APT28 Exploited a Vulnerability in Microsoft Outlook to Compromise Czech and German Entities

APT28 Exploited a Vulnerability in Microsoft Outlook to Compromise Czech and German Entities
Czechia and Germany disclosed on Friday that they had been subjected to an extended cyber espionage campaign carried out by APT28, a nation-state actor affiliated with Russia. The European Union (E.U.), the North Atlantic Treaty Organization (NATO), the United Kingdom (UK), and the United States all condemned the operation.

The Ministry of Foreign Affairs (MFA) of the Czech Republic stated in a statement that unidentified entities within the country were compromised using a Microsoft Outlook security vulnerability that was discovered early last year.
“Cyber attacks hitting political organizations, state institutions, and vital facilities are not only an imminent danger to national security but also disrupt the democratic processes upon which our open society is founded,” according to the MFA.
The contested security vulnerability is CVE-2023-23397, a critical privilege escalation flaw in Outlook that has been rectified. This flaw may enable a malicious actor to gain access to Net-NTLMv2 hashes and subsequently exploit them for a relay attack-based authentication attempt.
The threat actor was linked to a cyber attack targeting the Executive Committee of the Social Democratic Party, according to the German Federal Government (also known as Bundesregierung). The attack exploited a “relatively long period” of time for the same Outlook vulnerability, which enabled the threat actor to “compromise numerous email accounts.”

The campaign specifically targets industry verticals such as logistics, armaments, air and space, IT services, foundations, and associations situated in Germany, Ukraine, and Europe. Furthermore, the Bundesregierung has linked the group to the assault on the German federal parliament (Bundestag) in 2015.
APT28, which the military intelligence agency GRU of the Russian Federation attributes to Military Unit 26165, is additionally monitored by the cybersecurity community at large under the aliases BlueDelta, Fancy Bear, Forest Blizzard (previously Strontium), FROZENLAKE, Iron Twilight, Pawn Storm, Sednit, Sofacy, and TA422.

Microsoft ascribed the hacking group’s abuse of a Microsoft Windows Print Spooler component (CVE-2022-38028, CVSS score: 7.8) as a zero-day exploit to deliver GooseEgg, a previously unidentified custom malware designed to compromise organizations in the education, transportation, government, and Western Europe and North America. The targeted nations included Ukraine, Western Europe, and North America.
The hybrid actions of Russia, according to NATO, “pose a threat to Allied security.” Additionally, the Council of the European Union commented, stating that the “malicious cyber campaign demonstrates Russia’s ongoing pattern of irresponsible cyberspace behavior.”

“Current action by Russian GRU cyber group APT28, like the targeting of the German Social Democratic Party executive, is the most recent instance in an established pattern of behavior by the Russian Intelligence Services that threatens democratic processes across the globe,” the United Kingdom’s government stated.
APT28 has been identified by the U.S. Department of State as having a reputation for “malicious, nefarious, destabilizing, and disruptive behavior.” The DOS stated that it is dedicated to safeguarding the security of its allies and partners, as well as maintaining the rules-based international order, which includes the realm of cyberspace.
A coordinated law enforcement operation in February of this year disrupted a botnet consisting of numerous small office and home office (SOHO) routers located in Germany and the United States. It is believed that the botnet was operated by the APT28 actors in order to obscure their malicious activities, including the exploitation of CVE-2023-23397 against specific targets.
A report published this week by the cybersecurity firm Trend Micro details the origins of a third-party criminal proxy botnet, which was established in 2016. In addition to Ubiquiti routers, the botnet comprises Raspberry Pi, virtual private servers (VPS), and Linux-based routers.
“A portion of the EdgeRouter bots were transferred by the threat actor [behind the botnet] from the C&C [command-and-control] server that was shut down on January 26, 2024, to a newly established C&C infrastructure in early February 2024,” the company stated, adding that legal and technical obstacles prevented a comprehensive cleanup of all compromised routers.
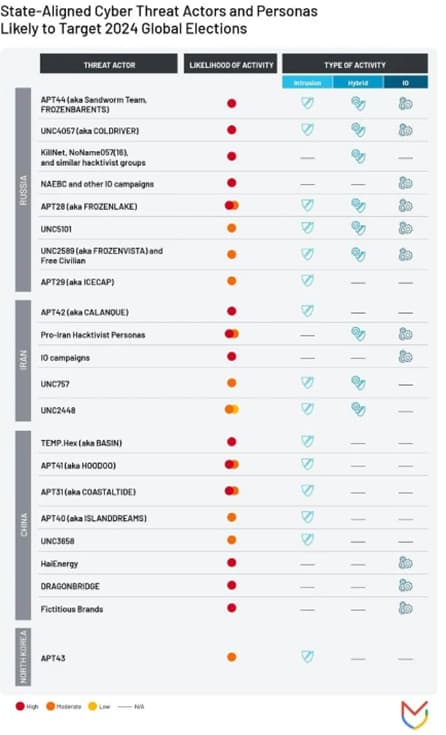
An assessment published last week by Google Cloud subsidiary Mandiant predicts that Russian state-sponsored cyber threat activity, including data theft, destructive attacks, DDoS campaigns, and influence operations, will pose a severe risk to elections in regions such as the United States, the United Kingdom, and the European Union. Multiple groups, including APT44 (also known as Sandworm), COLDRIVER, KillNet, APT29, and APT28, are expected to be responsible for these threats.
“In 2016, GRU-linked APT28 compromised U.S. Democratic Party group targets as well as the private account of the Democratic presidential candidate’s campaign chairman and orchestrated a leak campaign ahead of the 2016 U.S. Presidential election,” investigators Kelli Vanderlee and Jamie Collier reported.
Furthermore, empirical evidence from Cloudflare and NETSCOUT indicates a notable upsurge in Distributed Denial of Service (DDoS) assaults directed at Sweden subsequent to its NATO membership acceptance, a trend that echoes the trends identified during Finland’s NATO membership in 2023.

“The probable perpetrators of these attacks encompassed the hacker groups NoName057, Anonymous Sudan, Russian Cyber Army Team, and KillNet,” NETSCOUT reported. “All these groups are politically motivated, supporting Russian ideals.”

The developments occurred after government agencies from Canada, the United Kingdom, and the United States published a new joint fact sheet to assist critical infrastructure organizations in securing industrial control systems (ICS) and small-scale operational technology (OT) systems against continued attacks launched by ostensibly pro-Russian hacktivists since 2022.
“The pro-Russia hacktivist behavior comes primarily restricted to unsophisticated methods that manipulate ICS equipment to create nuisance effects,” the government agencies reported. “However, studies have shown that these individuals have the ability of tactics which present physical threats against vulnerable and misconfigured OT settings.”

The entities that fall prey to these assaults consist of institutions operating in critical infrastructure sectors across North America and Europe. These sectors encompass water and wastewater systems, dams, energy, and food and agriculture.
It has been observed that hacktivist organizations exploit publicly accessible internet-facing connections and factory default passwords linked to human-machine interfaces (HMIs) that are commonly found in these environments in order to obtain remote access. Subsequently, they manipulate mission-critical parameters, deactivate alarm mechanisms, and restrict operator access by altering administrative passwords.
Hardening human-machine interfaces, restricting the exposure of OT systems to the internet, employing strong and unique passwords, and implementing multi-factor authentication for all OT network access are all recommended measures to mitigate the threat.

“These hacktivists are interested in harming modular, internet-exposed industrial control systems, or ICS, through their software elements, like human-machine interfaces (HMIs), by leveraging virtual network computing (VNC) remote access software and default passwords,” the notification stated.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE






