DISGOMOJI Malware is Employed by Pakistani Hackers in Indian Government Cyber Attacks
DISGOMOJI Malware is Employed by Pakistani Hackers in Indian Government Cyber Attacks
In 2024, a cyber espionage operation aimed at Indian government organizations was connected to a suspected threat actor with a base in Pakistan.

Under the codename UTA0137, cybersecurity firm Volexity is monitoring the activity and pointing out that the attacker is only using DISGOMOJI, a Golang-written malware intended to infect Linux systems.

“It is a modified version of the public project Discord-C2 which uses emojis for its C2 communication and the messaging service Discord for command and control (C2),” the statement read.
Notably, DISGOMOJI is the same “all-in-one” espionage tool that BlackBerry claimed to have found during an infrastructure examination in relation to an attack operation carried out by the Transparent Tribe actor, a Pakistani hacking group.
Spear-phishing emails containing a Golang ELF binary sent in a ZIP archive file start the attack chains. The DISGOMOJI payload is then covertly downloaded by the program from a remote site together with an innocuous lure document.

A bespoke version of Discord-C2, DISGOMOJI is made to run commands from an attacker-controlled Discord server and record host information. The commands are delivered in an intriguing twist as various emojis:
- 🏃♂️ – Execute a command on the victim’s device
- 📸 – Capture a screenshot of the victim’s screen
- 👇 – Upload a file from the victim’s device to the channel
- 👈 – Upload a file from the victim’s device to transfer[.]sh
- ☝️ – Download a file to the victim’s device
- 👉 – Download a file hosted on oshi[.]at to the victim’s device
- 🔥 – Find and exfiltrate files matching the following extensions: CSV, DOC, ISO, JPG, ODP, ODS, ODT, PDF, PPT, RAR, SQL, TAR, XLS, and ZIP
- 🦊 – Gather all Mozilla Firefox profiles on the victim’s device into a ZIP archive
- 💀 – Terminate the malware process on the victim’s device

“Every channel in the Discord server represents a unique victim because the malware creates a dedicated channel for itself,” Volexity stated. “The attacker can then use these channels to engage with every victim individually.”
The company claimed to have discovered several DISGOMOJI versions that could create persistence, stop multiple DISGOMOJI processes from running at once, dynamically retrieve the credentials to connect to the Discord server at runtime instead of hard coding them and discourage analysis by showing false informational and error messages.

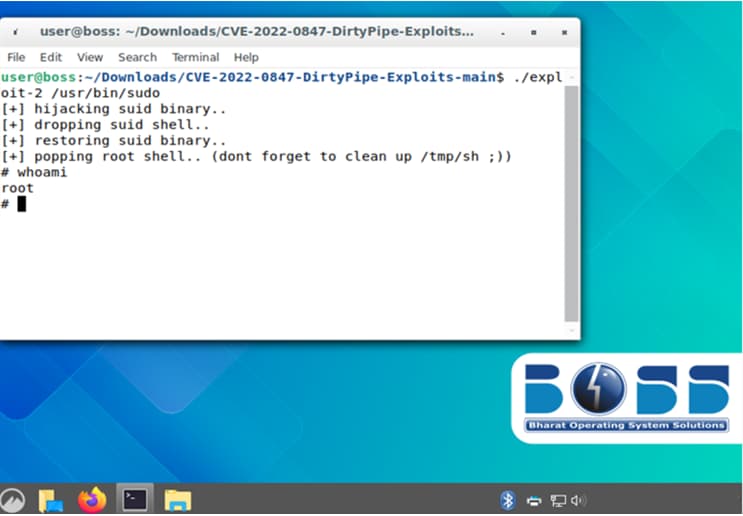
As for network scanning and tunneling, UTA0137 has also been seen using legal and open-source tools like Nmap, Chisel, and Ligolo; one recent campaign has even been seen taking advantage of the DirtyPipe vulnerability (CVE-2022-0847) to acquire privilege escalation against Linux machines.

A further post-exploitation strategy is to use the Zenity tool to show a dangerous dialog box that looks like a Firefox update in an attempt to socially engineer people into disclosing their credentials.
“With their Golang malware, DISGOMOJI, the attacker successfully managed to infect a number of victims,” Volexity stated. UTA0137 has over time enhanced DISGOMOJI.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE