How to Crack Passwords Using John The Ripper?

How to Crack Passwords Using John The Ripper?
John the Ripper is a widely used software tool for breaking passwords. John endorses a wide range of encryption methods for Windows and Unix platforms, including Mac.
An outstanding characteristic of John is its ability to automatically recognize the encryption used in popular formats. This will significantly reduce the amount of time you spend on researching the various hash types and hunting for the appropriate program to decrypt them.
John is a tool that relies on a dictionary for its functionality. This implies that it operates by utilizing a compendium of frequently used passwords to juxtapose it with the given hash. Presented here is a widely used password compilation known as rockyou.txt.
Although the RockYou wordlist is widely used, John also has its own collection of wordlists with numerous commonly used passwords. John’s proficiency in breaking systems with weak passwords greatly enhances his effectiveness.
This is how John works by default:
- Identify the form of hash utilized by the current hash.
- Produce hashes dynamically for every password contained within the dictionary.
- Stop when the current hash is matched by a newly generated hash.
John acquires passwords in additional ways besides this. John can also be modified to suit your specific needs. For instance, the format of the password can be specified via the —— format flag.
This article commences with the installation of John and then proceeds with an exposition of the various modalities that can be employed. John will subsequently be employed to decipher passwords for three distinct use cases: Linux, Windows, and compressed files.
How to Install John the Ripper?
If you are using Kali Linux, John is pre-installed. You can use John by typing the following command:
$ john
For Ubuntu/Debian, you can get John from the apt source. Here is the command to install John in Ubuntu:
$ apt install John
In Mac, you can find John in Homebrew:
$ brew install john
For Windows and other operating systems, you can find the binaries here.
Utilize the help command once John has been installed to verify that the installation is functioning properly. Similarly, when collaborating with John, the help command may be utilized as a reference.
$ john -h
Here is the output of the help command:
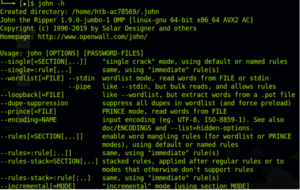
John help command
How to Use John the Ripper?
Having established the nature of John, we shall now examine the three modalities it provides. One of these three will be utilized for the majority of your use cases.
- Single crack mode
- Wordlist mode
- Incremental mode
Let’s look at each one of them in detail.
What is Single Crack Mode?
In single-crack mode, John takes a string and generates variations of that string in order to generate a set of passwords.
For example, if our username is “stealth” and the password is “StEaLtH”, we can use the single mode of John to generate password variations (STEALTH, Stealth, STealth, and so on).
We use the “format” flag to specify the hash type and the “single” flag to let John know we want to use the single crack mode. We will also create a crack.txt file which will contain the username and the hash value of the password.
stealth:d776dd32d662b8efbdf853837269bd725203c579
Now we can use the following command to use John’s single crack mode:
$ john –single –format=raw-sha1 crack.txt
And here is the result. You can see that John has successfully found the correct password “StEaLtH”.
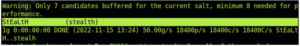
John single crack mode
What is Dictionary Mode?
In dictionary mode, we will provide John with a list of passwords. John will generate hashes for these on the fly and compare them with our password hash.
For this example, we will use the RockYou wordlist. If you are using Kali, you can find it at /usr/share/wordlists/rockyou.txt. We will also have a crack.txt file with just the password hash.
edba955d0ea15fdef4f61726ef97e5af507430c0
Here is the command to run John in dictionary mode using the wordlist.
$ john –wordlist=/usr/share/wordlists/rockyou.txt –format=raw-sha1 crack.txt
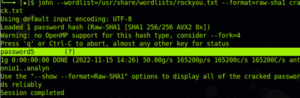
John wordlist mode
The weaker the password is, the quicker John can figure it out. This is why it is always recommended to have strong passwords.
What is Incremental Mode?
Incremental mode is the most powerful mode provided by John. It tries all possible character combinations as passwords.
This sounds great, but there is a problem. The cracking can go on for a long time if the password is too long or if it’s a combination of alphanumeric characters and symbols.
You will rarely use this mode unless you have no other option. In typical cases, a combination of Social Engineering attacks and wordlist mode will help you crack most of the hashes.
If you would like to try the incremental mode, here is the syntax.
$ john -i:digits passwordflle.txt
Here, the -i flag tells John that we want to use the increment mode. The “digits” placeholder can be used to set the maximum number of digits in the password.
You can also add the “format” option to make it easier for John to start cracking.
Use Cases for John the Ripper
Now that you understand the different modes of John, let’s look at a few use cases.
We will use John to crack three types of hashes:
- A Windows NTLM password,
- A Linux shadow password, and
- The password for a zip file.
How to Crack a Windows Password?
Let’s start with Windows. In Windows, the password hashes are stored in the SAM database. SAM uses the LM/NTLM hash format for passwords, so we will be using John to crack one.
Getting passwords from the SAM database is out of scope for this article, but let’s assume you have acquired a password hash for a Windows user.
Here is the command to crack it:
$ john –format=lm crack.txt
The crack.txt will contain the password hash. If John is unable to crack the password using its default wordlist, you can use the RockYou wordlist using the — — wordlist flag.
The crack.txt will contain the password hash. If John is unable to crack the password using its default wordlist, you can use the RockYou wordlist using the — — wordlist flag.
$ unshadow /etc/passwd /etc/shadow >output.db
This command will combine the files together and create an output.db file. We can now crack the output.db file using John.
$ john output.db
John tries to find the password for all the users in the passwd file
and generates the output with the list of cracked passwords. Again, you can use custom wordlists via the — — wordlist flag.
How to Crack a Zip File Password?
Finally, let’s crack a zip file password. To do that, we first have to get the hash of the zip file’s password.
Like Unshadow, John has another utility called zip2john. zip2john helps us to get the hash from zip files. If you are cracking a .rar file, you can use the rar2john utility.
Here is the syntax to get the password hash of a zip file:
$ zip2john flle.zip >zip.hashes
The above command will get the hash from the zip file and store it in the zip.hashes file. You can then use John to crack the hash.
$john zip.hashes
How News4Hackers Can Help?
As we all know, News4Hackers is a leading cybersecurity information and news-providing organization that helps its readers get ground-breaking information on the latest trends, techniques, technologies, and cyber attacks on diverse organizations worldwide. Our news collectors keep their 24X7 eyes on the lookout for the happening news in the technology world to provide them to you with utmost urgency.
In addition to this, Craw Security is the sister company of News4Hackers, which is the top-notch cybersecurity training provider in India and other prominent nations throughout the world. You can give them a call at their hotline mobile number +91-9513805401 to clear any doubts related to the upcoming batches of their best cybersecurity training programs or any other related stuff to cyber security.
READ MORE ARTICLE HERE






