How to Keep Your Business A float in a Tense Situation?

Establishing thorough plans for threat preparedness, mitigation, and response is crucial for firms implementing cybersecurity rules and cyber event reporting requirements into their security protocols.
Your vital systems and operating technology are the foundation of your company. Because of this, cybercriminals will be more interested in
- Taking Advantage of These Weaknesses,
- Compromising Your Data, and
- Demanding Ransom Payments.
Safeguarding your company is critical in the current environment, which is marked by the constant threat of ransomware attacks and the difficulties presented by disjointed security solutions. Here is where the National Institute of Standards and Technology (NIST) promotes the creation of robust security systems that are able to anticipate, withstand, and recover from cyberattacks.
We’ll look at ways to strengthen your defenses against online attacks and guarantee continuous operations in this article. Proactive cybersecurity pioneer Fidelis Security is here to support you during this journey.
Prepare
- Compliance and Regulatory Compliance:#
Adhering to industry-specific and government rules is non-negotiable, making compliance especially important in regulated businesses. The Compliance Management solutions offered by Fidelis Security give businesses the controls and monitoring tools they need to be compliant with changing regulations.
Sustaining compliance in a world of ever-changing regulations can be a difficult undertaking. Fidelis Security offers complete Compliance Management solutions that make this difficulty easier to handle.
These solutions provide the controls and monitoring tools required to make sure businesses follow industry- and government-specific rules. By staying in compliance, they improve their overall cybersecurity posture in addition to avoiding possible penalties.
Analysts can locate information on the network that is governed by regulatory compliance statutes, such as PCI, HIPAA, FISMA, GLBA, and FERPA, in addition to PII, intellectual property, finance-related, confidential, or secret information, thanks to Fidelis Security’s
- Patented Deep Session Inspection (DSI) and
- Real-Time Traffic Analysis.
Analysts can match these kinds of content along with any other content they consider sensitive by utilizing pre-built data leakage protection (DLP) or custom-built policies. Network prevention can be activated to halt exfiltration in the process, which could have been initiated by an insider threat or a malevolent actor.
- Continuous Monitoring and Threat Detection:#
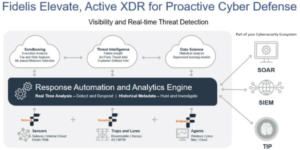
Proactive cybersecurity strategies require both ongoing monitoring and real-time threat identification. The Network Detection and Response (NDR) solutions from Fidelis Security enable enterprises to recognize and react to threats instantly by providing enhanced threat detection capabilities and continuous monitoring.
The capacity to continuously monitor networks and identify potential dangers in real time is crucial in the face of ever-changing cyber threats. The Network Detection and Response (NDR) products from Fidelis Security are made to continuously monitor endpoints and networks.
In order to recognize and address such risks before they become more serious, these systems make use of sophisticated threat detection capabilities. Organizations can take the initiative in the ongoing fight against cyberattacks using Fidelis NDR.
To achieve real-time detection and reaction, Fidelis NDR makes use of a variety of features across the board. Network and mail sensors use the following techniques to offer a multifaceted approach to network-based detection:
- Deep Packet Inspection (DPI),
- DNS Protocol Anomaly Detections,
- Deep Session Inspection (DSI)
- Decoding,
- Antivirus Detection (AV), and
- Other Techniques.
The Fidelis Collector is used for event and sequence-based detections, as well as anomaly detections. It is a real-time database that gathers all decoded session and object metadata that is gathered as it moves over the network.
Furthermore, on endpoints where an agent is installed, Fidelis Endpoint finds harmful items, traffic patterns, and behaviors.
You can design deception layers that complement your real network architecture with the help of Fidelis Deception.
These tiers are intended to detect and follow malware and hackers as they try to enter your network covertly. Decoys and breadcrumbs are placed deliberately to improve the security posture of your network.
With this strategy, you can protect your assets and gain more insight in places where traditional security agents cannot be used, like
- Enterprise IoT,
- Shadow IT, and
- Legacy Systems.
Consequently, you are able to identify and eliminate risks inside your network in a proactive manner, shielding your company from possible damage. Lastly, to discover bad actors early in the threat lifecycle rather than after the fact, the Fidelis Threat Research Team supplies each of these platforms with timely intelligence in the form of threat intelligence feeds and detection policies.
Analysts at the Fidelis CommandPost are notified of any detections so they can take quick action.
Mitigate#
- Vulnerability Management:#
Reducing security threats is mostly dependent on vulnerability management. It entails locating and fixing holes in the IT infrastructure. The Vulnerability Management solutions from Fidelis Security provide a strong method for locating and ranking weaknesses, assisting companies in strengthening their defenses.
Cybercriminals may use IT infrastructure vulnerabilities as access points into systems. Fidelis Security’s Vulnerability Management solutions enable enterprises to efficiently detect and prioritize vulnerabilities in order to tackle this threat.
They strengthen their defenses and lower security risks by resolving infrastructure deficiencies, which improves their cybersecurity posture in the end.
- Insider Threat Mitigation:#
Insider occurrences pose a serious risk, regardless of their intentionality or inadvertence. Maintaining business continuity requires reducing these risks. The Data Loss Prevention (DLP) solution from Fidelis Security is made to guard against insider threats by spotting odd activity and preventing unauthorized access to sensitive information.
Insider threats pose a complicated issue with potentially devastating effects. Fidelis DLP offers a comprehensive method of reducing these risks by preventing unauthorized access to and exfiltration of sensitive data.
Respond#
- Incident Response and Recovery Planning:#
Plans for incident reaction and recovery are essential during a cyber emergency. When it comes to developing and carrying out successful reaction plans and guaranteeing prompt and effective actions when it matters most, Fidelis Security’s Incident reaction solutions are their first choice.
In the world of cybersecurity, incidents happen “when” rather than “if.” It’s critical to be ready to act quickly and decisively. The incident response solutions offered by Fidelis Security are made to assist businesses in developing and putting into action efficient response strategies.
These procedures serve as an organization’s lifeline during emergencies, guaranteeing that they can act quickly and effectively to contain and lessen the effects of cyber catastrophes.
- The Fidelis Challenge:#
Fidelis Security advances cybersecurity by bringing knowledge and dedication to the fore. They really think they have the best viewpoint on cyber threats. Organizations are encouraged to take the Fidelis Challenge as evidence of this.
They can include Fidelis Elevate into your corporate environment for a duration of thirty days, during which time Fidelis Security will demonstrate its unmatched ability to detect threats. Fidelis Security is sure that businesses will realize the impact they can have in protecting their establishments. It’s free to try.
Conclusion
Cyber incidents may have an effect on public safety, economic stability, and national security. As a result, businesses should give their critical infrastructure security top priority. The primary takeaways from this manual underscore the significance of strong cybersecurity protocols in preserving uninterrupted operations.
It is recommended that organizations prioritize their cybersecurity endeavors and utilize specialized knowledge to identify appropriate, customized solutions for their security requirements, thereby strengthening their defenses against constantly changing threats.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security.
Read More Article Here