Google Makes Setting Up 2-Factor Authentication Easier

Google Makes Setting Up 2-Factor Authentication Easier
Google stated on Monday that customers with personal and Workspace accounts will find it easier to use two-factor authentication (2FA). Also known as 2-Step Verification (2SV), its goal is to fortify users’ accounts with an additional layer of security to thwart takeover attempts if passwords are compromised.
To avoid using the less secure SMS-based authentication, the new modification requires adding a second-step method—such as an authenticator app or a hardware security key—before turning on 2FA.

| “This is particularly helpful for organizations using Google Authenticator (or other equivalent time-based one-time password (TOTP) apps).” “Previously, users had to enable 2SV with a phone number before being able to add Authenticator.” |
To link hardware security keys to their accounts, users can either register a FIDO1 credential on the key or assign a passkey, which is a FIDO2 credential, to one. Google warns that if the admin policy for “Allow users to skip passwords at sign-in by using passkeys” is disabled, Workspace accounts might still need to input their passwords in addition to their passkey.
Another important enhancement is that users’ enrolled second steps will no longer be immediately erased if they choose to disable 2FA in their account settings.
| “When an administrator turns off 2SV for a user from the Admin console or via the Admin SDK, the second factors will be removed as before, to ensure user off-boarding workflows remain unaffected.” |
This development coincides with Google’s announcement that, during the previous year, over 400 million Google accounts had begun to use passkeys forzn.
Instead of using passwords, which are easily stolen by credential harvesting or stealer malware, modern authentication methods and standards like FIDO2 use cryptographic keys generated by and linked to smartphones and computers to verify users. This makes them resistant to phishing and session hijacking attacks.

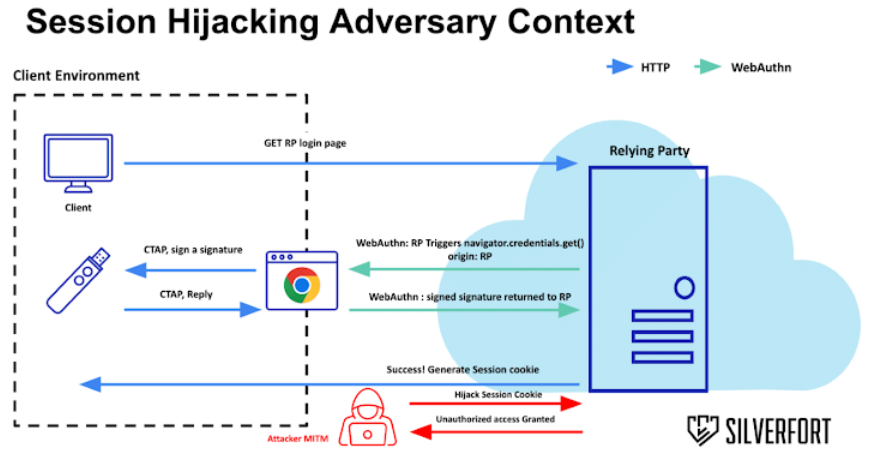
However according to recent research from Silverfort, a threat actor may circumvent FIDO2 by setting up an adversary-in-the-middle (AitM) attack, which could take control of user sessions in programs that make use of single sign-on (SSO) services like Yubico, Microsoft Entra ID, and PingFederate.
Dor Segal, Security Researcher
| “A successful MitM attack exposes the entire request and response content of the authentication process.”
“When it ends, the adversary can acquire the generated state cookie and hijack the session from the victim. Put simply, there is no validation by the application after the authentication ends.” |
Because most systems do not secure the session tokens issued upon successful authentication, unauthorized access can be gained by a malicious actor. This makes the attack viable.
Furthermore, no validation is done on the device requesting the session, therefore the cookie can be used by any device until it expires. This allows the cookie to be obtained by an AitM attack, so avoiding the authentication stage.
It is recommended to utilize a technique called token binding, which enables services and applications to cryptographically link their security tokens to the Transport Layer Security (TLS) protocol layer, to guarantee that the authenticated session is used only by the client.
Token binding is exclusive to Microsoft Edge, but to assist guard against session cookie theft and hijacking attempts, Google last month announced the addition of Device Bound Session Credentials (DBSC) to Chrome.
About The Author
Suraj Koli is a content specialist with expertise in Cybersecurity and B2B Domains. He has provided his skills for the News4Hackers Blog and Craw Security. Moreover, he has written content for various sectors Business, Law, Food & Beverage, Entertainment, and many others. Koli established his center of the field in a very amazing scenario. Simply said, he started his career selling products, where he enhanced his skills in understanding the product and the point of view of clients from the customer’s perspective, which simplified his journey in the long run. It makes him an interesting personality among other writers. Currently, he is a regular writer at Craw Security
READ MORE ARTICLE HERE






