Implantation of the Offensive Lua Backdoor on Many Devices via Cisco Zero-Day Exploitation

Implantation of the Offensive Lua Backdoor on Many Devices via Cisco Zero-Day Exploitation
Cisco has issued a warning regarding a recently discovered zero-day vulnerability in IOS XE. This vulnerability has been actively exploited by an unidentified threat actor, who has utilized it to deliver a
The vulnerability, identified as CVE-2023-20273 with a CVSS score of 7.2, pertains to a privilege escalation weakness found in the online user interface functionality. It has been observed to be utilized in conjunction with CVE-2023-20198 as a component of an exploit chain.
According to a recently revised advisory published on Friday, Cisco reported that the assailant initially exploited CVE-2023-20198 in order to acquire initial access. Subsequently, the attacker executed a privilege 15 command to establish a local user and password combination. This feature enabled the user to authenticate and gain access to the system using standard user privileges.
The assailant proceeded to exploit an additional element of the web user interface functionality, utilizing the recently acquired local user privileges to escalate their authority to the root level and successfully save the malicious software onto the file system. This vulnerability has been designated with the identifier CVE-2023-20273.
According to a representative from Cisco, a solution addressing both vulnerabilities has been developed and will be provided to customers commencing on October 22, 2023. During the interim period, it is advisable to deactivate the HTTP server functionality.
Cisco has previously acknowledged that a security fault in its software, which has since been fixed, was exploited to install a backdoor. However, in light of the recent revelation of a new zero-day vulnerability, the company has determined that the previously identified vulnerability is no longer connected to the observed activity.
According to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), the vulnerabilities in question could potentially be leveraged by an unauthorized remote actor to gain control over a system that is impacted by these flaws. These vulnerabilities enable the perpetrator to establish a privileged account that grants full control over the device.
The defects, if successfully exploited, have the potential to enable attackers to acquire unrestricted remote access to routers and switches, monitor network traffic, manipulate and redirect network traffic, and establish a persistent presence within the network. This is mostly owing to the absence of adequate protective measures for these devices.
The emergence of this situation coincides with the discovery that a considerable number of around 41,000 Cisco equipment, which operate on the susceptible IOS XE software, have potentially fallen victim to unauthorized access by malicious individuals using the two identified security vulnerabilities. This information has been obtained from data provided by Censys and LeakIX.
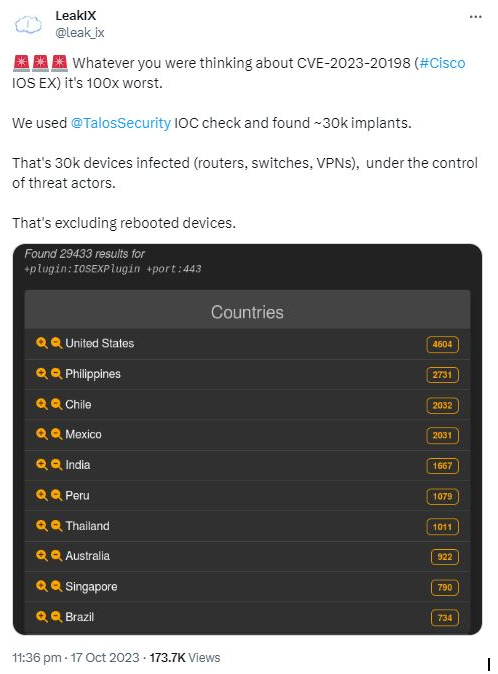
According to the attack surface management organization, the quantity of hacked Cisco devices has decreased to 36,541 as of October 19th. The main targets of this vulnerability are not predominantly huge organizations, but rather smaller entities and individuals.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article Here






