Take A Caution on ‘Cyberstalking’: CERT-In Unveils Best Practices Against Cyberstalking On Its Official X Handle.

The official cyber watch station of India, CERT-In has issued best practices in the public interest against cyberstalking on its official X (formerly Twitter) handle and informed every individual to stay vigilant against such nuisance attacks. The post read “Safety Tips Against Cyberstalking” and gave the best chances to learn and stay alert from the heinous acts of some anti-social elements.

What is Cyberstalking?
The utilization of the internet or other forms of technology to harass or pursue a person, organization, or group constitutes cyberstalking. Tracking, identity theft, threats, criminal activity, sexual solicitation, or the collection of information that could be used to torment or threaten others are all examples.

How Does Cyberstalking Work?
| Harassing Communications | This encompasses the dissemination of unsolicited, repetitive, and menacing emails, messages, or remarks across social media platforms. |
| Creating Fake Profiles | Stealers might fabricate social media profiles in order to observe or engage in conversations regarding the online activities of the targeted individual. |
| Identity Theft | By impersonating the victim online using their private information, cyberstalkers may attempt to harm their reputation or relationships. |
| Monitoring Online Activity | Cyberstalkers frequently conduct extensive surveillance of the online activities of their targets, encompassing forum participation, online purchases, and social media postings. |
| Using Location Services | By using geotagging information in social media posts or images, cyberstalkers can determine the location of the victim. |
| Exploiting Personal Data | Acquiring unauthorized access to confidential information such as photographs, contact details, or professional information, with the intent to harass or coerce the target. |
| Spreading False Information | Distributing or posting false information about the victim on the Internet with the intent to harm their reputation or relationships. |
| Installing Spyware | Cyberstalkers occasionally install spyware onto the devices of their targets in order to surveil their communications and activities. |
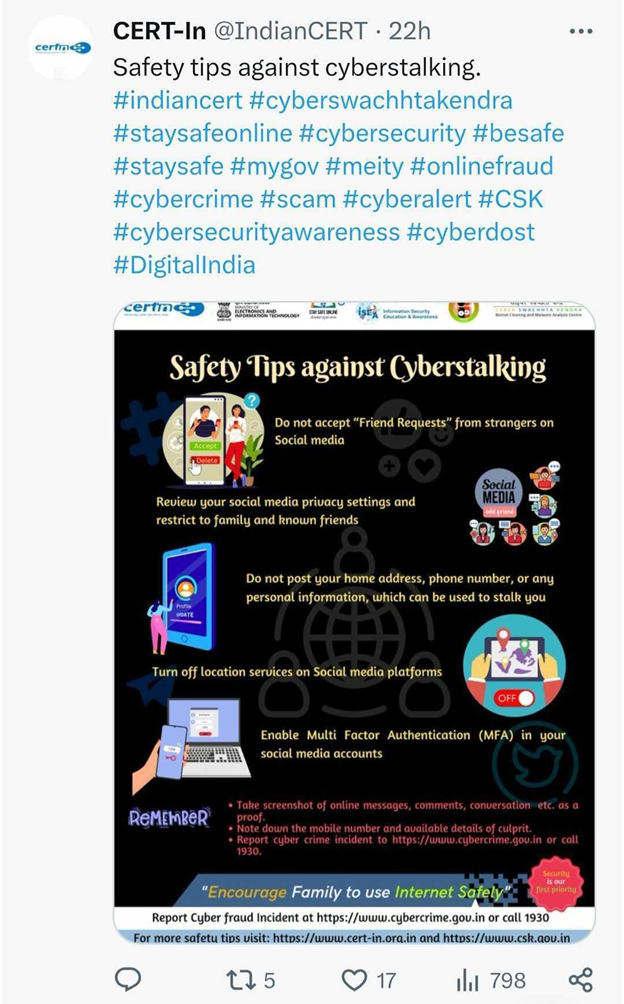
Safety Tips Against Cyberstalking
- Do not accept “Friend Requests” from strangers on Social Media.
- Review your social media privacy settings and restrict to family and known friends.
- Do not post your home address, phone number, or any personal information, which can be used to stalk you.
- Turn off location services on social media platforms.
- Enable Multi-Factor Authentication (MFA) in your social media accounts.

Do Remember To:
- Take screenshots of online messages, comments, conversations, etc. as proof.
- Note down the mobile number and available details of the culprit.
- Report cybercrime incident to https://www.cybercrime.gov.in or call 1930.
By exercising caution and staying informed, one can protect their personal information and get trapped in cyberstalking.

Precaution Advisory from News4Hackers
It is always so tempting to upload photos and videos of our accomplishments and visits! However, cybercrooks do note all kinds of activities to lure you into some fake promotions or advertisements.
DO NOT FALL TRAP TO SUCH ACTIVITIES. DO NOT POST YOUR UTMOST PERSONAL INFORMATION ON SOCIAL MEDIA. IT’S FOR YOUR OWN GOOD!
Stay Alert! Stay Safe!

About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE