Aircrack-ng – A Globally Famous Cybersecurity Tool

Aircrack-ng – A Globally Famous Cybersecurity Tool
Aircrack-ng is a program designed to crack 802.11 WEP and WPA-PSK keys. It is capable of recovering keys after capturing a sufficient number of data packets.
In comparison to other WEP decryption tools, it executes the standard FMS attack in addition to optimizations such as KoreK attacks and the brand-new PTW attack, which significantly accelerates the attack.
By utilizing these commands, one will have the capability to decrypt Wi-Fi access points that employ WPA/WPA2 encryption via PSK (Pre-Shared Key).
The aim is to intercept the WPA/WPA2 authentication interaction and subsequently employ Aircrack-ng to decrypt the PSK.
Here are the fundamental procedures that will be undertaken:
- Install the latest aircrack-ng.
- Start the wireless interface in monitor mode using airmon-ng.
- Start airodump-ng on the AP channel with a filter for BSSID to collect authentication handshake.
- Use aireplay-ng to deauthenticate the wireless client. (Optional)
- Run aircrack-ng to crack the WPA/WPA2-PSK using the authentication handshake.
How Does It Work?
Start Kali Linux and login, preferably as root.
Step 1:
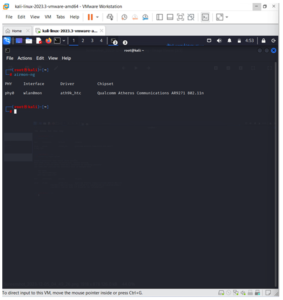
Launch a Terminal, disconnect from all wireless networks, and enter airmon-ng.
All wireless devices that support monitor mode (as opposed to injection mode) will be enumerated. Disconnect and reconnect the adapter (if one is present) and verify that it supports monitor mode if no cards are displayed.
My card allows monitor mode, as evidenced by the fact that it is listed as wlan0.
Step 2:
Enter airmon-ng start subsequently followed by the wireless card’s interface name. The command I would use to activate wlan0 is airmon-ng start wlan0.
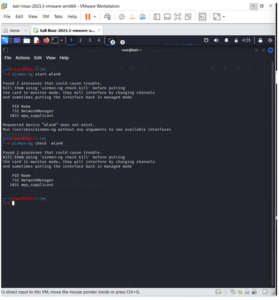
The message “(monitor mode enabled)” indicates that the card has been placed into monitor mode effectively. Take note that the new monitor interface is designated mon0.
Type: Ifconfig [Interface Of Wireless Card] Down And Hit Enter.
Replace [Interface Of Wireless Card] With The Name Of The Interface That You Enabled Mon0 On; Probably Called Wlan0.
By doing so, the wireless card is prevented from establishing an internet connection, thereby enabling it to concentrate on monitor mode.
After you have disabled mon0 (completed the wireless section of the tutorial), you’ll need to enable wlan0 (or name of wireless interface), by typing: ifconfig [interface of wireless card] up and pressing Enter.
STEP 3:
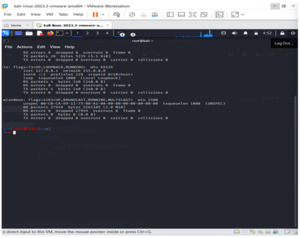
Type airodump-ng followed by the name of the new monitor interface, which is probably mon0.
STEP 4:
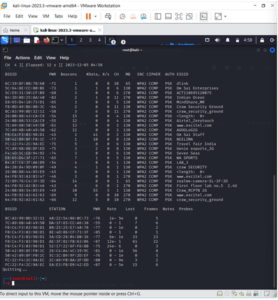
Airodump will now provide a comprehensive list of all nearby wireless networks, including a wealth of relevant information about each one.
Identify the network that you are authorized to conduct a penetration test on or your own.
Once your network appears on the continuously expanding list, press Ctrl + C to terminate the procedure. Take note of the target network’s channel.
STEP 5:
Transfer the BSSID of the intended network
Enter the following command now:
airodump-ng -c [channel] –bssid [bssid] -w /root/Desktop/ [monitor interface]
Now, [channel] should be substituted with the channel of the destination network. Replace [bssid] with the network BSSID and [monitor interface] with the name of the interface that is enabled for monitoring, denoted as mon0.
The directory path and “–w” option specify a location in which airodump will store any intercepted four-way handshakes (which are required to decrypt the password). It was saved to the Desktop in this instance, but it could be saved anywhere.
The format of a comprehensive command should be as follows:
airodump-ng -c 1 –bssid 22:0b:88:54:85:E9 -w /Pictures/abcd/ wlan0mon

Now press enter.
