‘Auto-Color,’ A New Linux Malware that Allows Hackers Complete Remote Access to Compromised Systems

‘Auto-Color,’ A New Linux Malware that Allows Hackers Complete Remote Access to Compromised Systems
According to recent research from Palo Alto Networks Unit 42, between November and December 2024, universities and government agencies in North America and Asia were the target of Auto-Color, a Linux malware that had not yet been published.
In a technical description of the malware, security researcher Alex Armstrong stated, “Once installed, Auto-color gives threat actors complete remote access to compromised machines, making it very difficult to remove without specialized software.”
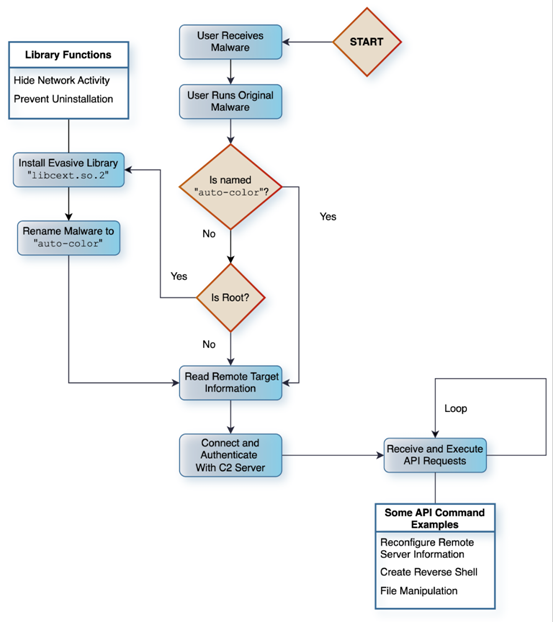
The name “auto-color” comes from the file name that the initial payload changes after installation. Although how it accomplishes its goals is unknown at this time, it is known that the victim must specifically run it on their Linux computer.
One noteworthy feature of the malware is the variety of strategies it uses to avoid detection. This involves hiding command-and-control (C2) connections, utilizing ostensibly harmless file names like door or egg, and using proprietary encryption algorithms to hide configuration and communication data.
It installs a malicious library implant called “libcext.so.2,” copies and renames itself to /var/log/cross/auto-color, and modifies “/etc/ld.preload” to create persistence on the host after being launched with root capabilities.
“If the present user lacks root privileges, the malware will not proceed with the installation of the evasive library implant on the system,” Armstrong stated. “It will proceed to do as much as possible in its later phases without this library.”
By altering “/proc/net/tcp,” a file that includes details on all active network connections, the library implant can passively hook libc functions to intercept the open() system call, which it exploits to conceal C2 interactions. Symbiote, another piece of Linux malware, used a similar tactic.
Additionally, it keeps the malware from being uninstalled by safeguarding “/etc/ld.preload” against additional alteration or deletion.
After that, Auto-color makes contact with a C2 server, which gives the operator the ability to launch programs, create or edit files, spawn a reverse shell, collect system information, use the computer as a proxy for communication between a remote IP address and a particular target IP address, and even uninstall itself using a kill switch.
“Upon execution, the malware attempts to receive remote instructions from a command server that can create reverse shell backdoors on the victim’s system,” Armstrong explained. “The threat actors separately compile and encrypt each command server IP using a proprietary algorithm.”
Malware C2 API Functionality
The complete API and its primary capability categories are briefly described in this section. Table 1 lists all of the command ID values that are grouped together along with their primary functions. XX is a placeholder value that is used to group the things together, and each command ID will be provided in hex format.
| Command IDs | Category Name | Description |
| 0, 1, 2, 3, 0xF | General options and kill switch | Sends host information and includes a kill switch to uninstall itself from the system |
| 0x100 | Reverse shell | Creates a reverse shell for the remote server to interact with the victim machine directly |
| 0x2XX | File operations and manipulation | Create and/or modify files and execute programs locally |
| 0x300 | Network Proxy | The infected machine will act as a middleman proxy for any connections between the remote target and the IP address given in the argument |
| 0x4XX | Global payload manipulation | Sends and manipulates global configuration data mentioned previously |
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blogs, he also writes for brands including Craw Security, Bytecode Security, and NASSCOM.
READ MORE HERE