Terrorist Outfits Are Using Cyberspace to Target the Paris Olympics 2024 and the US General Elections: Resecurity

Terrorist Outfits Are Using Cyberspace to Target the Paris Olympics 2024 and the US General Elections: Resecurity
Synopsis:
- The Paris Olympics and U.S. elections were the targets of terrorists’ cyberspace attacks, as revealed by Resecurity. Terrorists utilized digital channels to recruit and attack.
- New strategies, such as the exploitation of cryptocurrencies for funding and the development of secure applications for anonymous communication, present substantial threats to global security.
Some days back, FBI Director Christopher Wray acknowledged rising concerns about a concerted foreign terrorist assault in the US. In his House Oversight Committee hearing, Mr. Wray referenced the March ISIS-K attack on Crocus City Hall in Moscow as a threat the bureau is increasingly concerned about.
He also stressed the necessity for international cooperation to combat terrorism and the risk of foreign terrorists exploiting the U.S. southern border. The FBI is investigating ISIS, al Qaeda, al Shabbab, Hezbollah, and IRGC. “We are increasingly concerned about a coordinated foreign terrorist attack, as well as a foreign terrorist-inspired attack,” he said.
He said that prosecutors sentenced an Iraqi immigrant who planned to infiltrate a terrorist hit squad into the US to kill former President George W. Bush this year. Mr. Wray also warned that foreign terrorists could exploit the U.S. southern border. He stressed the necessity for worldwide cooperation to combat these challenges. The worrisome revelations challenge the security community and corporate sector to take a proactive approach to address this danger, including recognizing online precursors.
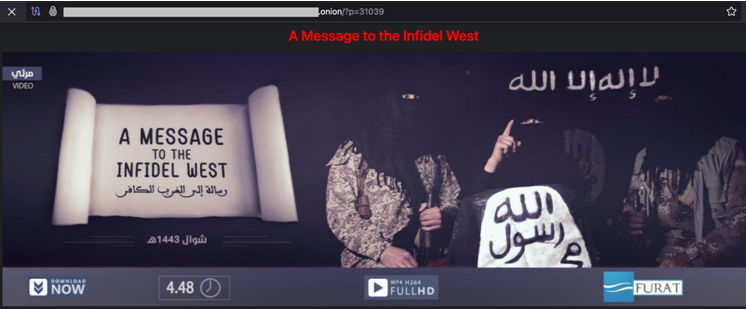
“A Message To The Infidel West”
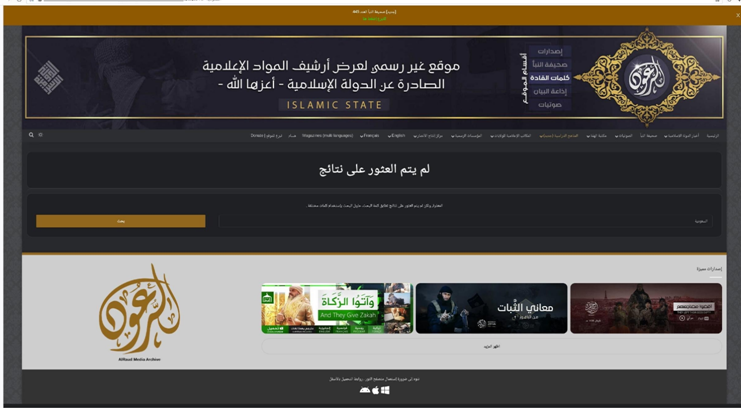
Resecurity found that terrorist groups are increasingly leveraging cyberspace and digital communication channels to plan and execute attacks, recruit, and build anonymous channels. Terrorist resources have been found on the public web and Tor.
New resources began surfacing in Q3 2024 after Q2 2024’s considerable activity. The worldwide security community is tracking such sites and intends to remove them from the surface web to prevent illicit content dissemination, but anonymous peer-to-peer networks make censorship difficult. Terrorists use this to recruit kids, convey misinformation, and recruit.
They also use cryptocurrency to receive donations and other funding. The most popular cryptocurrencies used by terrorists are Monero (XMR) and ZEC. Threat actors routinely upgrade cryptocurrency wallets to elude detection and obscure financial transaction distribution channels for money laundering. One of the last cryptocurrency wallet updates was found on March 29, 2024.
