New Eldorado Ransomware is Hitting to Infect VMware ESXi VMs and Windows Systems

New Eldorado Ransomware is Hitting to Infect VMware ESXi VMs and Windows Systems
In March, a new ransomware-as-a-service (RaaS) known as Eldorado was released. It comes with locker variations for both Windows and VMware ESXi.

There have already been sixteen victims of the gang, most of whom were victims in the United States, specifically in the fields of industry, education, healthcare, and real estate.

Researchers from the cybersecurity company Group-IB tracked the activity of the Eldorado and discovered that its owners were pushing the malicious service on RAMP forums and looking for skilled affiliates to join the scheme.
A data leak website that lists victims is also operated by Eldorado; however, at the time of this writing, the website was unavailable.
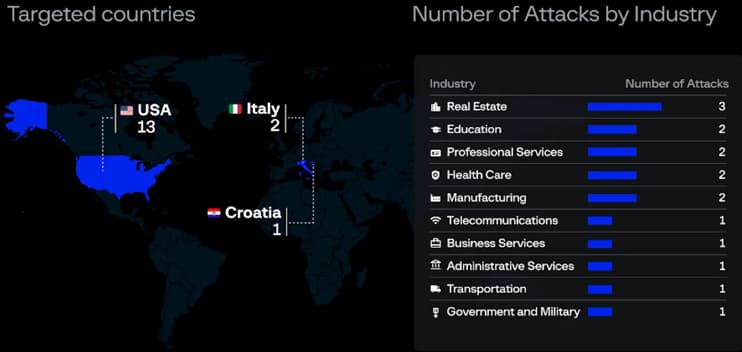
Eldorado ransomware targets
Source: Group-IB
Microsoft Windows and Linux encryption
Using two unique variations that have a significant amount of operational similarities, Eldorado is a ransomware that is based on the Go programming language and has the ability to encrypt both Windows and Linux platforms.
The researchers were able to get an encryptor from the developer. The encryptor came with a user manual that stated that there are 32-bit and 64-bit variants available for Windows and VMware ESXi hypervisors.
The Eldorado is a one-of-a-kind development, according to Group-IB, which also states that it does not rely on previously released builder sources.

For the purpose of encryption, the malicious software employs the ChaCha20 algorithm, and it generates a one-of-a-kind 32-byte key and a 12-byte nonce for each of the files that have been locked. After that, the keys and nonces are encrypted by applying the RSA algorithm with the OAEP scheme, which stands for Optimal Asymmetric Encryption Padding.
Following the completion of the encryption process, the files are given the extension “.00000001” and ransom notes with the name “HOW_RETURN_YOUR_DATA.TXT” are placed in the Documents and Desktop folders.

The Eldorado ransom note
Source: Group-IB
Eldorado additionally deletes shadow volume copies on compromised Windows workstations in order to hinder recovery. This is done in order to optimize the impact of the encryption of network shares, which is accomplished through the use of the SMB communication protocol.
In order to prevent the system from becoming unbootable or unusable, the ransomware will bypass DLLs, LNK, SYS, and EXE files, as well as files and directories that are associated with the installation of the system and its fundamental functions.
In conclusion, it is configured to remove itself automatically by default in order to avoid detection and analysis by reaction teams.

Researchers from Group-IB, who were able to infiltrate the organization, have stated that affiliates have the ability to personalize their attacks. For instance, on Windows, they have the ability to define which folders should be encrypted, bypass local files, target network shares on particular subnets, and prevent the malware from deleting itself.
Nevertheless, the customization settings on Linux are limited to the configuration of the directories that are encrypted.
Some Crucial Facts:
| Affected Platform(s) / Version(s) | Windows and Linux platforms, VMware ESXi. |
| Distribution Method | Undisclosed |
| Attack Type | Ransomware Attack |
| Attack Source | Unauthorized Access |
| Region | USA |
| Affected Business(s) | Multiple Sectors |
| Direct File Download | IoC Eldorado_Ransomware_05_07_2024.xlsx |
Defense Recommendations
Group-IB, which is responsible for defense suggestions, emphasizes that the Eldorado ransomware threat is a new, independent operation that did not originate as a rebranding of another group.
A degree of protection against any and all ransomware attacks can be achieved by implementing the following defenses, which are recommended by the researchers:
- The use of multi-factor authentication (MFA) and access solutions based on credentials is recommended.
- To swiftly identify ransomware indicators and respond to them, you can make use of Endpoint Detection and Response, also known as EDR.
- Utilize data backups on a regular basis to reduce the risk of data loss and harm.
- Make use of artificial intelligence-based analytics and sophisticated malware detonation in order to detect and respond to intrusions in real time.
- In order to address vulnerabilities, it is important to prioritize and routinely apply security fixes.
- Employees should be educated and trained to identify and report any potential cybersecurity concerns.
- Both technical audits and security assessments should be performed annually, and digital hygiene should be maintained.
- Refrain from paying the ransom because doing so almost never guarantees the recovery of data and can lead to other attacks.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
READ MORE ARTICLE HERE






