Famous Android Apps Xiaomi and WPS Office are Vulnerable To File Overwrite Vulnerability.

Famous Android Apps Xiaomi and WPS Office are Vulnerable To File Overwrite Vulnerability.
A number of widely used Android applications that can be found in the Google Play Store are prone to a path traversal-related flaw known as the Dirty Stream attack. A malevolent app could exploit this vulnerability to overwrite arbitrary files in the home directory of the vulnerable app.

“Based on the implementation of an application, this vulnerability pattern may result in token theft and arbitrary code execution,” Dimitrios Valsamaras of the Microsoft Threat Intelligence team wrote in a report published on Wednesday.
An attacker could gain complete control of the application’s behavior and use the compromised credentials to gain unauthorized access to the victim’s online accounts and other data if exploitation is successful.

Two applications that were identified as susceptible to the issue are as follows:
| Xiaomi File Manager (com.mi. Android.globalFileexplorer) | Over 1 billion installs |
| WPS Office (cn.wps.moffice_eng) | Over 500 million installs |
In addition to implementing isolation by allocating dedicated memory and data space to each application, Android provides a content provider to enable secure file and data sharing between applications. However, oversights in implementation may allow read/write restrictions in the home directory of an application to be circumvented.
“This content provider-based architecture gives users a clear file-sharing process, allowing a serving app to exchange its files with other apps in an encrypted way with fine-grained control,” said Valsamaras.
“However, we frequently come across instances in which the consuming application does not confirm the content of the file that it receives and, most concerning, it employs the filename given by the serving app to cache the obtained file within the consuming app’s internal data directory.”
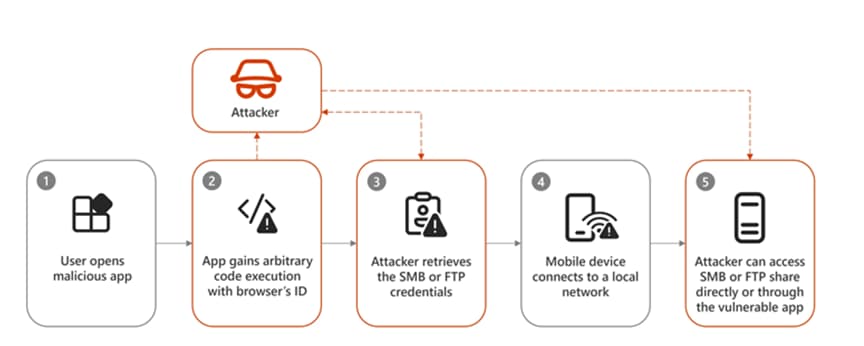
When a serving application declares a malicious version of the FileProvider class to facilitate file sharing between apps, this pitfall can result in severe repercussions, including the overwriting of critical files in the private data space of the consuming application.
In other words, code execution results from the mechanism capitalizing on the consuming application’s naive trust in the input in order to transmit arbitrary payloads bearing a particular filename using a custom, explicit intent and without the user’s knowledge or consent.

Consequently, this could enable a malicious actor to modify the shared preferences file of the targeted application and force it to establish a connection with a server under its command in order to extract confidential data.
Conversely, if applications load native libraries from their own data directory (rather than “/data/app-lib”), a malicious application could exploit the aforementioned flaw to inject malicious code into a native library, which would be executed when the library is loaded.

As of February 2024, both Xiaomi and the WPS Office have resolved the matter subsequent to the conscientious disclosure. However, Microsoft stated that the problem might be more widespread and mandated that developers take precautions to scan their applications for similar flaws.
Furthermore, Google has issued official guidance regarding this subject, advising developers to manage the filename supplied by the server application in an appropriate manner.
“When the client app writes the newly acquired file to storage, it should ignore the filename given by the server app and instead utilize its own internally produced unique identifier as the filename,” the search giant stated. “If creating a unique filename is not practical, the client app ought to sanitize the provided filename.”
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
READ MORE ARTICLE HERE