Malvertizers Target Individuals Conducting Searches for Famous Software Employing Google Ads
Malvertizers Target Individuals Conducting Searches for Famous Software Employing Google Ads
New information has been revealed regarding a malvertising effort that exploits Google Ads as a means to redirect people seeking popular software to fraudulent landing pages, hence disseminating subsequent payloads.
According to Malwarebytes, the entity that detected this behavior, it possesses a distinctive capability to identify people and disseminate time-sensitive payloads.
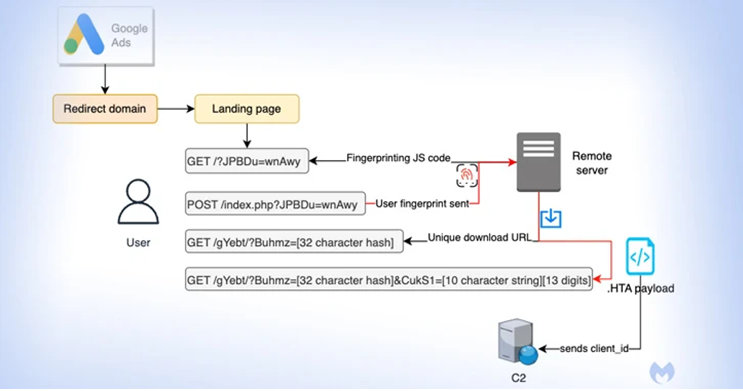
The assault specifically targets individuals who are conducting searches for Notepad++ and PDF converters, with the intention of displaying fraudulent advertisements on the Google search results page. These ads are designed to filter out automated programs (bots) and other undesired IP addresses by presenting a deceptive website when clicked.
If the visitor is considered to be of interest to the threat actor, they will be sent to a replica website that promotes the program. Simultaneously, the system will be quietly fingerprinted to ascertain whether the request is originating from a virtual machine.
When users do not pass the verification process, they are redirected to the official website of Notepad++. Meanwhile, a distinct identification number is provided to a possible target for the goal of tracking, as well as to ensure that each download is both unique and time-restricted.
The ultimate kind of malicious software is a payload in the form of an HTA file, which initiates a connection to a distant domain named “mybigeye[.]icu” through a customized port. This connection is utilized to distribute subsequent malware.
According to Jérôme Segura, the director of threat intelligence, threat actors are effectively employing evasion strategies to circumvent ad verification checks, enabling them to specifically target particular categories of victims.
By possessing a dependable malware supply network, nefarious individuals can concentrate on enhancing their deceptive web pages and creating tailored malware payloads.
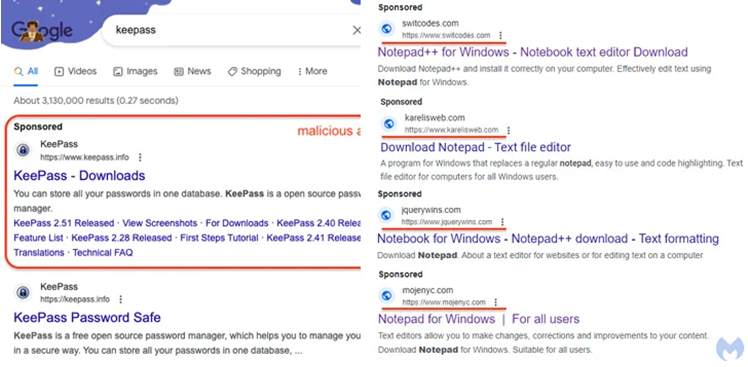
The disclosure encompasses a campaign that exhibits an overlap with another initiative, which specifically aims at people who are searching for the KeePass password manager. This particular campaign employs deceitful advertisements that redirect unsuspecting victims to a domain that utilizes Punycode (keepass[.]info vs. ķeepass[.]info). Punycode is a specialized encoding technique employed to transform Unicode letters into ASCII.
According to Segura, individuals who engage with the advertisement will be redirected to a cloaking service designed to identify and exclude sandboxes, bots, and individuals who are not considered genuine victims. The threat actors have established a transient domain at the keepasstacking[.]site, which executes a conditional redirect to the ultimate destination.

Individuals who access the deceptive website are deceived into acquiring a malevolent installation program, which subsequently initiates the activation of FakeBat (also known as EugenLoader), a loader specifically designed to retrieve additional harmful software.
The utilization of Punycode in conjunction with rogue Google Ads signifies an advancement in the sophistication of malvertising through search engines, although this practice is not wholly unprecedented. The objective of utilizing Punycode to register domain names that resemble a legal website is to execute a homograph attack, thereby enticing unsuspecting individuals to install malicious software.
Segura stated that the utilization of Punycode in conjunction with internationalized domain names has been employed by malicious individuals for an extended period to deceive unsuspecting targets. This observation highlights the enduring efficacy of this technique in the realm of brand impersonation through the means of malicious advertising.
In relation to visual deception, it has been observed that various threat actors, namely TA569 (also known as SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), ClearFake, and EtherHiding, are exploiting themes associated with counterfeit browser updates to disseminate Cobalt Strike, loaders, stealers, and remote access trojans. This indicates that these attacks pose an ongoing and dynamic threat.
According to an investigation published this week by Dusty Miller, a researcher at Proofpoint, deceptive browser updates exploit the trust of end users by utilizing hacked websites and bait that is tailored to the user’s specific browser. This strategy aims to provide the appearance of legitimacy to the update and deceive users into clicking on it.
The potential danger is solely within the web browser and might be triggered by a user’s interaction, such as clicking on a genuine and anticipated email, accessing a social networking platform, conducting a search engine query, or just visiting a hacked website.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article Here






