APT33: A Deeper Dive into a Famous Cyber Espionage Group

APT33: A Deeper Dive into a Famous Cyber Espionage Group
Introduction:
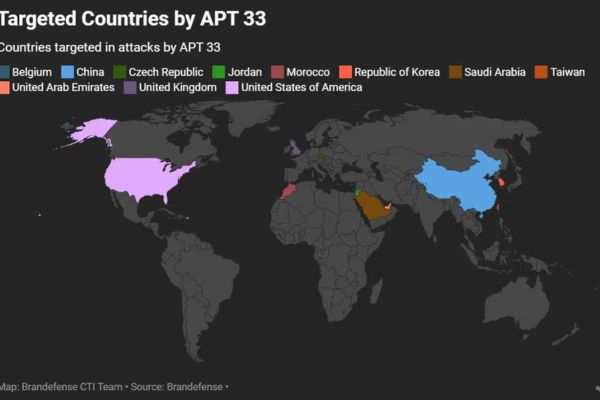
The prominent Advanced Persistent Threat (APT) group known as APT33 is also known by a number of other names, including Refined Kitten, Elfin, and Magnallium. An advanced persistent threat (APT33) that is believed to have connections to the Iranian government has been operating since at least 2013, attacking businesses in a variety of industries all around the world. Geopolitical considerations are the primary impetus behind the activities of the group, with a particular emphasis on cyber espionage and various disruptive operations.

