Intel and Arm Macs are being targeted by New ‘Cuckoo’ Persistent macOS Spyware

Intel and Arm Macs are being targeted by New ‘Cuckoo’ Persistent macOS Spyware
A new information thief that targets Apple macOS systems has been found by cybersecurity researchers. It is intended to become persistent on infected hosts and function as spyware. The malware, which Kandji dubbed Cuckoo, is a universal Mach-O binary that runs on Macs with Intel and Arm processors.

Although there are hints that the binary is hosted on websites like dumpmedia[.]com, tunesolo[.]com, fonedog[.]com, tunesfun[.]com, and tunefab[.]com seems to offer both free and paid versions of applications dedicated to ripping music from streaming services and converting it into MP3 format, the precise distribution vector is currently anonymous.
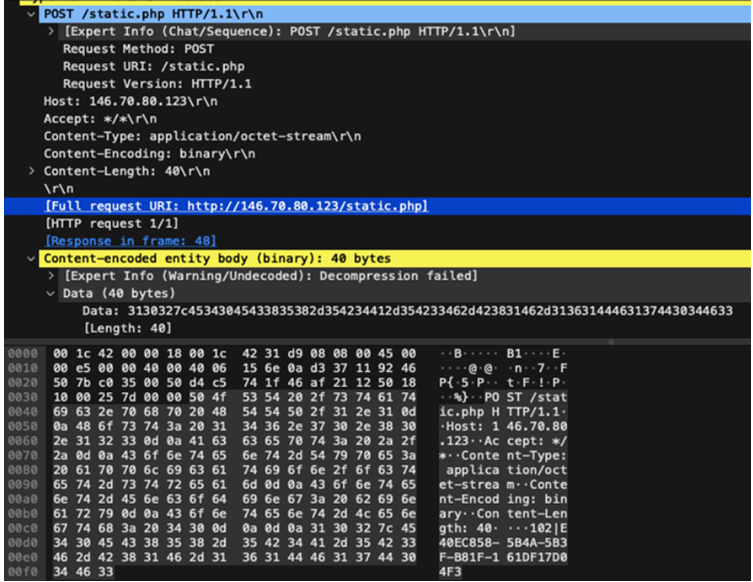
The disk image file that was downloaded from the websites is in charge of starting a bash shell to collect host data and confirm that the computer that was compromised is not situated in Russia, Ukraine, Belarus, Armenia, or Kazakhstan. Only if the locale check is successful is the malicious binary run.
Additionally, it achieves persistence through a LaunchAgent—a tactic previously employed by other malware families, including ZuRu-overlapping macOS backdoors, XLoader, RustBucket, and JaskaGO. Similar to the MacStealer macOS stealer virus, Cuckoo uses osascript to display a phony password prompt and fool users into entering their credentials to escalate their privileges.

Adam Kohler & Christopher Lopez (Researchers)
| “This malware queries for specific files associated with specific applications, in an attempt to gather as much information as possible from the system.” |
It can execute several instructions to gather data from iCloud Keychain, Apple Notes, web browsers, cryptocurrency wallets, and applications like Discord, FileZilla, Steam, and Telegram. It can also gather hardware information, take screenshots, record processes that are presently running, and search for installed programs.
Adam Kohler & Christopher Lopez (Researchers)
| “Each malicious application contains another application bundle within the resource directory.” “All of those bundles (except those hosted on fonedog[.]com) are signed and have a valid Developer ID of Yian Technology Shenzhen Co., Ltd (VRBJ4VRP).” |
Researchers
| “The website fonedog[.]com hosted an Android recovery tool among other things; the additional application bundle in this one has a developer ID of FoneDog Technology Limited (CUAU2GTG98).” |
The revelation follows the discovery of another stealer software, called CloudChat, by the Apple device management firm over a month ago. This malware can trick macOS users whose IP addresses do not geolocate to China by posing as a private messaging program.
The malware obtains information linked to Google Chrome wallet extensions and crypto private keys that have been copied to the clipboard.
It also comes after the discovery of a new Go-written version of the infamous AdLoad virus, known as Rload (also known as Lador), which is only produced for Intel x86_64 architecture and is designed to avoid detection by Apple’s XProtect malware signature list.
Phil Stokes, Security Researcher, SentinelOne, Report, Last Week,
| “The binaries function as initial droppers for the next stage payload,” adding the specific distribution methods remain presently obscure. |
Also Read What is Digital Arrest & How Do People Lose Money Due to Fake Police? Beware!
Having said that, these droppers are usually found integrated into trojanized or cracked software that is posted on malicious websites.
AdLoad is a well-known adware campaign that has been plaguing macOS users since at least 2017. It uses an adversary-in-the-middle web proxy to reroute user traffic through the attacker’s own infrastructure to hijack search engine results and insert advertisements into websites for financial gain.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for the News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Read More Article Here