STEP 6:
By restricting Airodump’s monitoring to the target network, we can acquire more precise and detailed information pertaining to it.
At this moment, our true activity consists of patiently awaiting the connection or reconnection of a device to the network, which compels the router to transmit the four-way communication that is critical for password cracking.
Additionally, remember that the handshake will be preserved in four files that should appear on your desktop after it has been captured; do not delete them.
However, we have no intention of waiting for a device to connect; impatient hackers never do that.
A further cool utility from the aircrack suite known as aireplay-ng will be utilized to accelerate the procedure.
By employing this tool, malicious actors can coerce a device into reconnecting with the network by transmitting deauthentication (deauth) packets to one of the devices comprising the network. This causes the device to believe it is obligated to reconnect.
Someone else must be connected to the network before this utility can function; therefore, observe the airodumping and wait for a client to appear. It could be an instantaneous moment or an extended period of time before the initial one appears.
If no one appears after an extended period of waiting, the network may be vacant at the moment or you may be too far away from it.
Next Step:
STEP 7:
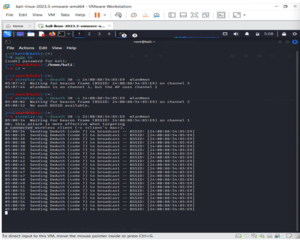
While airodump-ng remains operating, access a second terminal. Put the following command into this terminal:
aireplay-ng –0 2 –a [router bssid] –c [client bssid] mon0
The –0 is a shortcut for the deauth mode
2 is the number of deauth packets to send.
-a indicates the access point/router’s BSSID
-c indicates the client’s BSSID
mon0 merely means the monitor interface
My complete command looks like this:
aireplay-ng –deauth 20 –a 22:0b:88:54:85:E9 wlan0mon
STEP 8:
When you press Enter, aireplay-ng will begin transmitting the packets.
Should the deauthentication process succeed and you were in close proximity to the target client, the following message will manifest on the airodump screen that you intentionally left unattended:
This indicates that the handshake has been intercepted and the intruder now possesses the password in some capacity.
To cease network monitoring, press Ctrl + C on the airodump-ng terminal and close the aireplay-ng terminal. However, retain the airodump-ng terminal just in case you require some of the information in the future.
STEP 9:
This brings the external portion of this tutorial to a close.
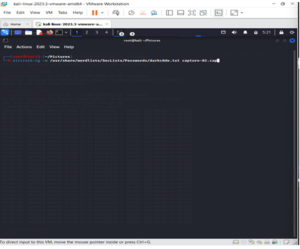
In a new Terminal, enter the following command:
aircrack-ng -a2 -bssid [router bssid] -w [path to wordlist] /root/Desktop/*.cap
-a is the method aircrack will use to crack the handshake.
-b stands for bssid, replace [router bssid] with the BSSID of the target router
-w stands for wordlist
/root/Desktop/*.cap is the path to the .cap file containing the password.
STEP 10:
At this moment, Aircrack-ng will initiate the password-cracking procedure.
You can decipher it if the password appears in the specified wordlist. Occasionally, it is not.
If this is the case, alternative wordlists may be attempted.
It appears that the penetration test has failed if the password remains undiscovered despite attempting numerous wordlists; the network is therefore at least impervious to basic brute-force attacks.
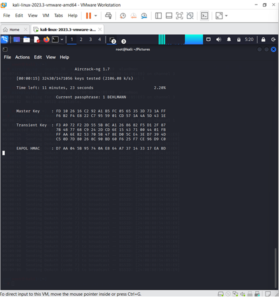
If the phrase is present in the wordlist, aircrack-ng will display it as follows:
The passphrase for our test network was “notsecure,” which aircrack discovered as evidenced by the fact that it appeared in the wordlist.
If you can deduce the password with minimal effort, you should modify your password if the network in question is yours. When conducting penetration testing on behalf of an individual, advise them to promptly update their password.
How News4Hackers Can Help?
News4Hackers is an organization that provides cybersecurity news and informative articles of international caliber. In addition, News4Hackers is committed to providing our readers with up-to-date information on the most recent developments, methodologies, technologies, and cyber assaults targeting enterprises globally. Our news collectors remain vigilant for the most recent technological developments around the clock, every day of the week, in order to promptly deliver them to you.
Additionally, Craw Security is affiliated with News4Hackers, an authoritative resource on cybersecurity that provides insights into numerous prominent nations, including India. Contact them at +91-9513805401 for any inquiries regarding the commencement dates of their most effective cybersecurity training courses or any other matter pertaining to cybersecurity.
READ MORE ARTICLE HERE