225,000+ Compromised ChatGPT Credentials Are For Sale On Dark Web Marketplaces
225,000+ Compromised ChatGPT Credentials Are For Sale On Dark Web Marketplaces
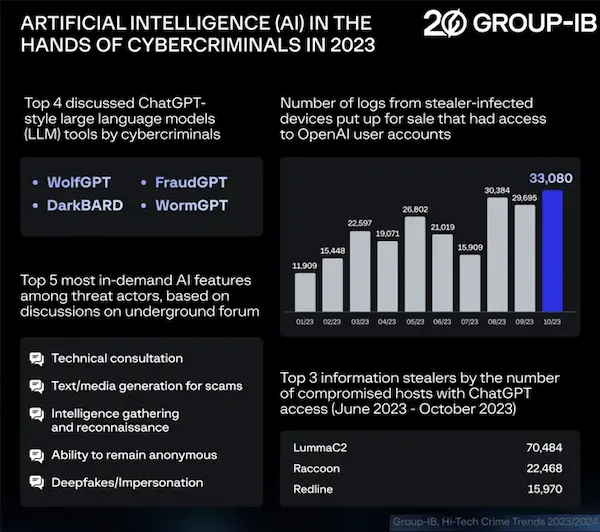
From January to October 2023, more than 225,000 logs comprising stolen OpenAI ChatGPT credentials were sold on clandestine markets, according to new research from Group-IB.

The information stealer records pertaining to the LummaC2, Raccoon, and RedLine stealer malware contained these credentials.
“The number of devices with infections declined slightly in mid and late summer, but increased dramatically between August and September,” the cybersecurity firm headquartered in Singapore wrote in its last week-published Hi-Tech Crime Trends 2023/2024 report.
More than 130,000 distinct hosts with the ability to use OpenAI ChatGPT were compromised between June and October 2023, representing a 36% increase compared to the data collected in the initial five months of 2023. The following is a breakdown of the top three stealer families:
- LummaC2 – 70,484 hosts
- Raccoon – 22,468 hosts
- RedLine – 15,970 hosts

“The sharp growth in the amount of ChatGPT credentials for sale is due to the overall spike in the number of hosts infected with information stealers, data from which is then put up for sale on markets or in UCLs,” according to Group-IB.
Microsoft and OpenAI have disclosed that nation-state actors from China, Russia, North Korea, and Iran are integrating large language models (LLMs) and artificial intelligence (AI) into their ongoing cyber attack operations. This development coincides with these revelations.
Group-IB stated that adversaries may employ LLMs to devise novel strategies, construct convincing phishing and scam attacks, and enhance operational efficiency. Furthermore, the technology may facilitate the execution of hacking toolkits, expedite reconnaissance processes, and enable fraudulent robocalls.

“In the past, [threat actors] were primarily focused on corporate computers and in systems that had access that permitted movement across the network,” the report stated. “They now concentrate on devices that have access to public AI systems as well.”
“This provides them the ability to view logs with the communication history between personnel and structures, which they may employ to conduct searches for sensitive information (for spying reasons), details about internal infrastructure, authentication details (for carrying out more serious attacks), and information about application source code.”

A leading access technique has become the misuse of legitimate account credentials by threat actors; this is primarily due to the ease with which such information can be obtained via stealer malware.
“The mixture of a surge in info stealers and the unlawful use of legitimate login information to obtain initial access has worsened guardians’ identity and access management challenges,” IBM X-Force reported.

“An enterprise credential data can be obtained from hacked devices by means of credential reuse, browser credential stores, or obtaining enterprise accounts right from personal devices.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.





