Netcat — All You About This Exciting Cyber Security Tool

Netcat — All You About This Exciting Cyber Security Tool
What is Netcat Used For?
Netcat can be a useful tool for any IT team, though the growth of internally managed network services and cloud computing makes that particular environment a natural fit. Network and system administrators need to be able to quickly identify how their network is performing and what type of activity is occurring.
Basic Netcat Commands
Here are a few to get started with:
nc -help – This command will print a list of all of the available commands you can use in Netcat. It will come in handy if you run into any errors while writing a script or are unsure of how to proceed.
nc -z -v site.com – This will run a basic port scan of the specified website or server. Netcat will return verbose results with lists of ports and statuses. Keep in mind that you can use an IP address in place of the site domain.
nc -l – This command will instruct the local system to begin listening for TCP connections and UDP activity on a specific port number.
nc site.com 1234 (less than) file_name – This command will initiate the transfer of a file based on the specified port number.
Printf – Netcat can actually operate as a simplified web host. This command will let you save HTML code and publish it through your local server.
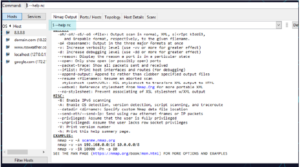
A basic port scan command for an IP ncat address looks like this:
nc -v -n 8.8.8.8 1-1000
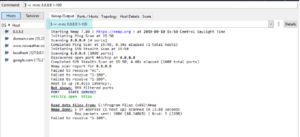
If you don’t know the IP address of a server or website, then you can look it up via a ping terminal command or just insert the domain into the Netcat command:
nc -v -n google.com 1-1000
General Syntax
By default, netcat operates by initiating a TCP connection to a remote host.
netcat [options] host port
If you would like to send a UDP packet instead of initiating a TCP connection, you can use the -u option:
netcat -u host port
You can specify a range of ports by placing a dash between the first and last:
netcat host startport-endport
How To Use Netcat for Port Scanning?
We do this by specifying a range of ports to scan, as we did above, along with the -z option to perform a scan instead of attempting to initiate a connection.
For instance, we can scan all ports up to 1000 by issuing this command:
netcat -z -v domain.com 1-1000
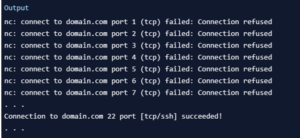
However, your scan will go much faster if you know the IP address that you need. You can then use the -n flag to specify that you do not need to resolve the IP address using DNS:
netcat -z -n -v 198.51.100.0 1-1000
We will redirect standard error to standard output using the 2>&1 bash syntax. We will then filter the results with grep:
netcat -z -n -v 198.51.100.0 1-1000 2>&1 | grep succeeded
How To Communicate Through Netcat?
Netcat is not restricted to sending TCP and UDP packets. It also can listen on a port for connections and packets. This gives us the opportunity to connect two instances of Netcat in a client-server relationship.
On one machine, you can tell Netcat to listen to a specific port for connections. We can do this by providing the -l parameter and choosing a port:
netcat -l 4444
This will tell Netcat to listen for TCP connections on port 4444. As a regular (non-root) user, you will not be able to open any ports under 1000, as a security measure.
On a second server, we can connect to the first machine on the port number we chose. We do this the same way we’ve been establishing connections previously:
netcat domain.com 4444
will look as if nothing has happened. However, you can now send messages on either side of the connection and they will be seen on either end.
How To Send Files Through Netcat?
netcat -l 4444 > received_file
The > in this command redirects all the output of Netcat into the specified filename.
On the second computer, create a simple text file by typing:
echo “Hello, this is a file” > original_file
We can now use this file as input for the Netcat connection we will establish to the listening computer. The file will be transmitted just as if we had typed it interactively:
netcat domain.com 4444 < original_file
We can see on the computer that was awaiting a connection, that we now have a new file called received_file with the contents of the file we typed on the other computer:
cat received_file

For instance, we can transfer the contents of an entire directory by creating an unnamed tarball on-the-fly, transferring it to the remote system, and unpacking it into the remote directory.
On the receiving end, we can anticipate a file coming over that will need to be unzipped and extracted by typing:
netcat -l 4444 | tar xzvf –
The ending dash (-) means that tar will operate on standard input, which is being piped from Netcat across the network when a connection is made.
On the side with the directory contents we want to transfer, we can pack them into a tarball and then send them to the remote computer through Netcat:
tar -czf – * | netcat domain.com 4444
Optimize File Transfers
When you send large files, you can compress them on the fly to speed up the transfer.
On the receiving end enter:
nc -vl 44444 | gunzip > pick_desired_name_for_file
And on the sender, enter the following, replacing 10.11.12.10 with the IP address of your receiving device:
gzip -c /path/to/file/you/want/to/send | nc -N 10.11.12.10 44444
How News4Hackers Can Help?
News4Hackers is an international news organization specializing in timely and enlightening articles regarding cybersecurity. In addition, News4Hackers is committed to providing our audience with up-to-date information concerning the most recent developments, approaches, technologies, and cyber assaults that are specifically designed to compromise organizations worldwide. Our news collectors remain attentive to the most recent technological developments on a daily basis in order to provide you with them as soon as possible.
Furthermore, it is worth noting that Craw Security maintains a partnership with News4Hackers, a well-regarded organization that focuses on cybersecurity and provides insightful analysis and perspectives on a multitude of significant nations, including India. To obtain further information on their exceptionally successful cybersecurity training courses or any other subject pertaining to cybersecurity, please contact them at the following number: +91-9513805401.
READ MORE ARTICLES HERE