Active Directory for Hackers | Pentesting Guide | Ethical Hackling in Delhi

Active Directory for Hackers | Pentesting Guide | Ethical Hackling in Delhi
Active Directory Attacks: Techniques, Tools, and Methods for Hackers
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is widely used in enterprise environments to manage users, computers, and other resources. Due to its critical role in managing access and authentication, AD is a prime target for attackers seeking to gain unauthorized access to an organization’s network. This article explores the various types of attacks on Active Directory, the tools used by hackers, and the methods employed to exploit vulnerabilities.
Understanding Active Directory
Before diving into the attacks, it’s essential to understand what Active Directory is and how it works. Active Directory stores information about objects on the network, such as user accounts, groups, computers, and permissions. This information is organized into a hierarchical structure, making it easy to manage and secure resources.
AD operates using the following components:
- Domain Controllers (DCs): Servers that respond to authentication requests and store the AD database.
- Kerberos Authentication: The default authentication protocol in AD, which uses tickets to grant access to resources.
- Group Policy: A feature that controls the environment of user accounts and computer accounts.
- LDAP (Lightweight Directory Access Protocol): A protocol used to query and modify items in AD.
Types of Attacks on Active Directory
Active Directory is vulnerable to a wide range of attacks. Below are some of the most common types:
- Credential Harvesting
Credential harvesting involves obtaining usernames and passwords from an AD environment. Attackers can use various methods to capture these credentials, which are then used to gain unauthorized access to the network.
Tools and Techniques:
- Mimikatz: A popular tool for extracting plaintext passwords, hashes, PINs, and Kerberos tickets from memory.
- Credential Dumping: Attackers dump credentials from memory using tools like Mimikatz or Windows Credential Editor.
- Phishing: Attackers send emails with malicious attachments or links to capture user credentials.
Example:
Attackers can use Mimikatz to dump credentials from the LSASS (Local Security Authority Subsystem Service) process:
| privilege::debug sekurlsa::logonpasswords |
- Pass-the-Hash (PtH) Attack
In a Pass-the-Hash attack, an attacker uses a hashed version of a password instead of the plaintext password to authenticate to the network. This allows attackers to move laterally across the network without needing to crack the password.
Tools and Techniques:
- Mimikatz: Extracts NTLM hashes from memory.
- Pass-the-Hash Toolkit: A collection of tools to perform PtH attacks.
- Psexec: A tool from the Sysinternals suite used to execute processes on remote systems, often used in conjunction with PtH.
Example:
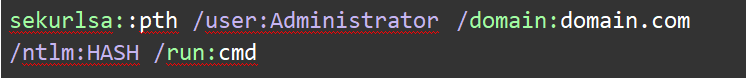
Using Mimikatz to perform a Pass-the-Hash attack:
| sekurlsa::pth /user:Administrator /domain:domain.com /ntlm:HASH /run:cmd |
- Kerberoasting
Kerberoasting is an attack technique where attackers request service tickets for service accounts in AD. These tickets are encrypted with the service account’s password hash, which can be cracked offline to reveal the plaintext password.
Tools and Techniques:
- Rubeus: A tool that can request service tickets and extract them for offline cracking.
- Impacket: A Python library for working with network protocols, including tools for performing Kerberoasting.
- John the Ripper/Hashcat: Password cracking tools used to crack the extracted hashes.
Example:
Using Rubeus to request and dump service tickets:
| Rubeus.exe kerberoast |
- Golden Ticket Attack
A Golden Ticket attack involves creating a forged Kerberos ticket-granting ticket (TGT) that provides unlimited access to any service or resource in the AD environment. This is possible when an attacker gains access to the KRBTGT account’s hash, which is used to sign all TGTs.
Tools and Techniques:
- Mimikatz: Used to create and inject Golden Tickets.
- Impacket: Includes tools to create and manipulate Kerberos tickets.
Example:
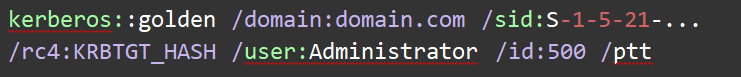
Using Mimikatz to create a Golden Ticket:
powershell
| kerberos::golden /domain:domain.com /sid:S-1-5-21-… /rc4:KRBTGT_HASH /user:Administrator /id:500 /ptt |
- Silver Ticket Attack
A Silver Ticket attack is similar to a Golden Ticket but is more targeted. Instead of forging a TGT, attackers forge a service ticket (TGS) for a specific service. This provides access to a specific service without interacting with the Domain Controller.