Main Features
Advanced persistent threat (APT33) is distinguished by its sophisticated and persistent nature. Among the most notable characteristics of this APT group are the following:
| Sophisticated Malware | When it comes to designing and delivering sophisticated malware, APT33 is well-known. DropShot and Shamoon are two examples of the unique malware families that are included in their toolkit. It is particularly infamous for its destructive characteristics, which include the ability to delete data and render systems useless. Shamoon is this particular virus. |
| Persistent Attacks | Long-term campaigns are carried out by APT33, which allows it to keep access to infiltrated networks for considerably longer periods of time. Through the use of this permanent access, they are able to acquire intelligence and, in some instances, prepare for attacks that are devastating. |
| Targeted Phishing Campaigns | In order to launch its attacks, the organization typically uses spear-phishing emails as its initial vector. The appearance of these emails is meticulously created to give the impression that they are authentic. However, they frequently contain dangerous attachments or links that, when clicked on, launch malware. |
| Advanced Evasion Techniques | A variety of evasion strategies are utilized by APT33 in order to evade detection. The use of legitimate tools for malevolent objectives, the utilization of hacked credentials, and the implementation of strategies to circumvent antivirus and other security measures are all examples of this. |
Historical Context
It was around the year 2013 when APT33 first came to public attention, but it is likely that its actions began earlier. The operations of the group are intricately connected to Iran’s geopolitical goals, notably in the context of wars in the area and tensions with countries in the West. Over the course of its existence, the Advanced Persistent Threat (APT33) has endeavored to acquire intelligence, steal intellectual property, and, in certain instances, disrupt operations by focusing on businesses that are strategically significant to Iran.
Other Known Names
APT33 is also referred to by several other names in the cybersecurity community:
- Refined Kitten: The group’s relationship with Iran is reflected in the appellation since many advanced persistent threats (APT) groups with ties to Iran frequently get referred to as “Kittens.”
- Elfin: Symantec’s way of describing the group, emphasizes their stealthiness and agility.
- Magnalium: This is yet another name that Dragos uses, and it highlights the connection between the gang and attacks on industrial control systems (ICS).
Typical Techniques
A number of different strategies are utilized by APT33 in order to accomplish its goals. The following are some of the most often-used methods:
Spear Phishing
The spear-phishing emails that contain malicious attachments or URLs are frequently used as the starting point for APT33’s activities. Emails like these are sent with the intention of taking advantage of human weaknesses and gaining early access to specific networks being targeted.
Credential Dumping
APT33 makes use of tools such as Mimikatz to harvest credentials once it has gained access to a network. This gives them the ability to increase their privileges and move laterally anywhere within the network.
Exploitation of Vulnerabilities
In order to obtain access or increase their privileges, the gang makes use of known flaws in software and information systems. As a result of the fact that they are known to target systems that have not been patched, timely updates are extremely important.
Data Exfiltration
APT33 is exceptionally competent in the art of silently removing sensitive material from networks that have been infiltrated. They frequently make use of encrypted channels and genuine technologies in order to blend in with the typical activity on the network.
Destructive Attacks
Additionally, APT33 has been active in destructive attacks, primarily through the utilization of the Shamoon virus. This is in addition to their involvement in espionage. It is possible for these attacks to result in severe data loss as well as disruptions to operations.
Key Incidents
It has been determined that APT33 is responsible for a number of high-profile incidents, which demonstrates its capabilities and objective:
| Shamoon Attacks | The virus known as Shamoon is one of the most notorious tools that APT33 possesses in its arsenal. Shamoon is a destructive wiper malware that was identified for the first time in 2012 and has been utilized in successive waves. It has caused enormous harm, particularly in the energy sector. One of the most significant examples is the attack that took place in 2012 against Saudi Aramco, which resulted in the deletion of data from around 30,000 systems. |
| Aerospace Targeting | During the year 2017, it was claimed that APT33 had targeted a number of companies operating in the aerospace industry, particularly those organizations that have connections to Saudi Arabia and the United States. The overarching objective of this attack was to steal sensitive information and valuable intellectual property that was associated with aviation technology. |
| Supply Chain Attacks | In addition, APT33 has been responsible for supply chain attacks, in which it has compromised smaller businesses in order to obtain access to larger targets that are more protected. They are able to infiltrate networks in a manner that is indirect and frequent with less initial examination because of this strategy. |
Evolving Techniques
The strategies that APT33 uses are constantly being improved in order to stay one step ahead of detection measures and to increase its attack capabilities. Among their ever-evolving strategies are the following:
- Living off the Land: A growing number of legitimate administrative tools and procedures are being utilized by APT33 within their compromised settings. They decrease the possibility of discovery by utilizing tools such as PowerShell and PsExec, which are often utilized in information technology environments.
- Modular Malware: Malware developed by the organization has become increasingly modular, which enables them to tailor their payloads to specific targets and purposes through modification. It is also possible to circumvent conventional signature-based detection systems with the help of this modular strategy.
- Cloud and IoT Targeting: APT33 has been focusing its attention on cloud services and Internet of Things devices because it is aware of the growing significance of these platforms. Providing wide access and control over vital systems can be accomplished by compromising cloud infrastructure and Internet of Things devices.
Defensive Measures
Because of the complex nature of APT33’s operations, it is necessary to use a multi-pronged approach in order to protect against their assaults:
- User Education: In light of the fact that spear-phishing continues to be a significant attack vector, it is essential to educate users on how to identify and respond to phishing efforts. The likelihood of successful phishing assaults can be considerably reduced by the implementation of regular training and awareness programs.
- Advanced Threat Detection: By utilizing modern threat detection systems that make use of behavioral analysis, machine learning, and anomaly detection, it is possible to assist in the identification of anomalous activities that are indicative of the strategies employed by APT33.
- Patch Management: It is necessary to have systems that are regularly updated and patched in order to address any identified vulnerabilities. Because APT33 frequently takes advantage of systems that have not been patched, regular updates are an essential defensive strategy.
- Network Segmentation: Within a network, the implementation of network segmentation can restrict the attackers’ ability to move laterally within the network. When firms isolate their most important systems and sensitive data, they are able to lessen the effect of any potential security compromise.
- Incident Response Planning: Having a comprehensive incident response plan in place guarantees that organizations are able to respond to an attack carrying the APT33 malware in a timely and efficient manner. Regular exercises and simulations can be helpful in preparing the response team for situations that could occur in the real world.
Who is at Risk?
The primary targets of APT33 are enterprises operating in industries that Iran considers to be of strategic importance. Among the most high-risk industries are the following:

Aerospace and Defense
Companies that are involved in aerospace and defense are prominent targets because of the confidential data and technologies that they possess. The objective of APT33 is to collect intelligence and cause potential disruptions to operations.
Energy
There is a high frequency of attacks directed at the energy industry, which includes oil and gas corporations. A disruption in the energy infrastructure can have enormous repercussions for both the economy and the geopolitical system.
Manufacturing
It is also possible for manufacturers to be affected, particularly those that are engaged in the production of high-tech equipment. The objective of APT33 is to get their hands on intellectual property and to learn about the latest technical developments.
Healthcare
Organizations in the healthcare industry, such as pharmaceutical firms and research universities, are the targets of attacks because of the important research data and intellectual property they possess.
Government and Military
Government agencies and military groups are high-value targets for spying, which seeks to gather intelligence on capabilities, tactics, and policies. Other targets include military organizations.

Conclusion
When it comes to the cyber world, APT33 continues to be a strong danger. Because of their advanced methods, dogged determination, and readiness to engage in both espionage and destructive activities, they pose a tremendous threat to companies all over the world. In order to reduce the dangers that are posed by APT33 and other advanced persistent threat organizations, it is essential to maintain vigilance, put in place effective cybersecurity measures, and ensure that systems are kept up to date.
READ MORE ARTICLE HERE