Gobuster Full Tutorial Step by Step
Gobuster Full Tutorial Step by Step
Gobuster is a popular command-line tool used for directory and file brute-forcing on web servers. It is written in Go programming language and is widely used by penetration testers and security professionals for enumerating directories and files on web servers to discover hidden resources or potential points of vulnerability.
Key features of Gobuster include:
- Directory and file brute-forcing: Gobuster sends HTTP requests to the target web server with different directory and file names to discover hidden or unlinked resources.
- Customizable wordlists: Users can specify their own wordlists containing directory or file names to be used in the brute-forcing process.
- Concurrent requests: Gobuster allows for multiple concurrent requests to speed up the scanning process.
- Recursive mode: Gobuster can be set to recursively search directories, enabling it to discover nested directories and files.
- Extension brute-forcing: It can be configured to brute-force file extensions, which can help identify potentially vulnerable or interesting files.
How To Install the Gobuster ?
- In Linux Distros the gobuster is pre-installed just run it.
[ sudo apt install gobuster ]
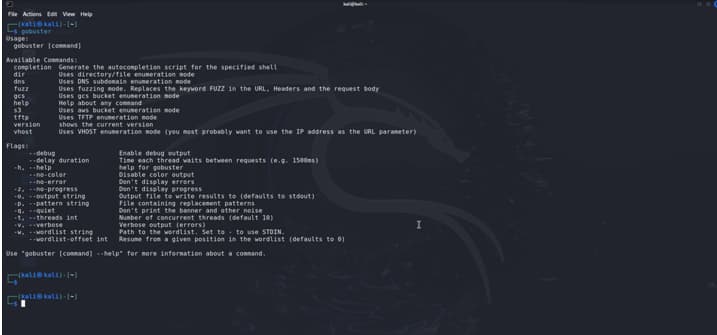
Gobuster Provide Various Commands to Brute-Force
- Dir = Use for Directory enumeration
- Dns = Use for DNS subdomain enumeration mode
- Fuzz = Use fuzzing mode. Replace FUZZ in the URL , Headers and the request
- Gcs = Use gcs bucket enumeration mode
- S3 = Use aws bucket enumeration mode
- Tftp = Use TFtp enumeration mode
- Vhost = Use Vhost enumeration
We Will see the Dir, DNS and Fuzz commands
DIR
Directory/FILE Enumeration Mode
Gobuster use Some flag
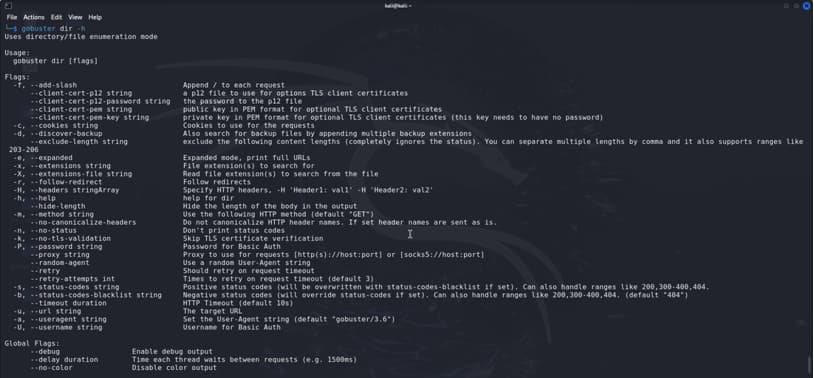
- -u , –url = target url
- -e , –expanded = expanded mode print full urls
- -t ,–threads int =no of concurrent threads
- -w , –wordlist = Path to the wordlist.
- -r ,–follow–redirect = Follow Redirects
Now We Will Test the gobuster with dir mode.
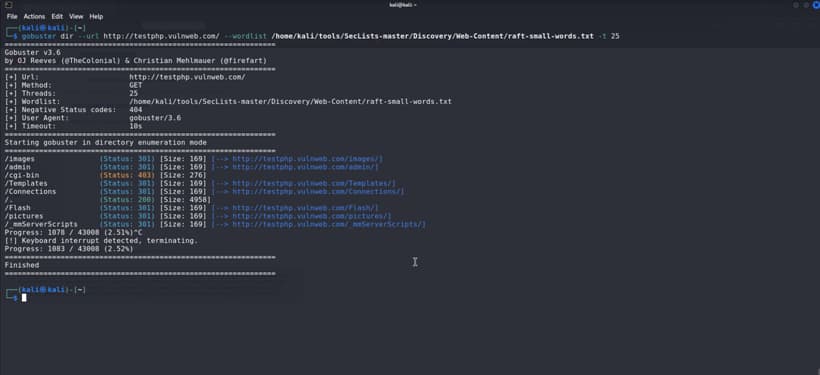
We Have found the admin Directory int the testphp.vulnhub.com using the Gobuster.
DNS
Dns enumeration mode.
Gobuster use flags for dns.
- -d , –domain = The Target Domain
- -c , –show-cname = Show CNAME Records
- -i , –show-ips = Show IP address
- -t , –threads =Number of concurrent threads (default 10)
- -v , –verbose = Verbose Output
- -w, –wordlist string Path to the wordlist.
Now We Will Scan the craw.in With Gobuster dns mode.
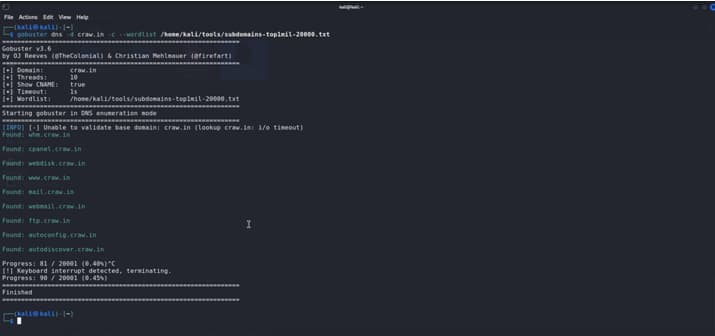
Here We Have Found Few Domains using Gobuster dns mode
FUZZ
“fuzz testing” (or “fuzzing”) is a technique used to discover vulnerabilities in software by providing invalid, unexpected, or random data as input to a computer program
How to fuzz with gobsuster
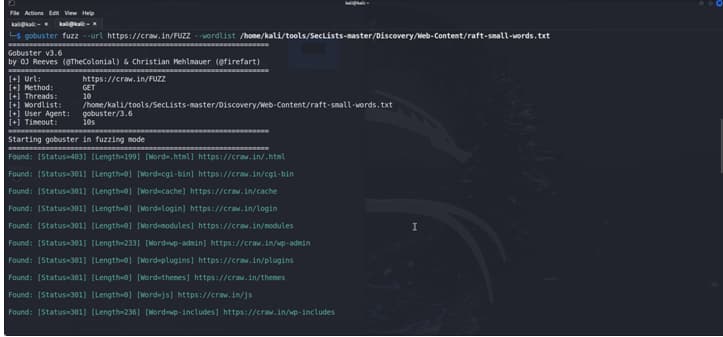
Here We Have found some folder with the fuzz mode with gobuster.
READ MORE ARTICLE HERE