Tools and Techniques:
- Mimikatz: Used to create and inject Silver Tickets.
- Impacket: Also supports creating and using Silver Tickets.
Example:
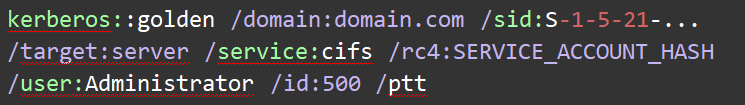
Using Mimikatz to create a Silver Ticket:
| kerberos::golden /domain:domain.com /sid:S-1-5-21-… /target:server /service:cifs /rc4:SERVICE_ACCOUNT_HASH /user:Administrator /id:500 /ptt |
- DCSync Attack
In a DCSync attack, attackers impersonate a Domain Controller and request account password data from another Domain Controller. This attack allows attackers to retrieve password hashes for any account in the domain, including KRBTGT and administrator accounts.
Tools and Techniques:
- Mimikatz: Has a DCSync module that can be used to perform the attack.
- Impacket: Includes tools to simulate Domain Controller synchronization.
Example:
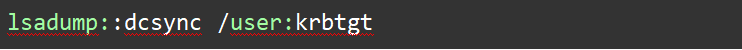
Using Mimikatz to perform a DCSync attack:
| lsadump::dcsync /user:krbtgt |
- Lateral Movement
Lateral movement involves attackers gaining access to one machine or account and using that foothold to move to other systems within the network. This is often done to escalate privileges and gain control over the entire AD environment.
Tools and Techniques:
- BloodHound: A tool for analyzing Active Directory trust relationships to identify attack paths.
- CrackMapExec: A tool for automating the lateral movement and credential validation process.
- PowerShell Empire: A post-exploitation framework that allows for lateral movement and persistence.
Example:
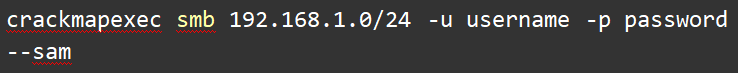
Using CrackMapExec to move laterally within the network:
bash
| crackmapexec smb 192.168.1.0/24 -u username -p password –sam |
Tools Used by Hackers for Active Directory Attacks
Hackers utilize a variety of tools to perform these attacks. Below are some of the most commonly used tools:
- Mimikatz: A powerful tool for extracting passwords, hashes, PINs, and Kerberos tickets from memory. It’s commonly used for credential dumping, Pass-the-Hash attacks, and Golden Ticket attacks.
- BloodHound: A tool that uses graph theory to reveal hidden and often unintended relationships within an AD environment. It’s used to identify attack paths and high-value targets.
- Impacket: A collection of Python classes for working with network protocols. Impacket includes tools for Kerberoasting, DCSync, and other attacks.
- Rubeus: A tool that focuses on Kerberos-related attacks, including Kerberoasting and forging tickets. It’s part of the SharpCollection of offensive tools.
- CrackMapExec: A post-exploitation tool used for automating the process of assessing the security of large Active Directory networks. It can perform lateral movement, credential validation, and more.
- Responder: A tool used to capture and manipulate network traffic. It’s commonly used for capturing NTLM hashes via LLMNR (Link-Local Multicast Name Resolution) poisoning.
- PowerShell Empire: A post-exploitation framework that allows for a wide range of attacks, including lateral movement, persistence, and data exfiltration.
- John the Ripper/Hashcat: Password cracking tools used to crack password hashes obtained during attacks like Kerberoasting or credential dumping.
Conclusion
Active Directory is a cornerstone of enterprise IT infrastructure, making it a prime target for attackers. Understanding the types of attacks that can be carried out against AD, the tools used, and the methods employed is crucial for defending against these threats.
Organizations must implement strong security practices, such as using multi-factor authentication, regularly auditing AD configurations, and monitoring for unusual activity, to protect against these attacks. By staying informed about the latest attack techniques and leveraging defensive tools, organizations can better secure their Active Directory environments and prevent attackers from gaining a foothold in their networks.
READ MORE ARTICLE HERE