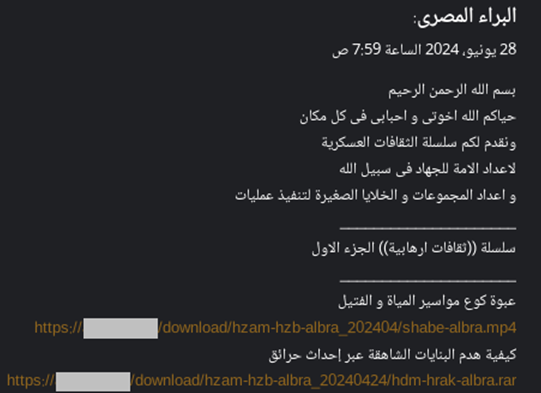
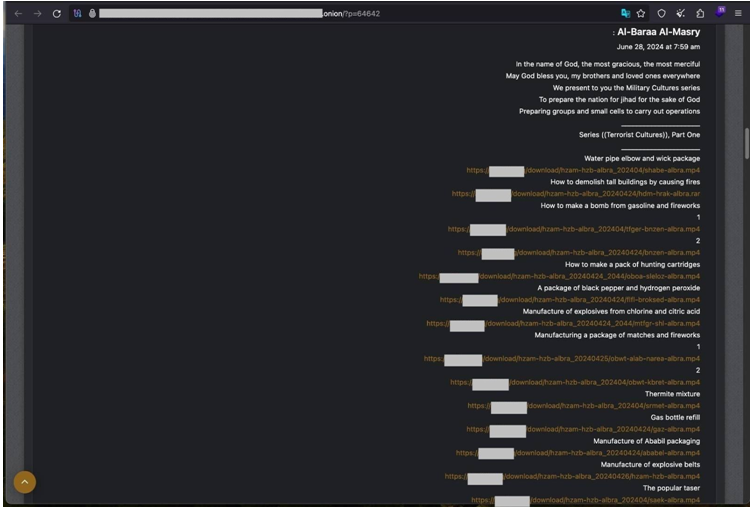
June 28, 2024 — the actors issued explicit guidelines for making explosive devices. Terrorists aim to promote hateful messages.
Terrorists employed surface online sites to make illicit materials easily accessible for download. The security community must speed online information distribution prevention.
Several illegal radical media organizations coordinate and encourage this activities.
ISIS Makes Chilling Threat To Bomb Opening Ceremony Of Paris Olympics
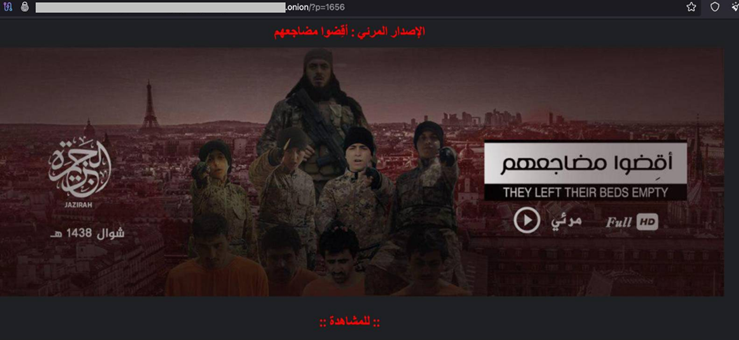
ISIS posted a terrifying graphic online claiming drones may be used to bomb the Paris Olympics, with a caption stating the “Lone Wolves’ Olympics” begin.
Terror group operators posted a photo of a faceless person flying a drone with a ‘gift’ box near the Eiffel Tower. Image caption: “Lone wolves’ Olympics have begun with the Will of Allah.” The image was posted on IS-affiliated website al-Ru’ud (al-Raud). It read, “The Lone Wolves qualifiers have begun, God willing Al-Adiyat Media Foundation.”
