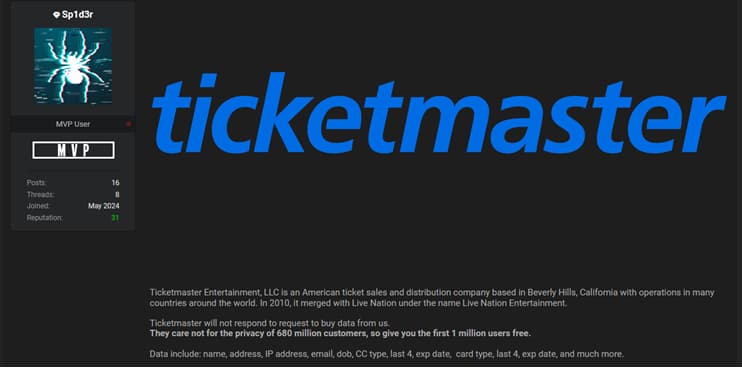
In a post that was made on BreachForums, Sp1d3r stated:
| “Ticketmaster will not respond to request to buy data from us.
They care not for the privacy of 680 million customers, so give you the first 1 million users free.” |
The cybercriminals who are active on those forums will surely take advantage of the opportunity and make an effort to make money off of those records immediately. When this occurs, it is quite possible that innocent individuals who are included in the first million records that were published will be subjected to a significant amount of spam and phishing emails in the days that are to follow.

How To Protect Yourself Once A Data Breach Has Occurred?
If you are the victim of a data breach or if you suspect that you may have been the victim of such a breach, there are several activities that you can take.
- Find out what the vendor recommends. As each breach is unique, it is important to contact the vendor to inquire about what has occurred and to adhere to any specific recommendations that they may provide.
- Change your password, please. Changing a password that has been stolen can render it useless to the person who took it. It is important to select a robust password that you will not use for any other purpose. What’s even better is that you can let a password manager pick one for you.

- Turn on two-factor authentication, often known as 2FA. If you are able to, utilize a hardware key that is compliant with FIDO2 as your second factor, either a laptop or a phone. Some types of two-factor authentication, sometimes known as 2FA, are susceptible to phishing attacks almost as easily as passwords. Phishing is not possible for two-factor authentication that is based on a FIDO2 device.
- Be wary of suppliers who are not genuine. Under the guise of the vendor, the criminals could get in touch with you. In addition to verifying the identity of anyone who contacts you through a different communication channel, you should check the website of the seller to determine whether or not they are contacting victims.
- Hold on to your time. Themes that require immediate response, such as missing deliveries, account suspensions, and security alerts, are frequently used in phishing attacks. Phishing attempts frequently spoof businesses or individuals that you are familiar with.
- Give some thought to not saving your card information. We strongly advise against saving your credit card information on websites, despite the fact that it is certainly more convenient to have websites remember your card details for you.
- Identity monitoring should be set up. In the event that your personal information is discovered to be being traded unlawfully online, identity monitoring will notify you and assist you in recovering from the situation.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE