A Python Backdoor is Employed in a Zero-Day Attack on Palo Alto Networks.

A Python Backdoor is Employed in a Zero-Day Attack on Palo Alto Networks.
Since March 26, 2024, threat actors have been capitalizing on the recently exposed zero-day vulnerability in the PAN-OS software of Palo Alto Networks, approximately three weeks prior to its revelation yesterday.

Unknown in origin, the Unit 42 division of the network security corporation is monitoring the activities under the name Operation MidnightEclipse and attributes it to a single threat actor.
The identified security vulnerability is a command injection defect (CVE-2024-3400; CVSS score: 10.0). It grants root privileges to the firewall to unauthenticated attackers, allowing them to execute arbitrary code.

Notably, the issue only affects firewall configurations running PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 with GlobalProtect gateway and device telemetry enabled.
Operation MidnightEclipse involves the utilization of the vulnerability to establish a cron job that retrieves commands from an external server at minute intervals (“172.233.228[.]93/policy” or “172.233.228[.]93/patch”). These commands are subsequently executed via the bash terminal.
It has been reported that the assailants managed an access control list (ACL) for the command-and-control (C2) server manually in order to restrict access to the device that is in communication with it.

Although the precise functionality of the command remains undisclosed, it is hypothesized that the URL functions as a conduit for a Python-based backdoor on the firewall that is hosted on a separate server and is tracked by Volexity (which realized an in-the-wild exploit of CVE-2024-3400 on April 10, 2024 under the alias UPSTYLE; “144.172.79[.]92” and “nhdata.s3-us-west-2.amazonaws[.]com”).
The Python file is specifically engineered to generate and execute an additional Python script (“system.pth”), which decodes and executes the embedded backdoor component. This backdoor component executes the commands provided by the threat actor and is documented in a file named “sslvpn_ngx_error.log.” The outcome of the operation is appended to an independent file with the name “bootstrap.min.css.”
The most intriguing element of the attack chain is that both the files utilized for command extraction and result writing are authentic files that are affiliated with the firewall:
- /var/log/pan/sslvpn_ngx_error.log
- /var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css
Concerning how the commands are appended to the error log of the web server, the threat actor fabricates network requests that are specifically designed to reach a non-existent webpage that incorporates a designated pattern. The backdoor subsequently examines the log file for the line that matches the specified regular expression (“img[([a-zA-Z0-9+/=]+))”) in order to decode it and execute the command contained within it.

“The script will subsequently establish an additional thread that runs a function called restore,” according to Unit 42. “The restore function uses the initial structure of the bootstrap.min.css file, as well as the initial access and modified times, sleeps for 15 seconds,writes the initial data restored to the file, and resets the access and updated times to their originals.”
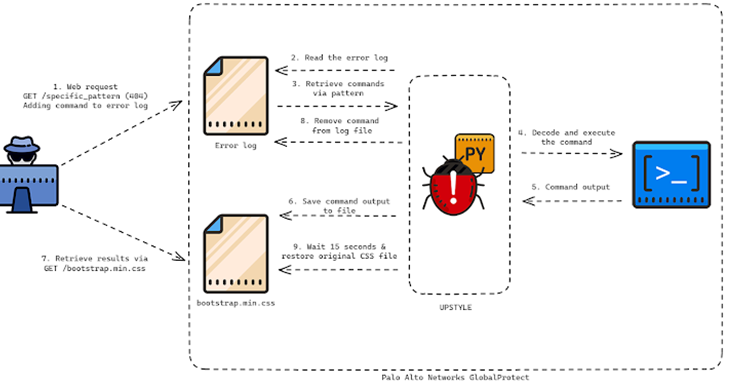
The primary objective seems to be preventing any remnants of the command outputs, which requires the results to be exfiltrated within a time constraint of 15 seconds prior to the overwriting of the file.
Volexity stated in its analysis that it witnessed the threat actor construct a reverse shell, download additional tools, pivot into internal networks, and ultimately exfiltrate data by remotely exploiting the firewall. Current information regarding the campaign’s magnitude is scarce. The company has designated the adversary with the designation UTA0218.
“The tradecraft and speed utilized by the intruder indicates an extremely skilled threat actor with a clear blueprint of what they can use to advance their objectives,” the cybersecurity company in the United States reported.
“The initial goals of UTA0218 were to acquire the DPAPI keys for the domain backup and to target Active Directory credentials through the acquisition of the NTDS.DIT file. Additionally, they focused on user workstations in an effort to pilfer saved cookies, login information, and DPAPI credentials.”
Internal Palo Alto Networks GlobalProtect firewall devices are advised to be monitored for indications of lateral movement by organizations.

The vulnerability has also been included in the Known Exploited Vulnerabilities (KEV) catalog of the U.S. Cybersecurity and Infrastructure Security Agency (CISA), necessitating that federal agencies deploy the necessary upgrades by April 19 in order to mitigate potential threats. By April 14, Palo Alto Networks is anticipated to release patches for the vulnerability.
“Concentrating on edge devices maintains an effective vector of assault for capable threat actors who have sufficient time and resources to invest into investigating new vulnerabilities,” according to Volexity.

“It is highly probable that UTA0218 is a state-backed threat actor considering the resources necessary to develop and leverage a flaw of this nature, the sort of victims targeted by this actor, and the abilities demonstrated to install the Python backdoor and to further access victim networks.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE





