Malicious Apps Detected Secretly Transforming Android Devices into Agents for Hackers
xr:d:DAFuft7RJ-o:1004,j:8388377996873835543,t:24040308
Malicious Apps Detected Secretly Transforming Android Devices into Agents for Hackers
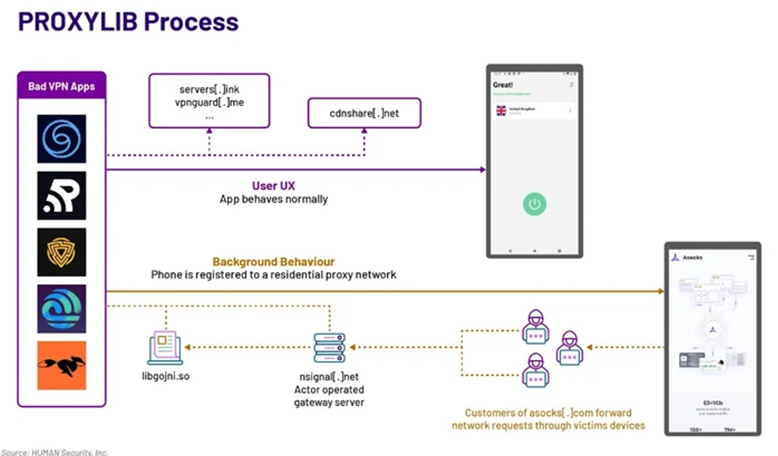
On the Google Play Store, a number of malicious Android applications that transform mobile devices carrying out the operating system into residential proxies (RESIPs) for other hackers have been identified.

The results were reported by the Satori Threat Intelligence team of HUMAN. According to the team, the collection of VPN applications was equipped with a Golang library that surreptitiously converted the user’s device into a proxy node.
The organization has assigned the designation PROXYLIB to the operation. Subsequently, Google removed the 29 malicious applications.
Residential proxies comprise a network of proxy servers that utilize authentic IP addresses supplied by Internet service providers (ISPs). By routing users’ internet traffic through an intermediary server, these proxies enable users to conceal their true IP addresses.

Aside from the advantages of anonymity, they are highly susceptible to exploitation by threat actors who can use them to conceal their true origins and execute a variety of attacks.
“When an adversary employs a residential proxy, the traffic resulting from such assaults looks to be originating via multiple residential IP addresses instead of an IP of a data center or another component of a threat actor’s infrastructure,” researchers from security firms said. “Many hackers purchase access to these systems for the sake of their operations.”

Malware administrators may establish some of these networks by deceiving unsuspecting users into installing bogus applications, which essentially ensnare the devices in a botnet and subsequently generate revenue through the sale of access to other customers.
HUMAN has identified Android VPN applications that are specifically engineered to establish a connection with a remote server, enroll the compromised device into the network, and execute any request originating from the proxy network.
An additional noteworthy feature of these applications is that a subset of them, which were identified between May and October 2023, utilize a LumiApps software development kit (SDK) that includes the proxyware functionality. The malevolent capability is executed in both scenarios by utilizing an inbuilt Golang library.
Additionally, LumiApps provides a feature that enables users to upload and bundle the SDK for any APK file, including those of legitimate applications, without the need to establish an account. The bundled file can then be re-downloaded and shared with others.

“LumiApps assists organizations in collecting publicly accessible information from the internet,” the Israeli firm states on its website. “It employs the user’s IP address to load multiple web pages in background mode from well-known websites.”
“This is accomplished without ever interrupting the user and in strict accordance with GDPR/CCPA regulations.” The organizations subsequently receive the web pages and implement them into their databases in order to provide more competitive pricing, products, and services.

Then, these modified applications, known as mods, are distributed both within and outside the Google Play Store. LumiApps markets itself and the SDK as an alternative to ad rendering for app monetization.
Supporting evidence suggests that the threat actor responsible for PROXYLIB is distributing access to the proxy network established by the compromised devices via LumiApps and Asocks, two entities that promote themselves as providers of residential proxies.

Furthermore, to enhance the botnet’s scale and facilitate the integration of the software development kit (SDK) into a wide range of applications, LumiApps incentivizes developers with cash prizes contingent on the volume of traffic that traverses user devices sporting their apps. Social media platforms and black hat forums are utilized to promote the SDK service.

In a study recently published by Orange Cyberdefense and Sekoia, residential proxies were described as components of a “fragmented yet interconnected ecosystem.” This ecosystem encompasses a variety of advertising channels for proxyware services, including dedicated shops, reselling channels, and voluntary contributions.
“[In the case of software development kits] proxyware is frequently integrated into a product or service,” the firms noted. Proxyware may be installed without the user’s knowledge when they approve the terms of service for the primary application in which it is embedded. The absence of transparency results in users disclosing their Internet connection without a comprehensive comprehension.
The revelation coincides with the revelation by Lumen Black Lotus Labs that a botnet dubbed TheMoon is exploiting end-of-life (EoL) small home/small office (SOHO) routers and IoT devices in order to power the malicious proxy service Faceless.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE