Conquering the Difficulties of Kubernetes Security in Cloud Native Apps

Conquering the Difficulties of Kubernetes Security in Cloud Native Apps
Cloud-native applications have emerged as a transformational force within the dynamic field of information technology. Due to its exceptional scalability and versatile development and deployment capabilities, the use of cloud computing has emerged as a natural step for enterprises across all sectors and of varying sizes. Nevertheless, the earliest forays into cloud computing often resembled the preexisting infrastructure, as they relied on “lift and shift” migrations. However, it became evident that this approach was not economically viable nor efficient for executing workloads.
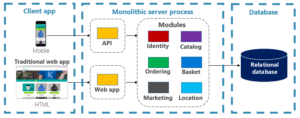
In response to this difficulty, the development of technologies such as Kubernetes has emerged, marking the advent of a novel era in the administration of cloud infrastructure. The transition from long-lasting systems to transient containers occurred, and the principle of considering systems as “cattle, not pets” became widely adopted within the DevOps community. The nature of servers has evolved from individually designed and customized systems with long lifespans to a more dynamic approach that involves automated scaling and provisioning in response to varying workload demands. The field of management has seen a transformation in its emphasis, shifting towards a more abstract level of analysis and consideration of the resources at hand.
Notwithstanding these technological breakthroughs, security measures in contemporary cloud-native systems frequently adhered to outdated approaches. Similar to how the “lift and shift” technique was shown to be insufficient for migrating to the cloud, it has been observed that old security practices are not well-suited for effectively protecting current application deployment methods.
The complexity around Kubernetes security arises due to various factors. The process of abstracting a resource, which facilitates its management by a certain team, inevitably presents novel issues for another team. The transition from physical servers to virtual machines and later to containers has necessitated the inclusion of security considerations at several levels, encompassing service-to-service communication as well as cluster-wide regulations.
The process of managing security across these several layers is complex and challenging. The process encompasses several aspects such as authentication, authorization, secret and security certificate management, traffic flow control and security, and anomaly monitoring, all while guaranteeing adherence to legislative, industry, and customer audit standards. Traditional security procedures continue to hold significance in the realm of cybersecurity. These practices include software patching, the implementation of least-privileged access, and the fortification of perimeters to prevent unauthorized entry.
In response to the intricate and multifaceted nature of potential threats, some companies have embraced a strategic approach commonly referred to as “defense in depth.” This entails the implementation of numerous layers of security measures in order to impede the progress of attackers and mitigate potential harm in the event of a security breach. The principle of defense in depth is enhanced by the notion of “zero trust security,” which questions the presumption of confidence and necessitates authentication for all forms of communication.
Nevertheless, the implementation of defense in depth can incur significant costs and consume a considerable amount of time, frequently necessitating the utilization of diverse systems that may lack adequate communication capabilities. The potential for creating vulnerabilities that malicious actors can exploit is a legitimate fear.
The previous solutions; however, characterized by their superior quality, were designed in reaction to identified or anticipated risks. They demonstrate proficiency in preserving traditional structures such as virtual machines and network perimeters, although they exhibit limitations in ensuring the security of contemporary, decentralized, finely divided, cloud-native applications. The efficacy of contemporary security tools in efficiently sharing information is frequently inadequate, hence hindering the implementation of a comprehensive defense-in-depth plan.
In order to streamline the security measures of Kubernetes, businesses have the option to implement a number of recommended practices:
- It is advisable to conduct periodic assessments of container images in order to identify potential risks.
- It is advisable to refrain from executing processes with root rights or allocating excessive privileges.
- The notion of least-privileged access should be implemented.
- Ensuring the security of inter-pod and inter-service communications.
- Adopting a zero-trust security approach entails the implementation of mutual transport layer security (mTLS).
- In order to establish a comprehensive secrets management plan, it is imperative to develop a rigorous approach.
- The implementation of security measures as a policy is essential in order to effectively respond to evolving requirements.
- It is imperative to emphasize the significance of observability, rather than solely focusing on measurements.
Managing the ingress and egress of traffic into applications is an essential component of ensuring security inside the Kubernetes framework. The presence of malevolent or dysfunctional upstream applications has the potential to inundate networks, hence requiring the implementation of an enterprise-level API gateway that offers rate-limiting, authentication, authorization, and advanced networking security features.
All in all, the task of ensuring the security of applications based on Kubernetes presents a formidable challenge; however, it is not an insurmountable obstacle. The keys to achieving success in securing a dynamic environment lie in implementing a layered security approach, adopting a zero-trust philosophy, and utilizing a contemporary security solution that offers comprehensive visibility and control.
About The Author:
Yogesh Naager is a content marketer who specializes in the cybersecurity and B2B space. Besides writing for the News4Hackers blog, he’s also written for brands including CollegeDunia, Utsav Fashion, and NASSCOM. Naager entered the field of content in an unusual way. He began his career as an insurance sales executive, where he developed an interest in simplifying difficult concepts. He also combines this interest with a love of narrative, which makes him a good writer in the cybersecurity field. In the bottom line, he frequently writes for Craw Security.
Read More Article Here
Wiretapping of an XMPP-based chat service has been uncovered by researchers.
N. The Lazarus Group from Korea Uses Known Flaws to Target Software Vendor
How to Keep Your Business A float in a Tense Situation?