Illegal Content Distribution And Propaganda
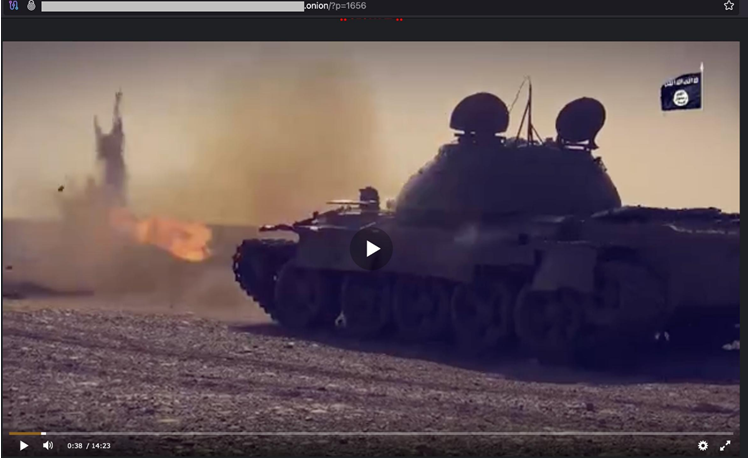
Besides ‘lone wolf’ assaults, terrorists are transferring instructional materials and advanced military training to other groups.
TOR file exchangers host the content, which is made available using specialized plugins like http://playerjs.com.
Hosting illicit videos on Tor protects them from takedown attempts. Because the Tor Network provides extreme anonymity, authorities find it hard to identify and prohibit content. J. Rami Mroz’s “Countering Violent Extremism Videopower and Cyberspace” found that terrorists and extremist groups exploited video formats to inspire and attract international audiences due to their emotional and psychological impact. Threat actors use video and cyberspace to:
- introduce religious or ideological rhetoric into political discourse
- adapt existing imagery from mainstream media to meet their objectives
- cultivate and/or amplify a belief-driven sense of purpose by eliciting emotive responses from their target audiences
- safeguard and regulate communication channels
- operate networks that are diffuse
- assemble an “army of believers”
- recruit operatives, particularly youthful individuals, to engage in violent activities
- furnish operational intelligence and information
- awe their adversaries
- solicit financial support.
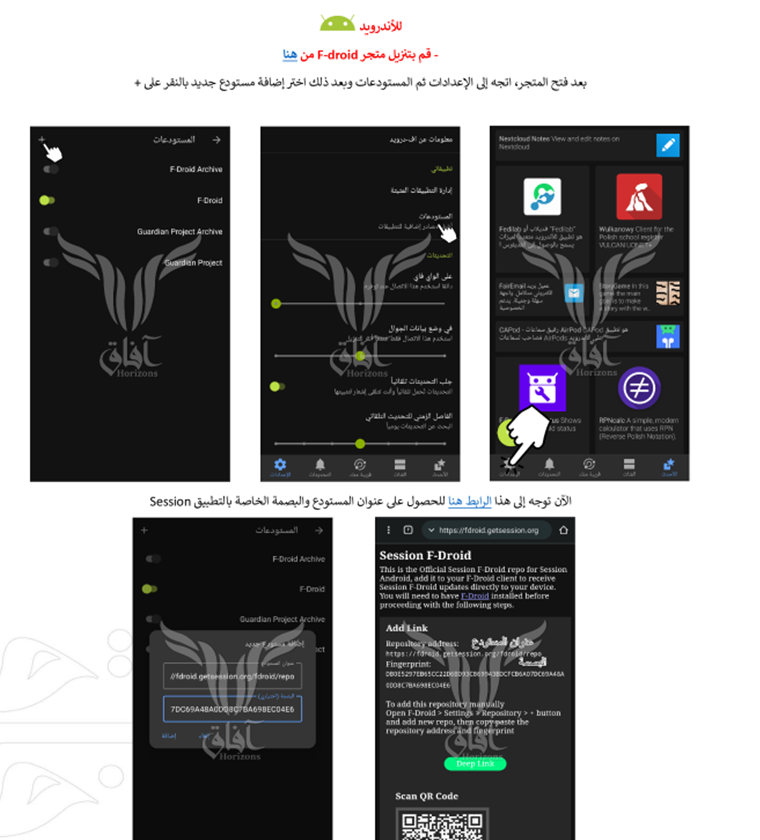
Apart from all this, there are multiple Anonymous Communication Channels that are duly active in promotion such as the secure messenger apps like Session.
The content is primarily written in Arabic, but there were identified translations in other languages as well including French and Russian:
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
READ MORE ARTICLE HERE