Nikto – The Hacker’s Chosen Cybersecurity Tool
Nikto – The Hacker’s Chosen Cybersecurity Tool
Nikto is a highly effective open-source web server scanner that is extensively employed in the fields of penetration testing and cybersecurity. Nikto, which was designed to detect potential security issues and vulnerabilities in web servers, conducts exhaustive evaluations by probing for known flaws, misconfigurations, and obsolete software.

With its ability to facilitate both manual and automated testing, this tool offers security professionals a flexible solution to assess the security stance of web servers. Nikto possesses an extensive repository of recognized vulnerabilities, which enables it to identify a wide array of concerns such as obsolete server software, exposed sensitive files, and potential security hazards.

In addition, Nikto possesses the capability to produce comprehensive reports and seamlessly integrate with additional security tools, rendering it an invaluable resource for ethical hackers and security analysts who aim to strengthen the security of online systems and web server defenses. Active community support, regular updates, and user-friendliness all contribute to its prominence in the cybersecurity community.
#Nikto Flags
| -help | This help information |
| -host+ | Target host/URL |
| -id+ | Host authentication to use, format is id:pass or id:pass:realm |
| -ipv4 | IPv4 Only |
| -ipv6 | IPv6 Only |
| -list-plugins | List all available plugins, perform no |
| -mutate+ | Guess additional file names: |
| -mutate-options | Provide information for mutates |
| -nointeractive | Disables interactive features |
| -nolookup | Disables DNS lookups |
| -nossl | Disables the use of SSL |
| -noslash | Strip trailing slash from URL (e.g., ‘/admin/’ to ‘/admin’) |
| -no404 | Disables nikto attempting to guess a 404 page |
| -output+ | Write output to this file (‘.’ for auto-name) |
| -Plugins+ | List of plugins to run (default: ALL) |
| -port+ | Port to use (default 80) |
| -RSAcert+ | Client certificate file |
| -root+ | Prepend root value to all requests, format is /directory |
| -Save | Save positive responses to this directory (‘.’ for auto-name) |
| -ssl | Force ssl mode on port |
These are some important flags that you use when you are trying to gather information on the host. Below is a simple example of the Nikto:
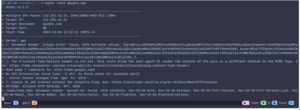
You can check out all the plugins with `-list-plugins`.
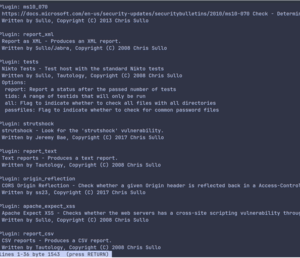
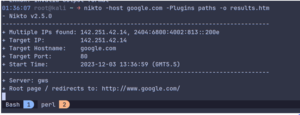
For demonstration, I can use the ‘path’ plugin on google.com. By default nikto runs all the plugins.
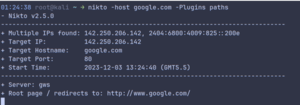
I can save my output using ‘-o filename’. Be sure to end your filename with any of these extensions:
| csv | Comma-separated-value |
| json | JSON Format |
| htm | HTML Format |
| nbe | Nessus NBE format |
| sql | Generic SQL (see docs for schema) |
| txt | Plain text |
| xml | XML Format |
How News4Hackers Can Help?
It is widely acknowledged that News4Hackers is a highly decorated news and cybersecurity information source, delivering innovative insights to its audience regarding the most recent developments, methodologies, technologies, and cyber assaults targeting organizations across the globe. Our news collectors remain vigilant around-the-clock in pursuit of breaking technology news in order to deliver it to you with the utmost urgency.
Furthermore, it is worth noting that Craw Security operates as a subsidiary of News4Hackers, a globally renowned provider of cybersecurity training with offices in India and other significant countries. You may contact them via their mobile hotline (+91-9513805401) with any inquiries regarding the forthcoming cohorts of their top-tier cybersecurity training programs or any other matters related to cybersecurity.
READ MORE ARTICLE HERE









