Dirb: The Widely Recognized Web Content Scanner

Dirb: The Widely Recognized Web Content Scanner
What is DIRB?
DIRB is a Web Content Scanner. It looks for existing (and/or hidden) Web Objects. It basically works by launching a dictionary-based attack against a web server and analyzing the response.
It comes with a set of preconfigured attack wordlists for easy usage but you can use your custom wordlists. Also, DIRB sometimes can be used as a classic CGI scanner, but remember is a content scanner, not a vulnerability scanner.
dirb
-a <agent_string> : Specify your custom USER_AGENT.
-c <cookie_string>: Set a cookie for the HTTP request.
-f Fine tunning of NOT_FOUND (404) detection.
-H <header_string>: Add a custom header to the HTTP request.
-i Use case-insensitive search.
-l Print the “Location” header when found.
-N <nf_code>: Ignore responses with this HTTP code.
-o <output_file> : Save output to disk.
-p <proxy[:port]> : Use this proxy. (Default port is 1080)
-P <proxy_username:proxy_password> : Proxy Authentication.
-r Don’t search recursively.
-R Interactive recursion. (Asks for each directory)
-S Silent Mode. Don’t show tested words. (For dumb terminals)
-t Don’t force an ending ‘/’ on URLs.
-u <username:password> : HTTP Authentication.
-v Show also NOT_FOUND pages.
-w Don’t stop on WARNING messages.
-X <extensions> / -x <exts_file> : Append each word with this extensions.
-z Add a milliseconds delay to not cause excessive Flood.
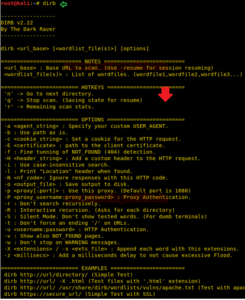
Utilizing Multiple Wordlists for Directory Traversing
The above attack works by using the default wordlist_files common.txt, but we can change this word list and select another wordlist for directory traversal.
cd /usr/share/wordlists/dirb
ls –la cd /usr/share/wordlists/vulns
ls –la
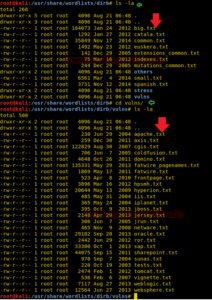
Default working of Dirb
In this attack the common.txt is set as a default word list for directory traversal, the protester can use the following command. Open the terminal and type the following command to start the Brussels Directory attack.
dirbhttp://192.168.1.137/dvwa/
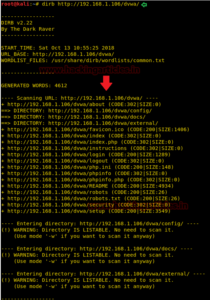
Enumerating Directory with Specific Extension List
There are a lot of situations where we need to extract the directories of a specific extension over the target server, and then we can use the -X parameter of the dirb scan. This parameter accepts the file extension name and then searches the given extension files over the target server or machine.
dirb http://192.168.1.106/dvwa/ -X .php
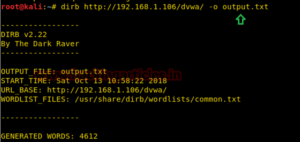
Save Output to Disk
We save the output of the dirb scan onto a file. To this, we will use the parameter -o of the dirb scan we can save the output of the dirb scan in a text file.
dirb http://192.168.1.106/dvwa/ -o output.txt

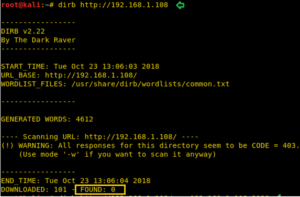
Default Working Vs Nonstop on WARNING messages Working
During the normal dirb scan as shown below, some of the pages generate warnings; the dirb scan skips those directories where it encounters any warnings.
dirb http://192.168.1.106/
While doing a scan that is to be done very deeply and verbosely, we want the dirb scan to not avoid these warnings and do an in-depth scan, hence we use the -w parameter of the dirb scan.
dirb http://192.168.1.106/ -w
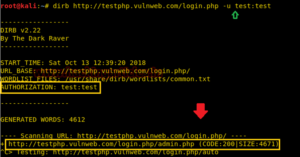
HTTP AUTHORIZATION (-u username: password)
HTTP Authentication/Authentication mechanisms are all based on the use of 401-status code and WWW-Authenticate response header. The most widely used HTTP authentication mechanisms are Basic.
dirb http://testphp.vulnweb.com/login.php -u test:test
Proxy URL
Using the –p option enables proxy URL to be used for all requests, by default it works on port 1080. As you can observe, on exploring the target network IP in the web browser it put up an “Access forbidden error” which means this web page is running behind some proxy.
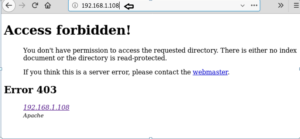

dirb http://192.168.1.108 –p 192.168.1.108:3129
How News4Hackers Can Help?
News4Hackers is a global news organization that specializes in providing informative and useful articles on topics related to cybersecurity. Furthermore, News4Hackers is dedicated to delivering current information to our audience regarding the latest advancements, methodologies, technologies, and cyber threats that are explicitly engineered to compromise organizations on a global scale. Daily, our news organizers remain watchful for the latest technological advancements with the intention of promptly furnishing you with them.
Additionally, it is noteworthy to mention that Craw Security maintains a collaboration with News4Hackers, a reputable organization specializing in cybersecurity, to offer perceptive analysis and viewpoints on numerous consequential countries, including India. For additional information regarding their highly effective cybersecurity training courses or any other related topic, please reach out to them at the provided calling number: +91-9513805401.
READ MORE ARTICLE HERE