Microsoft Issues Warning Regarding Increased Cyberattacks on Internet-Exposed OT Devices
Microsoft Issues Warning Regarding Increased Cyberattacks on Internet-Exposed OT Devices
Microsoft has underscored the necessity of safeguarding operational technology (OT) devices that are exposed to the internet in response to a series of cyber assaults that have targeted these environments since late 2023.

The Microsoft Threat Intelligence team emphasized the urgent necessity of enhancing the security posture of OT devices and preventing critical systems from becoming simple targets as a result of these repeated attacks.
The company observed that a cyber attack on an OT system could enable malicious actors to manipulate critical parameters utilized in industrial processes, either programmatically through the programmable logic controller (PLC) or through the graphical controls of the human-machine interface (HMI). This could lead to system outages and malfunctions.

It also stated that OT systems frequently lack sufficient security mechanisms, rendering them susceptible to exploitation by adversaries and the execution of attacks that are “relatively simple to execute.” This issue is further exacerbated by the additional hazards posed by directly connecting OT devices to the internet.
This not only renders the devices discoverable by attackers through internet scanning tools but also allows them to be weaponized to obtain initial access by exploiting weak sign-in passwords or outdated software with recognized weaknesses.
In response to “heightened geopolitical tensions and adversarial cyber activity globally,” Rockwell Automation issued an advisory last week, advising its customers to disconnect all industrial control systems (ICSs) that are not intended for public internet access.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also issued a bulletin regarding pro-Russian hacktivists who intend to attack vulnerable industrial control systems in North America and Europe.
“Particularly, pro-Russia hacktivists manipulated HMIs, leading water pumps and blower tools to operate above their normal operating parameters,” according to the organization. “In every instance, the hacktivists maxed out set parameters, altered other configurations, turned off alarm mechanisms, and changed administrative passwords to lock out the WWS operators.”

Moreover, Microsoft reported that the Israel-Hamas war, which began in October 2023, resulted in a significant increase in cyber attacks against internet-exposed, poorly secured OT assets developed by Israeli companies. The majority of these attacks were conducted by groups such as Cyber Av3ngers, Soldiers of Solomon, and Abnaa Al-Saada, which are affiliated with Iran.

According to Redmond, the attacks targeted OT equipment that was deployed in various sectors of Israel and was manufactured by international vendors, as well as equipment that was sourced from Israel but was deployed in other countries.
The tech titan further stated that these OT devices are “primarily internet-exposed OT systems with a poor security posture, potentially accompanied by weak passwords and known vulnerabilities.”
In order to mitigate the risks associated with these threats, it is advised that organizations implement zero-trust practices and reduce the attack surface in their OT systems. This will prevent attackers from advancing laterally within a compromised network.

The development occurs in the wake of the unpacking of a destructive malware strain known as Fuxnet by OT security firm Claroty. The Blackjack hacking group, which is suspected to be supported by Ukraine, is purportedly responsible for using this strain against Moscollector, a Russian company that operates a vast network of sensors to monitor Moscow’s underground water and sewage systems for emergency detection and response.
BlackJack, which disclosed the attack’s specifics early last month, characterized Fuxnet as “Stuxnet on steroids.” Claroty observed that the malware was likely disseminated remotely to the target sensor gateways via protocols such as SSH or the sensor protocol (SBK) over port 4321.
Fuxnet has the ability to permanently destroy the filesystem, prevent access to the device, and physically damage the NAND memory chips on the device by repeatedly writing and rewriting the memory to render it inoperable.
Additionally, it is intended to rewrite the UBI volume in order to prevent the sensor from rebooting and ultimately corrupt the sensors by sending a torrent of bogus Meter-Bus (M-Bus) messages.
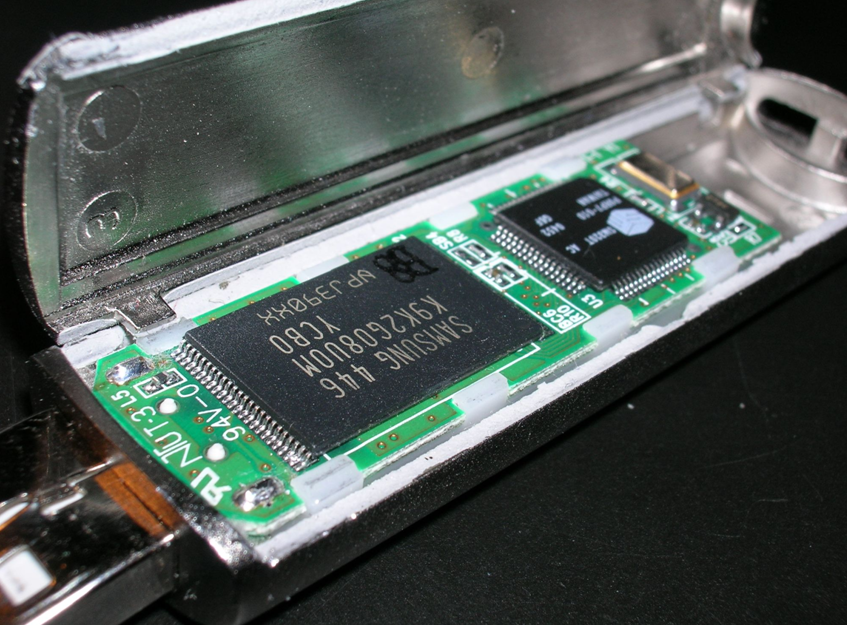
“The criminals created and spread malicious software that aimed the gateways and deleted filesystems, directories, disabled remote access services, routing services for each device, and rewrote flash memory, destroyed NAND memory chips, UBI volumes and other actions that further disrupted operation of these gateways,” according to Claroty.
In the first quarter of 2024, the internet, email clients, and removable storage devices were the primary sources of threats to computers in a company’s OT infrastructure, as per data released by the Russian cybersecurity company Kaspersky earlier this week.

“Malicious actors use scripts for a wide range of objectives: collecting information, tracking, redirecting the browser to a malicious site, and uploading various types of malware (spyware and/or silent crypto mining tools) to the user’s system or browser,” according to the report. “These spread via the internet and email.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE HERE





